Attackers Hone Their Playbooks, Become More Agile
Less malware, more interactive intrusions, and big game hunting lead to more success, with an 82% increase in ransomware-related data leaks.
February 17, 2022
Cybercriminals and nation-state actors adapted to defenders' tactics and became more efficient in 2021, with attackers relying more on data leaks combined with ransomware to extort increasing sums of money from companies — and in some cases using data leaks without encrypting data to force a company to pay, according to two analyses published this week.
Data leaks associated with ransomware jumped 82% in 2021, compared with the previous year, according to cybersecurity firm CrowdStrike's annual "Global Threat Report," published Wednesday. Almost two-thirds (62%) of attackers avoided using malware for the initial compromise, and in 45% of incidents, the attackers used interactive intrusion — with fingers on the keyboard — to infect systems.
In the past, companies use to be able to blame "sophisticated actors" for breaches, provide customers with credit-monitoring services, and essentially avoid any major consequences of a breach, but now the adversaries are taking control of the disclosure and the negotiation, says Adam Meyers, senior vice president for intelligence at CrowdStrike.
"Organizations need to understand that the threat actors are not just going after systems," he says. "They are going after their data and they are using it against them in ways that are far more dangerous than just encrypting it."
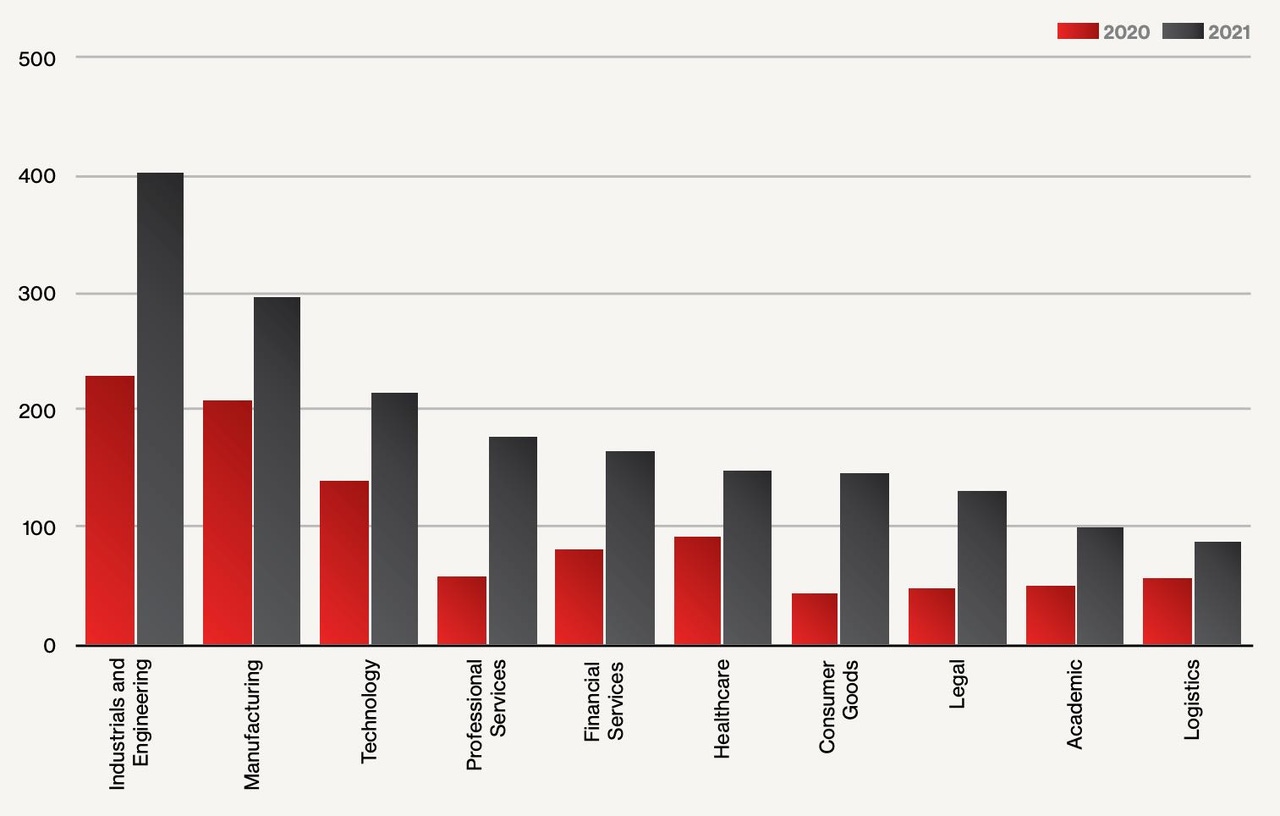
The adoption of data extortion highlights how attacks change to adapt to defenders tactics, with data leaks hitting every industry in higher numbers in 2021 than the previous year. The industrial and engineering sector suffered the most attacks, with ransomware-linked data leaks rising above 400 incidents, compared with about 230 in 2020. The second most targeted industry, manufacturing, had almost 300 data leaks, while technology firms suffered more than 200, according to the CrowdStrike report.
In 2021, the company investigated more targeted attacks, which increased to 18% of the total incidents investigated, up from 13% in 2020. The share of hacktivism-related threats remained the same at 1%, while e-crime and unattributed threats, which make up the majority of incidents — a half and a third, respectively — fell slightly.
A key theme for 2021 is that attackers continue to move operations to new approaches or malware wherever possible, the report states.
"New tactics, techniques and procedures (TTPs) used in data theft attacks in 2021 aided adversaries in extorting their victims — for example, [one group] avoided using publicly available exfiltration tools by developing their own," CrowdStrike states in the report. "Another major development was increased data theft and extortion without the use of ransomware, leading to the establishment of new marketplaces dedicated to advertising and selling victim data."
Data Weaponization
While many organizations have refused to pay ransoms to cybercriminals, the attackers have attempted to take control of negotiations back from victims by adding data leaks — and in some cases, denial-of-service attacks — to their repertoire. Organizations that do not comply with demands will find sensitive data leaked to the public, Meyer says.
"Data is increasingly being weaponized, and more and more actors are doing data weaponization because it gives the attacker a control lever with the victim," he says. "It becomes a way for the threat actor to take control of the situation in a way that they could not when they only encrypted the data."
Attackers' shift in their attacks is a theme of another report published this week by security advisory firm Kroll. Exploitation of vulnerabilities jumped to the second most-used method of initial access, up from fifth place, with 27% of attacks in the fourth quarter using exploits, according to Kroll's "Q4 2021 Threat Landscape" report. The top method of initial access continues to be phishing attacks that steal credentials, the company states.
Ransomware and e-mail compromises, including phishing, continue to be the most common types of threat incidents, together accounting for two-thirds of all incidents, according to Kroll. Companies need to become more agile in how they test and apply patches for critical systems, according to Keith Wojcieszek, managing director in Kroll’s cyber risk practice.
"While law enforcement made significant headway in disrupting attackers, the fact that we saw new ransomware variations and extortion sites, combined with splinter ransomware groups, demonstrates the agile operations and malicious intent of these criminal groups," he said in a statement. "Add this to the higher number of software vulnerabilities being exploited by ransomware operators and the speed at which they are compromised, and it underlines the importance of legislative action against attackers to take them out of operation completely."
Attackers continue to give defenders very little time to react to a breach. One way CrowdStrike measures the speed and agility of attackers is the so-called "breakout time," which is the amount of time it takes for an attacker to move from the initial compromise to infect other computers on the network. Between 2022 and 2021, the breakout time remained nearly the same, with attackers averaging 1 hour and 38 minutes in 2021 and 1 hour and 32 minutes the previous year.
About the Author
You May Also Like



_Daniren_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
