Targeted Attacks: A Defender's Playbook
Cyberthreat actors are increasingly going after a single victim. Here are some tips to help your organization get ready.
December 15, 2014

 Download the entire January 2015 issue of Dark Reading, distributed in an all-digital format.
Download the entire January 2015 issue of Dark Reading, distributed in an all-digital format.
Most cyber attacks today are random, automatically generated exploits that prey on vulnerable systems. But security experts now say there's a small but growing percentage of online attacks that are carefully targeted to compromise a single victim.
Advanced attackers are picking targets deliberately in order to steal very specific intellectual property, collect trade secrets, and scoop up troves of customer data.
To achieve these goals, these criminals are not only homing in on certain industries but also specific organizations and even particular individuals whom they hope to trick into helping them infect company machines.
When these crooks choose a target, they persist until they get in -- changing tactics or targeting different individuals if they don't succeed the first time. And when the criminals achieve success with these attacks, they aren't content to infect PCs; they try to dig deep into the network and find ways to gain administrative access to the organization's most sensitive systems and data.
These targeted attacks often rely on human nature and simple online research as much as technical hacking ability. And because most enterprises still model their security practices around generic malware and automated exploits, they're easy prey for these sophisticated, targeted attacks. Clearly, some new defenses are needed.
Figure 2: 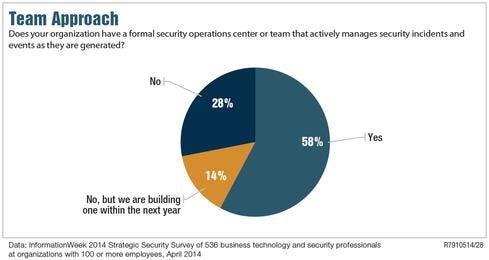
Who's doing the targeting?
Understanding the kinds of attackers doing the targeting offers an important first step in diagnosing targeted attacks. By coming to terms with the motivations these bad guys have for stealing specific data or gathering certain technical information, security teams can do a better job assessing risk and developing a stronger defense.
Most attackers fall into one of three buckets: hacktivists, nation-state-sponsored hackers, and organized cyber criminals.
Hacktivists are seeking to harm an organization or an industry because its operations conflict with the hacktivists' beliefs.
"Hacktivists are a real fear for organizations, especially in the energy sector or companies that do work overseas and might have practices that are not well received," says Jeff Horne, VP of emerging solutions for security consulting firm Accuvant. Hacktivists just want to disrupt a business. "They're the ones trying to do things like release email spools and cause havoc on the network."
State-sponsored attackers are usually employed by or associated with foreign spy agencies. They're trying to advance their country's military or economic interests by stealing intellectual property or gathering intelligence about an organization's operations. This could mean breaking into a defense contractor to steal blueprints, or into a government contractor to pilfer information about employees that could be used for future spy operations. These cyber-espionage operators often extend their operations beyond defense and other government targets and into commercial suppliers and contractors. In some cases, they seek intellectual property to help their country's commercial interests.
"It may not be how it works here, but other countries use their intelligence apparatus to benefit their domestic companies against US companies," says Anup Ghosh, CEO and founder of Invincea, an advanced malware detection and response vendor. "The spy agencies work hand in hand with their industry to get that kind of competitive intel."
Meanwhile, organized cyber criminals may also be on the hunt for specific intellectual property or information on how a company operates. They're hired to steal information for a company's competitor, or they look to profit by selling information on the black market or even engaging in insider trading.
For example, a go-to-market plan for a technology company or information on drilling sites scouted by an oil-and-gas company may be sellable insights. Cyber criminals will also target companies if they think they can steal valuable customer information for identity theft and credit card fraud. Over the past year, Home Depot and Target were among many companies specifically targeted by attackers to steal details about customers.
"These are organized groups, well funded, well resourced," says Michael Sutton, VP of security research for Zscaler. "The ultimate goal is almost always financial gain."
Keeping these three targeted attack motivations in mind can help a company assess which assets a persistent attacker may want to steal. "For instance, if you are in a retail organization, and you have customer information -- that's a value to certain Eastern European groups," says Ghosh.
Types of targeted attacks
While different attack groups may target different types of data and information, the overall operational framework for their attacks tend to look alike.
The majority of targeted attacks start with a spear-phishing campaign. These are not the poorly spelled, mass-emailed phishing attempts of yesteryear. Instead, advanced attackers do online research to find out email naming conventions and then find people they can email with a phony, but convincing, message.
"As an attacker, I'm able to do research about the company to find things like, 'Hey, I know this particular person is speaking at this particular conference at this particular time,'" says Alex Cox, senior manager of RSA FirstWatch. By guessing at that person's email address using the company naming convention and using the knowledge that someone
at a conference probably talked to more people than they remember, it becomes easy to create a lure. Says Cox: "I can then say, 'Hey, this is Joe. I met you at the conference. Really enjoyed your stuff. Hey, can you click on this link and tell me what you think about this business opportunity?'"
By tailoring a phishing lure to a specific person, attackers are very likely to get that person to click on a link or open an email that will infect their machine. If they don't get in through one person, they'll find another target until someone bites. These lures are usually tied with a piece of zero-day malware designed to get past antivirus filters. These malicious software packages take advantage of vulnerabilities not yet discovered by security researchers.
Sometimes attackers invest in malware kits and tweak them for a specific target. In other cases, they develop custom malware based on information they discovered about the company's infrastructure through port-scanning and other reconnaissance. To determined attackers who expect a big payday from a targeted campaign, it's worth the up-front investment to do research and even coding.
Figure 3: 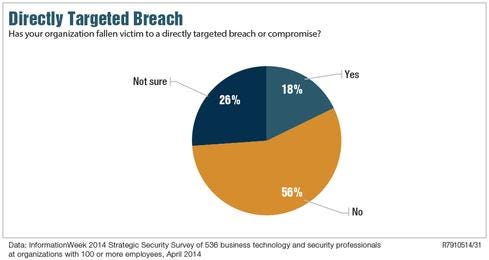
Once that first machine is infected, the attacker uses other malware to establish a back door or other foothold into the system and uses access on that machine to move laterally into the network. Attackers could gain this access by keylogging for credentials or by attacking installed software that uses internal network connections.
"Once I'm in the network, and I've found the information that I need, it's relatively easy for me to get it outside of the network because I know the company has to [have open connections] to do business [online]," says RSA's Cox.
While spear phishing is usually the go-to technique for first penetration, it's not the only option for targeted exploits. In some cases, attackers learn about third-party business relationships to find a weaker side channel to break into a particularly well-defended network.
"Corporation X may have excellent security, but Corporation Y may not have security that's as good," says Cox. "So I know if I can get into Corporation Y, and then I can leverage that connection into Corporation X, it gives me a back door into the higher security organization that I can manipulate and access," Cox says. "We've seen attackers leveraging VPN systems in that way multiple times."
Targeted attackers also build out their attack repertoire through malicious advertising, also known as malvertising. In the past, malvertising was primarily used to conduct click fraud on the advertising networks. But now criminals are employing targeting techniques using real-time bidding systems to place ads that will be seen by specific IP address ranges and specific geographic locations; they're aimed to hit users browsing from targeted firms. Researchers at Invincea recently found attackers using this "micro-targeting" malvertising technique to go after defense firms.
And sometimes attackers break into a specific target by more traditional routes. According to Accuvant's Horne, targeted attackers are buying control of already infected machines from bot herders who may have infected a host through random attacks.
"Why would an attacker go knocking on all the doors and try to bypass firewalls and discover a vulnerability in a web server when for a small amount of money they could just purchase a machine that is already on the network so they could install anything they want?" Horne asks.
Detection and response
However the targeted attackers come in, companies are failing miserably at detecting and responding to them, despite big investments in security products.
"Enterprises are at a huge disadvantage in that the adversaries only need to beat them once, whereas they need to beat the adversary every time," Zscaler's Sutton says. "And the bad guys can turn on a dime. There is no bureaucracy. There is no change control process. You try an attack today, it doesn't work, no problem. Try something completely new tomorrow."
Companies lack visibility, which is the reason they often fail to find out the bad guys are in the network before they flee with valuable information. "It's the rare enterprise that has true visibility into their threat landscape today," Sutton says.
Visibility starts by understanding where the targeted "crown jewels" reside on the network, and then monitoring them very closely for abnormal behavior, says Cox. Unfortunately, "companies know where their crown jewels are, but they don't really know what a good day looks like," he says. "It's hard for them to say what a bad day looks like from a technical perspective."
For many organizations, the high "signal-to-noise ratio" coming from signature-based security technology is drowning security analysts
with data, to the point that even when an alert is triggered by a targeted attacker it's ignored because it looks like all the other attacks.
"The Target breach is probably the best example of a company knowing that the breach was detected early on, but it was an alert within millions of other alerts, and it got ignored," Sutton says.
As a result, organizations need to stop waiting for alerts and start adopting a more proactive "hunting" method to look out for targeted attackers silently roaming the network, according to Dmitri Alperovitch, co-founder and CTO of CrowdStrike, a threat detection vendor focusing on advanced and targeted attacks.
"You're going to assume that the adversary has evaded all your technology, and you're going to try to fully instrument your network to look for anomalous activities, and look for signs of compromise that may already exist," Alperovitch says. "You need to understand everything that's going on from an execution perspective in your corporation so that you can analyze for both external threat actors and potential insiders looking to do damage to your network."
To make that happen, though, organizations need to overcome a skills and resource gap within security personnel.
"Technology is fantastic, but without a great team that can look at the data, prioritize it, and respond effectively to incidents, you're really not able to leverage it fully," Alperovitch says. "Upgrading the talent is probably the No. 1 challenge for organizations right now."
Jason Lewis, chief research scientist with Lookingglass, agrees, saying that many organizations get ahead of themselves when investing in threat intelligence feeds, because they don't have the people to utilize the information. These subscription services provide data about how attackers are operating. "Make sure there are people and processes to deal with the threats, then add the feeds and the intel," Lewis says.
Figure 4: 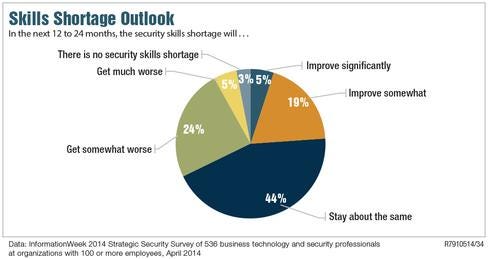
More-resilient infrastructure
Some experts believe that companies must look beyond detection and response for targeted attacks. "We're not going to stop them getting in eventually," says Chris Morales, practice manager of architecture and infrastructure for NSS Labs, a testing and analyst firm. Morales believes that more companies need to view targeted attacks as an architectural issue. "It truly surprises me that I still find organizations with almost a flat trust model where internal systems and services connect to each other and where access from work stations can get you anywhere," Morales says. "They have all these defenses, but once you're past them, you're in and you can pivot attacks easily."
The trick, he believes, is that companies need to design their networks and application infrastructure in a way that it takes longer for attackers to find what they're looking for. For example, segmenting the network can work much like a shipbuilder designs bulkheads, so that a collision limits damage to only one section of a ship. When servers running one type of application or data are separated from those running another type, it's more difficult for attackers to find what they're looking for through the compromise of a single asset. And the longer they're on the network, the more likely they'll be exposed before they steal data.
"We need to slow down their success rate," Morales says. "So I'd advise the use of server isolation zones, or more specifically, an application-centric trust model. That way, this application can't touch this other one and, not only that, the presentation layer can't access the middleware layer or the database layer."
So even if an attacker breaches a web server, they're not able to get to application processing or to a database. Or if the attacker accesses a client, they can't get to any other clients or servers.
This model is more about cyber resilience than cyber protection, and about reducing the probability of an attack rather than just the impact. And that's huge when it comes to targeted threats, which are still rare but can cause more damage than any other type of cyber attack out there.
Get the new issue of Dark Reading on targeted threats.
About the Author
You May Also Like




