Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
For Ransomware, Speed Matters
Someone interested in putting together a ransomware campaign has to consider several factors. The LockBit group touts its speed over competing families to attract potential buyers for its ransowmare-as-a-service.

Recent research has suggested that modern ransomware operations run much like legitimate businesses. Both have a management structure, different teams specializing in different aspects of the operation, and they outsource work when necessary. Many ransomware crews even have a PR team to draw attention to their latest victims and success stories. Recent research from Splunk suggests some groups are branching out into marketing, as well.
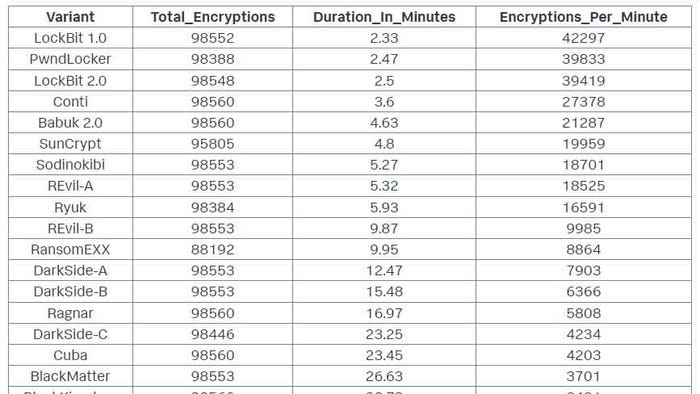
Earlier this year, the LockBit group posted a table listing encryption speeds for more than 30 ransomware families, highlighting the fact that LockBit 2.0 was the fastest. Measuring how long different ransomware takes to encrypt the files in victim environments is an interesting exercise from a technical perspective, but for LockBit, it was a marketing ploy to attract potential customers for its ransomware-as-a-service (RaaS) offering, says Shannon Davis, staff security strategist on Splunk’s SURGe research team.
The barrier to entry to launch a ransomware campaign is much lower, thanks to the availability of RaaS. LockBit and other “service providers” need to attract people who want to use the tool. By listing the encryption speeds on its site, LockBit is telling customers, “We are fast, use us, we are better,” Davis says.
Davis attempted to verify LockBit’s tests and claims about being the fastest. While Davis found that LockBit was faster than other ransomware families, there were some notable differences. For example, the “latest and greatest” version, LockBit 2.0, was actually slower at encrypting files than the original LockBit 1.0. And Splunk found that PwndLocker was the second fastest – though the LockBit group had ranked it 15th out of 30.
The 10 fastest families include some very well-known names. Conti, which has been in the headlines recently, was the fourth fastest in Splunk’s tests, while LockBit placed it 19th.
There is no way to tell whether the LockBit group fudged the numbers a bit to make certain groups look worse in the analysis than they actually performed, but Davis acknowledges that there are rivalries between crews as they go “head-to-head” competing for victims. The difference in results is most likely because of differences in testing methodologies, he says.
We Aren’t That Fast
While the rankings themselves are interesting (and good for ransomware marketing), security teams should note just how quickly ransomware performs its job. LockBit 1.0 takes 2.33 minutes. Conti takes a little over a minute longer, at 3.6 minutes.
“This is faster than any network defender can handle,” says Ryan Kovar, distinguished security strategist and leader of Splunk’s SURGe research team.
While the slowest, Avos, takes 132 minutes – or a little over two hours – the median is about 23 minutes. That’s still much faster than many organizations can act. Enterprise defense can’t “win” during the encryption phase, so their best chance for foiling a ransomware attack is to detect the intrusion before the encryption process kicks off, Kovar says.
Mandiant’s "M-Trends 2022" report notes that ransomware families tend to spend three to five days in the victim environment collecting information before kicking off the encryption process.
“We are not going to beat [them] in three minutes. We need more time,” Kovar says. “We need to be acting during those three to five days.”
Back to marketing, people often underestimate the extent to which ransomware is run like a business, Kovar says. Someone analyzed and measured the encryption speeds, but more than that, someone spent the time to create a graphic and put together a post discussing its research – and Kovar notes that all of this takes many hours to do. The fact that a ransomware crew has “top-tier marketing” and is thinking in terms of “value add” shows ransomware’s maturity, Kovar says.
“APT28 doesn’t have a marketing guy,” Kovar says.
About the Author
You May Also Like