Hand holding a figurine up at the top of the career ladder.
Cybersecurity Careers
CISO as a CTO: When and Why It Makes SenseCISO as a CTO: When and Why It Makes Sense
Enterprises are increasingly recognizing that a CISO's skills and experience building risk-based cyber programs translate well to other C-suite positions.

Ask the Experts
Read MoreFEATURED THREAT MONITOR
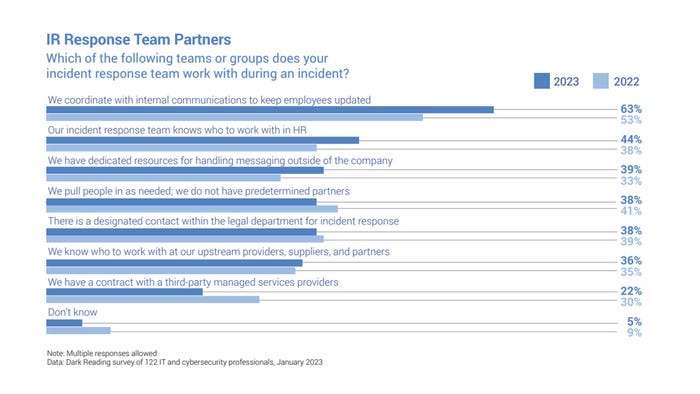
Effective Incident Response Relies on Internal and External Partnerships
Dark Reading research finds increased collaboration between security incident responders and groups within the HR, legal, and communications functions.