FBI Seizes Genesis Cybercriminal Marketplace in 'Operation Cookie Monster'
The homepage of a widely used Dark Web forum for stolen cookies and other compromised data has been replaced by a seizure notice by the US federal law enforcement agency.
April 5, 2023

The FBI has seized the Genesis Market, one of the largest and most widely used Dark Web forums for stolen cookies, credentials, and tokens, plus bots and other tools for initial access to victim networks. It's yet another blow dealt by international law enforcement to those engaged in cybercriminal activity worldwide.
On Tuesday, the homepage of the marketplace was replaced with a notice that "this website has been seized" by the FBI as part of "Operation Cookie Monster." The notice cited a seizure warrant issued by the United States District Court for the Eastern District of Wisconsin as the impetus for the activity.
The seizure of Genesis was a collaborative effort between international law enforcement agencies and the private sector, according to the notice, which included the logos of European law enforcement agency Europol; Guardia Civil in Spain; Polisen, the police force in Sweden; and the Canadian government.
The FBI also is seeking to speak those who've been active on the Genesis Market or who are in touch with administrators of the forum, offering an email address for people to contact the agency.
Takedown of a Significant Initial Access Broker
Genesis was founded in 2017 as an invitation-only marketplace offering malicious actors access to other people’s data, from credentials and cookies to digital fingerprints.
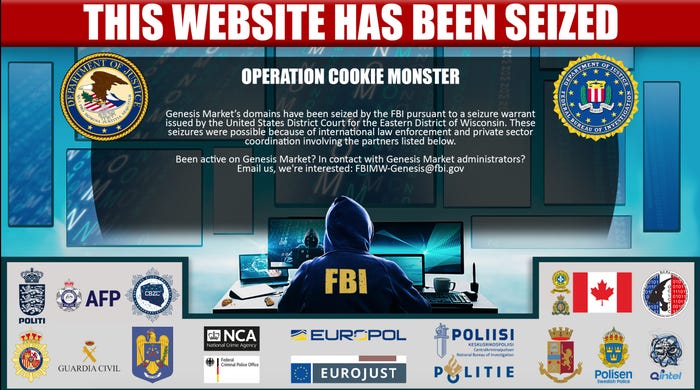
Screenshot of Genesis Market seizure notice.
A report last August by Sophos shed light on just how impressive an operation the site had become as an initial access broker (IAB), a service that helps threat actors gain a foothold in targeted networks to conduct various nefarious activity, including ransomware and cyber espionage.
"Genesis Marketplace is one of the earliest full-fledged IABs, and certainly one of the most polished," Sophos researchers said in the report at the time.
At that point, the site listed 400,000 bots, or compromised systems, and provided not only stolen data that cybercriminals could use to launch phishing and other cyberattacks, but also offered well-maintained tools—including bespoke offerings to help would-be threat actors evade detection and facilitate their abuse of that data.
Indeed, Genesis demonstrated the "growing professionalization and specialization of the cybercrime sphere," with the site earning money by gaining and maintaining access to victim systems until administrators could sell that access to other criminals, according to Sophos.
The various tasks that the Genesis Market bots could undertake included large-scale infection of consumer devices to steal digital fingerprints, cookies, saved logins, and autofill-form data stored on them. The marketplace would package up that data and list it for sale, with prices ranging from less than $1 to $370, depending on the amount of embedded data that the packages contained.
Another Win for Law Enforcement
Its position as a resource for rampant malicious cyber activity gained Genesis the attention of international authorities, which have been working together in a collaborative effort to take down not only various cybercriminal gangs but the Dark Web sites that help facilitate their activity.
Indeed, Genesis is another feather in the cap of the FBI and its cohorts, which already have put out of commission two other forums that provided significant resources for cyber-threat actors.
In March, the BreachForums underground hacker site went offline less than a week after its alleged leader was arrested in New York. Five days before the shutdown, US federal agents arrested man called Conor Brian Fitzpatrick, who they alleged was the chief operator behind BreachForums' administrator handle "pompompurin," in Peekskill, NY.
BreachForums itself had emerged in April 2022 in the wake of the takedown by the Department of Justice and other international agencies of another Dark-Web cybercriminal resource, RaidForums. Both marketplaces were major facilitators for cyberthreat activity, allowing users to buy and sell data obtained from breaches.
Other arrests of notable and alleged cybercrime figures in the last year include last week's arrest of one of the LockBit ransomware gang's ringleaders in Ontario, Canada; last month's extradition of Ukrainian national Yaroslav Vasinskyi from Poland to the US to be brought up on charges for his role as a member of the Sodinokibi/REvil ransomware group; and October's arrest by Brazil's Federal Police of a Brazilian man suspected to be a member of the cybercrime organization Lapsus$ Group.
About the Author
You May Also Like




