
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
Credential Harvesting Is Retail Industry's Top Threat
Why bother with new tactics and exploits when the old tricks are still effective?

Cybercriminals targeting the retail and hospitality industry are sticking to tried and tested threat vectors, such as credential harvesting and phishing, according to analysis by the Retail & Hospitality Information Sharing and Analysis Center (RH-ISAC).
An ISAC is an industry-specific organization that acts as a centralized repository of information on threats affecting a specific industry sector. Member organizations share threat intelligence and mitigation information, with the idea that organizations can prepare their defenses better if they know the kinds of attacks their peers are experiencing.
The "RH-ISAC Intelligence Trends Summary," which encompasses information shared by member organizations from May to August, highlights shifts in the threat landscape for the retail, hospitality, and travel sectors. Credential harvesting was "by far the most prevalent reported threat," at 63%, according to the report. Suspicious domains were the second most prevalent, at 16%. Other threat indicators reported by members include malicious domains (3%), botnets (3%), and adversary-in-the-middle attacks (4%).
Ten malware families made up 81% of total reports the RH-ISAC tracked during the four-month period, of which Emotet was the most prevalent. While it's possible that the rise in Emotet-related reports could be connected to member organizations' focusing more on Emotet defense, it also suggests that Emotet activity is "once again steady after the group's reemergence earlier this year," the report says.
RH-ISAC isn't just about reporting threat indicators — member organizations also share information about specific threat topics. The "Top Sharing Trends" graph is an indicator of what kinds of threats organizations are most concerned about.
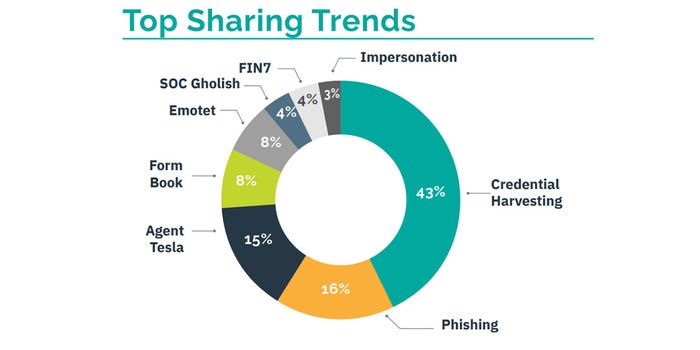
Credential harvesting remains the most common threat shared by members, at 43%, followed by phishing, at 16%. Information about malware attacks — namely Agent Tesla, Formbook, and Emotet — made up 31% of the threats shared by members.
The "Top Sharing Trends" graph outlines the frequency of sharing regarding a threat topic, while the "Top Reported Trends" graph shows the volume of threat indicators shared related to a given topic, according to RH-ISAC.
About the Author
You May Also Like

