
News, news analysis, and commentary on the latest trends in cybersecurity technology.
Stop Zero-Day Ransomware Cold With AI
AI can help recognize ransomware attacks and stop them at computer speed.

2021 has seen a dramatic rise in ransomware attacks – but it's just not just their volume that’s alarming. The automation and speed of ransomware is also increasing, as attackers continually add new capabilities and employ different techniques. We are currently seeing a record number of "zero-day" malwares launched by cybercriminals – the novel, never-before-seen ransomware strains that the security world has yet to catalog.
This is concerning because security approaches that rely on rules, signatures, and historical threat intelligence – looking in the rearview mirror at yesterday's attacks – will remain blind to these threats as they emerge in the enterprise.
However, artificial intelligence (AI) is winning many battles. Organizations around the world armed with sophisticated AI technology capable of recognizing these previously unknown attacks are able to stop them at computer speed. In this article, we will walk through a real-world ransomware attack where a US electronics manufacturer used Darktrace's self-learning AI to identify and contain a never-before-seen strain of ransomware before it was too late.
What a Zero-Day Ransomware Attack Looks Like
At the organization in question, Darktrace’s AI technology had been deployed and immediately began learning the "patterns of life" for every user and device in the organization, from the ground up. This understanding evolves in real time as the organization changes, spotting subtle deviations that indicate a threat.
When attackers gained remote access to a device – possibly through a phishing email or compromised credential – the AI recognized the "patient zero" device began deviating from its typical behavior. The AI understood what would be considered "normal" for the manufacturing company’s digital systems and used the insights to detect the early signs of malicious behavior.
In response, the AI fired a series of alerts indicating the device was making unusual SMB connections and reverse DNS lookups. The AI was able to determine that the device's anomalous behavior was significantly similar to ransomware and kick off a series of actions in response to the malware infection.
The device was making an unexpectedly large number of connections, reading and writing a large number of SMB files, and transferring the data internally to a server it did not usually communicate with. The spike in internal connections between patient zero and the server was a strong indicator of malware attempting to move laterally through the network. The reverse DNS lookups were suspicious because they are frequently used during the reconnaissance phase of an attack. Moreover, the ransomware had started its encryption phase, and some of these files were in the process of being encrypted.
Further investigation into the SMB activity revealed the device had accessed hundreds of Dropbox-related files on SMB shares it had not previously accessed.
As soon as the AI detected that some files had been encrypted, the technology immediately blocked anomalous connections for five minutes. This had the immediate effect of stopping other files from being encrypted.
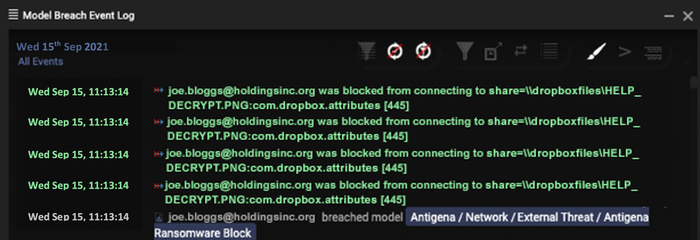
Stop the infected device from conducting lateral movement and ransom activity.
Response speed is important. Because the AI blocked those connections as soon as it did, the ransomware managed to successfully encrypt only four files. The connections are blocked for five minutes to give the AI time to collect evidence of other potentially malicious activities and minimize possible damage being caused during that interval.
It's not enough for the AI to just block connections, since the attackers are still in the network and can move laterally to other systems. Based on the scale and scope of anomalous activity the AI had detected, there was enough evidence to decide that this patient zero device should be quarantined for 24 hours. The attackers could no longer scan the network to learn about other systems, use harvested administrator credentials to gain elevated access, or perform other forms of reconnaissance.
By preventing the device from connecting to the server or any other device on the network, the technology effectively neutralized the threat.
No Signatures, No Problem
Based on what the AI knew about all devices on the network before the attack and everything it learned from the unusual set of alerts that were fired during the course of the infection, the technology was able to both stop the ransomware's encryption activity and lateral movement. The surgical intervention neutralized the threat while allowing normal business operations to continue.
There is a clear example of return on security investment. Based on recent trends, the manufacturer in question may have been hit with hundreds of thousands of dollars' worth of ransom payments had the attack not been thwarted. This novel strain of ransomware is unlikely to have been noticed or stopped based on previously encountered signs of an attack.
We can't stop breaches from happening -- but, as this example shows, self-learning AI technology can act before attackers wreak havoc. By spotting the subtle indicators of malicious activity and responding within seconds to stop the activities, the AI helps the organization avoid potential disruptions.
About the Author
You May Also Like

