80% of Software Codebases Contain at Least One Vulnerability
Open source code continues its steady takeover of codebases, and organizations have made slight gains in eliminating out-of-date and vulnerable components.
April 12, 2022

Open source software's share of the typical codebase grew to 78% in 2021, yet companies continued to use components that are out of date and no longer maintained, leaving their software potentially vulnerable, a new study shows.
The vast majority of software codebases contain at least one vulnerability (81%), use an open source component that is more than four years out of date (85%), and contain components that have had no development in the past two years (88%), according to Synopsys' annual "Open Source Software Risk Analysis" (OSSRA) report, published this week. However, many of the data points show improvement over last year, when 84% of codebases had at least one vulnerability and 91% had no development activity in the previous two years.
Overall, the data suggests that companies are just starting to make headway against vulnerabilities and there is still a long way to go, says Tim Mackey, principal security strategist at Synopsys.
"This whole of idea [of] people trying to get their act together around what they would do from a software supply chain perspective is resonating to some extent, but it is not yet at a point where it is making a big dent in big things," he says. With many of these open source components, "people are not saying, I'm going to use [component X,] it is coming along for the ride with some other library that they are using."
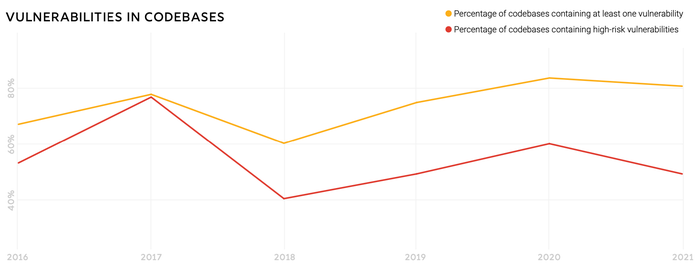
Source: Synopsys 2022 "Open Source Security Risk Analysis" (OSSRA) report
The Synopsys report is a unique look into the state of software security and license compliance, as the data comes exclusively from the company's service for due diligence that typically takes place during mergers and acquisitions (M&A). In 2021, the number of M&As surged 24% due to intense competition between corporate acquirers, private equity firms, and special-purpose acquisition companies (SPACs), according to consulting firm PricewaterhouseCoopers. The increased activity led to a surge in scanning codebases. Synopsys scanned more than 2,400 commercial codebases across 17 industries, a growth of 64%, according to the report.
Overall, the company saw improvements in lowering the number of high-risk vulnerabilities in audited codebases, with a significant decrease in the prevalence of top-10 high-risk vulnerabilities, the report stated. In the 2020 data, for example, 29% of codebases had components exposing the most prevalent vulnerability, while the 2021 data in this year's report identified the most prevalent high-risk vulnerability in only 8% of codebases.
"All reoccurring high-risk vulnerabilities saw significant decreases," the report states. "Prompt identification, prioritization, and mitigation of high-risk vulnerabilities can help teams address the risks that pose the greatest threat to their organizations."
Open Source's Persistent Spread
The improvements come as companies continue to deepen their use of open source software. In 2019, open source accounted for 70% of the codebases audited by Synopsys, climbing to 75% last year. Now at 78%, the security of a company's software overwhelmingly depends on the state of the open source components used by their development teams.
Yet the quality of open source software projects continues to be uneven, especially when it comes to security. For example, almost a quarter of software projects (23%) have only a single developer contributing the bulk of the code, potentially posing a risk to companies that use the library as a component of their own software, according to the report.
Unfortunately, companies have not eliminated the most significant risks from open source components and dependencies. With 88% of codebases containing outdated versions — components for which there is an update that has yet to be applied — organizations need to track the software and projects that they use in development with a software bill of materials (SBOM).
More SBOMs on the Way?
In the next year or two, SBOMs will become much more prevalent, but that still will not solve the issue, says Mackey.
"The bigger problem is that most people don't know what to do with [the SBOM]," he says. "It is another document that sits alongside the license agreement that nobody reads, and they don't know what to do about it, but they have heard that it has some magic voodoo associated with it, so they want it, but they haven't built a process for using it."
As companies become better about analyzing the components used by their software, they will also find and fix a lot of licensing issues as well. Because all sorts of open source licenses exist, businesses need to take care regarding what software they include in their own development. Currently, more than half of audited codebases (53%) have license conflicts, and 20% contain open source with no license or a nonstandard license.
According to the Synopsys report, "Codebases that contain open source components with no discernible license or a customized license have an additional layer of risk."
About the Author
You May Also Like




