Misconfigurations, Vulnerabilities Found in 95% of Applications
Weak configurations for encryption and missing security headers topped the list of software issues found during a variety of penetration and application security tests.
November 15, 2022

Nearly every application has at least one vulnerability or misconfiguration that affects security and a quarter of application tests found a highly or critically severe vulnerability, a new study shows.
Weak SSL and TLS configuration, missing Content Security Policy (CSP) header, and information leakage through server banners topped the list of software issues with security implications, according to findings in software and hardware tools conglomerate Synopsys' new Software Vulnerabilities Snapshot 2022 report published today. While many of the misconfigurations and vulnerabilities are considered to be of medium severity or less, at least 25% are rated highly or critically severe.
Configuration issues are often put in a less severe bucket, but both configuration and coding issues are equally risky, says Ray Kelly, a fellow with the Software Integrity Group at Synopsys.
"This really just points out that, [while] organizations may be doing a good job performing static scans to lower the number of coding vulnerabilities, they are not taking configuration into account, as it may be more difficult," he says. "Unfortunately, static application security testing (SAST) scans cannot perform configuration checks as [they have] no knowledge of the production environment where the code will be deployed."
The data argues for the benefits of using multiple tools to analyze software for vulnerabilities and misconfigurations.
Penetration tests, for example, detected 77% of the weak SSL/TLS configuration issues, while dynamic application security testing (DAST) detected the issue in 81% of tests. Both the technologies, plus mobile application security testing (MAST), led to the issue being discovered in 82% of tests, according to the Synopsys report.
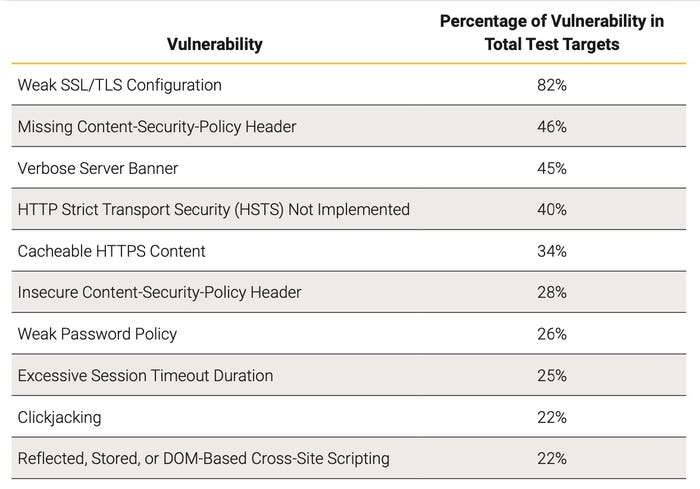
Most common application vulnerabilities. Source: Synopsys
Other application security firms have documented similar results. Over the past decade, for example, three times more applications are scanned, and each one is scanned 20 times more frequently, Veracode stated in its "State of Software Security" report in February. While that report found that 77% of third-party libraries still had not eliminated a disclosed vulnerability three months after the issue was reported, patched code was applied three times faster.
Software firms that use dynamic and static scanning in concert remediated half of flaws 24 days faster, Veracode stated.
"Continuous testing and integration, which includes security scanning in pipelines, is becoming the norm," the firm stated in a blog post at the time.
Not Just SAST, Not Just DAST
Synopsys released data from a variety of different tests with each having similar top offenders. Weak configurations of encryption technology — namely, Secure Sockets Layer (SSL) and Transport Layer Security (TLS) — topped the charts for static, dynamic, and mobile application security tests, for example.
Yet, the issues star to diverge further down the lists. Penetration tests identified weak password policies in a quarter of applications and cross-site scripting in 22%, while DAST identified applications lacking adequate session timeouts in 38% of tests and those vulnerable to clickjacking in 30% of tests.
Static and dynamic testing as well as software composition analysis (SCA) all have advantages and should be used together to have the highest chance to detect potential misconfigurations and vulnerabilities, says Synopsys's Kelly.
"Having said that, a holistic approach takes time, resources, and money, so this may not be feasible for many organizations," he says. "Taking the time to design security into the process can also help find and eliminate as many vulnerabilities as possible — whatever their type — along the way so that security is proactive and risk is reduced."
Overall the company collected data from nearly 4,400 tests on more than 2,700 programs. Cross-site scripting was the top high-risk vulnerability, accounting for 22% of the vulnerabilities discovered, while SQL injection was the most critical vulnerability category, accounting for 4%.
Software Supply Chain Dangers
With open-source software comprising nearly 80% of codebases, it's little surprise that 81% of codebases have at least one vulnerability and another 85% have an open-source component that is four years out of date.
Yet, Synopsys found that, despite those concerns, vulnerabilities in supply-chain security and open-source software components accounted for only about a quarter of issues. The Vulnerable Third-Party Libraries in Use category of security weaknesses was uncovered in 21% of the penetration tests and 27% of the static analysis tests, the report said.
Part of the reason for the lower-than-expected vulnerabilities in software components may be because software composition analysis (SCA) has become more widely used, says Kelly.
"These types of issues can be found in the early stages of the software development lifecycle (SDLC), such as the development and DevOps phases, which reduces the number that make it into production," he says.
About the Author
You May Also Like




