Cyberattacks via Unpatched Systems Cost Orgs More Than Phishing
External attacks focused on vulnerabilities are still the most common ways that companies are successfully attacked, according to incident data.
June 29, 2022

Attackers continue to find significant success targeting unpatched servers and vulnerable remote-access systems, researchers say -- and these types of compromises cost victim organizations 54% more than compromises caused by user actions (i.e., falling for phishing and opening malicious documents).
According to a Wednesday report by security firm Tetra Defense, which analyzed incident data from the first quarter, unpatched vulnerabilities and exposing risky services—such as Remote Desktop Protocol (RDP)—account for 82% of successful attacks, while social-engineering employees to take some action accounted for just 18% of successful compromises.
Incident data collected by the firm showed that the ProxyShell exploit for Microsoft Exchange servers accounted for about a third of external breaches, while insecure Remote Desktop Protocol (RDP) servers accounted for a quarter.
While the Log4Shell bug continued to see a great deal of media coverage, the attack vector was only used in 22% of breaches, says Nathan Little, senior vice president of digital forensics and incident response (DFIR) at Tetra Defense.
"We expect these tactics to continue—however, there is a finite amount of vulnerable Exchange servers," he says. "Over time—and we have seen this over the past five-plus years—the vulnerabilities that are used by threat actors will change, but [in general] externally accessible vulnerabilities will continue to be a favorite attack vectors for cybercriminals."
Healthcare topped the list of targeted industries, with nearly 20% of compromised organizations falling in that category. Finance and education tied for second at 13%, and manufacturing accounted for 12% of incidents, according to Tetra Defense's data.
Tetra Defense also tracked the cybercrime actors responsible for most breaches, and found that four groups—Lockbit 2.0, BlackCat, Conti, and Hive—are responsible for about half of all compromises investigated by the firm.
Cloud Misconfiguration: Less Costly Than Other Cyber-Incidents
While a common form of vulnerability, misconfigurations did not account for much of the cost of breaches, with few requests to investigate such compromises, Tetra Defense's Little says.
"For misconfigurations—because they can range from an AWS S3 bucket being publicly accessible with sensitive information stored in it -- to a non-sensitive server being exposed with a default username and password — the costs can range drastically," he says. "Typically speaking, the costs of misconfiguration are lower than unpatched systems and accidental user action."
While damages are hard to estimate, Little sees the potential impact as a percentage of revenue, with a reasonable financial impact of a major cybersecurity incident accounting for 2% to 10% of annual revenue.
He also notes that two controls -- comprehensive patching and using multifactor authentication (MFA) -- could have prevented nearly 80% of the investigated incidents. That includes 57% of external compromises that used an unpatched vulnerability, and the 13% of successful attacks on virtual private networks that either exploited a vulnerability or used stolen credentials to gain access where there was not MFA enabled, Little says.
"This shows that these two controls alone would have a drastic impact in decreasing the risk of a ransomware incident," he says. "The cost savings for a company would be the difference between having a data breach and ransomware incident that could stop business for a week or more and cause reputational harm or not."
Conflicting Data
Data on successful compromises can help companies determine the most critical attack vectors to address, but it should be noted that the conclusions depend greatly on the specific incident-response firm.
For instance, earlier this year, security-advisory firm Kroll saw phishing continue to grow, with 60% of the cases the company investigated using phishing attacks as the initial-access vector. Meanwhile, the exploitation of vulnerabilities dropped by half to 13% of all initial compromises, down from 27% in Q4 2021.
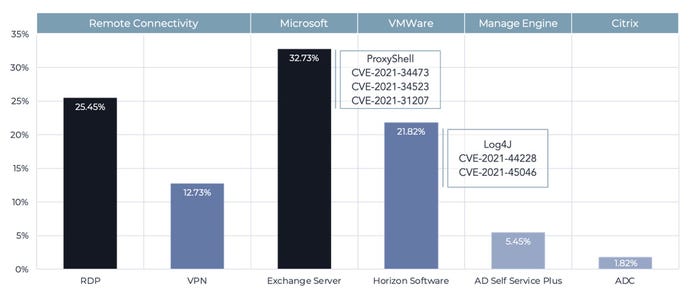
Source: Tetra Defense
"Despite a decrease in ransomware incidents and the disruption and exposure of a number of key threat groups ... 2022 is proving to be the year of attacker diversity, with actors exploiting new methods, such as email compromise, leading to extortion," Kroll stated in its latest quarterly threat landscape report.
Ransomware Spike
By way of context, in February, incident-response firm CrowdStrike released its annual report on its own incident data from 2021 showing that breaches related to ransomware attacks had grown by 82%. In addition, the company's data showed that malware had only been used in only 38% of successful intrusions, with 45% of attackers manually conducting the attacks.
The average time to move from an initial compromise to attacking other systems on the network—what CrowdStrike calls the "breakout time"—remained near 1.5 hours, according to the company's data.
About the Author
You May Also Like
Cybersecurity Day: How to Automate Security Analytics with AI and ML
Dec 17, 2024The Dirt on ROT Data
Dec 18, 2024




