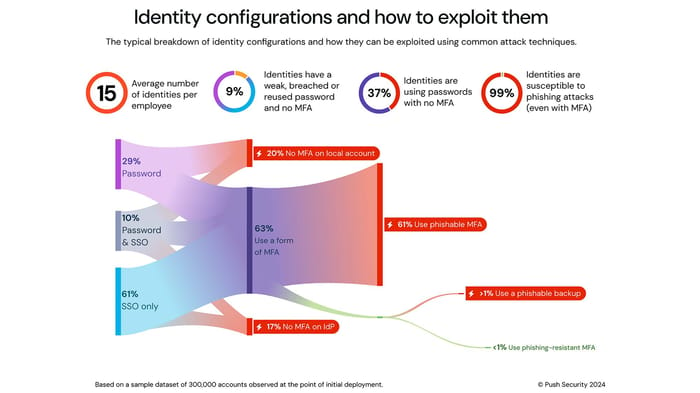
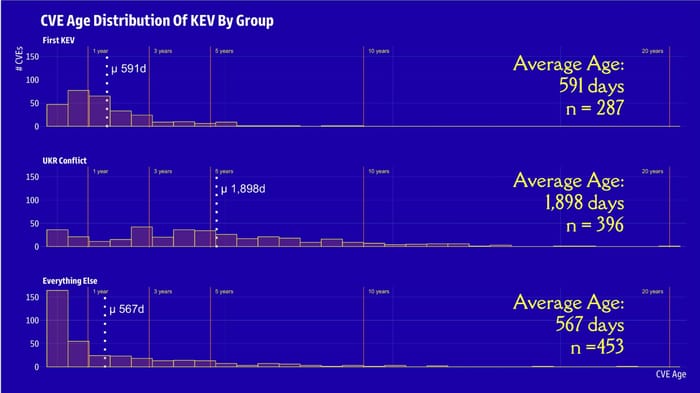
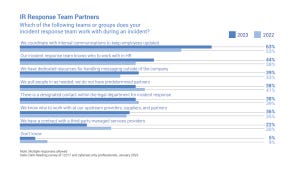
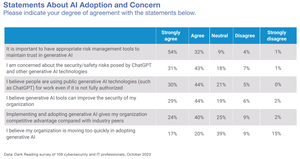
Featured on The Edge Threat Monitor
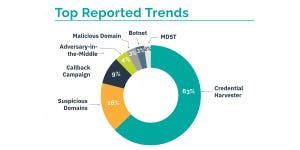
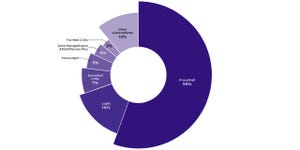
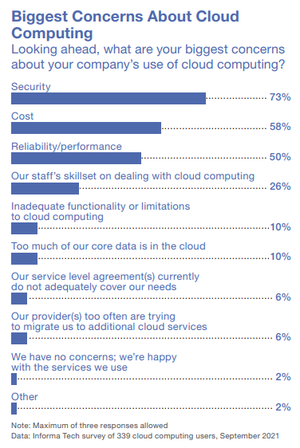
Figure 12, Initial Attack Vectors 
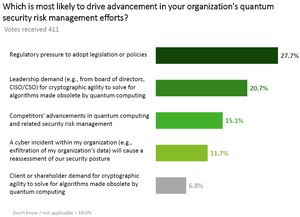
ICS/OT Security
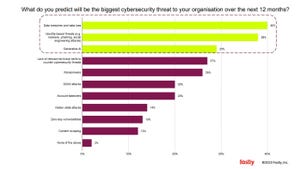
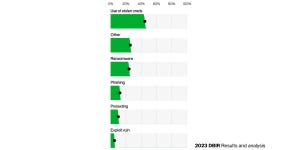
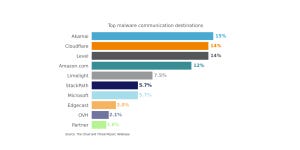
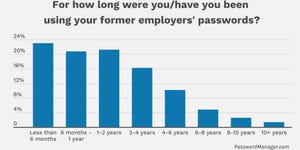
Attackers Breach IT-Based Networks Before Jumping to ICS/OT SystemsAttackers Breach IT-Based Networks Before Jumping to ICS/OT Systems
SANS's "2024 State of ICS.OT Cybersecurity report" highlights the most common types of attack vectors used against ICT/OT networks.
More from The Edge Threat Monitor
Keep up with the latest cybersecurity threats, newly discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or weekly right to your email inbox.