US Secretary of State Antony Blinken stands at a lectern on a large stage with projection screens everywhere.
Cybersecurity Operations
Blinken: Digital Solidarity Is 'North Star' for US PolicyBlinken: Digital Solidarity Is 'North Star' for US Policy
The four goals of the US International Cyberspace and Digital Policy Strategy are to advance economic prosperity; enhance security and combat cybercrime; promote human rights, democracy, and the rule of law; and address other transnational challenges.

Ask the Experts
Read MoreFEATURED THREAT MONITOR
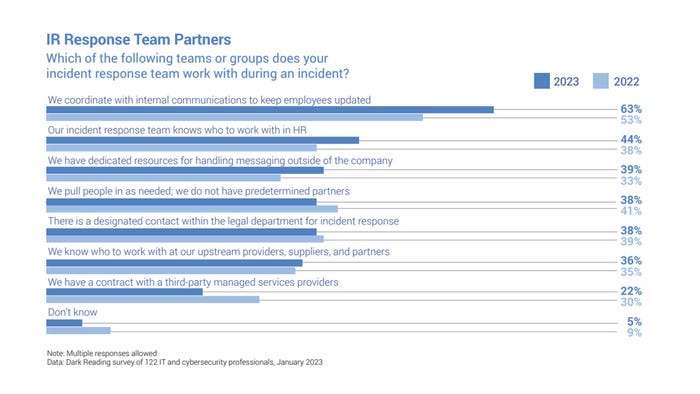
Effective Incident Response Relies on Internal and External Partnerships
Dark Reading research finds increased collaboration between security incident responders and groups within the HR, legal, and communications functions.