Deconstructing an iPhone Spearphishing Attack
How criminals today bypass smartphone anti-theft protection and harvest AppleID and passwords taken from fake Apple servers.
The nature of spearphishing attacks has drastically evolved: We've moved from crudely written, poorly spelled scattergun operations to highly targeted campaigns that leverage knowledge about the victim to increase the attacker's chances of success. Once a focused attack on high-value targets, the mark has changed and the ordinary consumer is now in reach. A recent report revealed the rate at which people fall for mobile phishing attacks has increased 85% every year since 2011.
That's not to say that I'm not a fan of recent anti-theft technology adopted by smartphone manufacturers like Apple. I am. Before Apple released features like Find My iPhone and Activation Lock, iPhones were the most stolen item in almost every city. In 2012, over 50% of robberies in San Francisco involved theft of a mobile communications device. With resale prices of new iPhones of dubious pedigree surpassing $1,000, it's easy to see why. But within 12 months of the release of Activation Lock and Find My iPhone for iOS 7 in 2013, iPhone theft fell 50% in London, 40% in San Francisco, and 25% in New York. These features were exactly what we needed to head off surging crime rates. Unfortunately, there are few groups as innovative as criminals. Within months of Apple deploying these anti-theft measures, criminals found ways to limit their effectiveness.
Fast forward to today: When a smartphone is stolen, thieves now power it down and often place it into a foil-lined bag to prevent signals from reaching it. The devices are then powered up only when thieves are positive no signal can reach or inspect them. If the phone is out of date and a software vulnerability exists, they hack the phone and wipe it clean to be resold. If the phone is up to date but not valuable enough to resell, it is either junked or sold for parts. This can easily happen on both older and newer models of phones. For example, here's how an attacker launched a spearphishing attack this past summer during the San Francisco Pride Parade. On June 30, a pickpocket stole an iPhone X from a teenager during the parade. The phone was up to date and locked with FaceID, and had Activation Lock as well as Find My iPhone enabled. The teenager realized the phone lost within 10 minutes, and immediately enabled lost mode. Too late. The thief had immediately powered the phone down and knew better than to do anything with it.
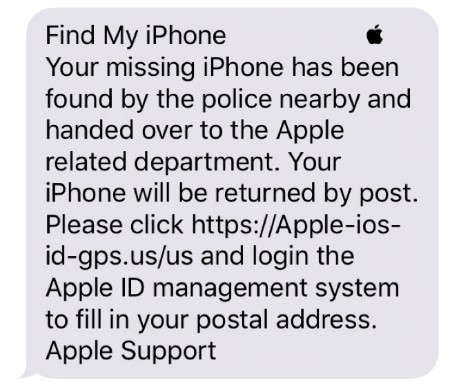
A little over a week later, the owner started to receive messages, claiming to come from Apple:
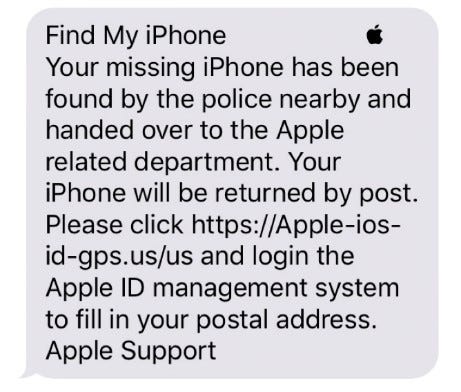
Despite reporting the messages as "junk," per Apple's own instructions, the texts continued to flood in. At one point, more than 10 messages per day came in at all hours. The strategy — to spam the target with messages — aims to bully and wear victims down until they click a link just to make it stop. In this case, the attacker employed a system that rotated through several iCloud addresses and phone numbers to prevent the target from blocking or ignoring any of the messages. The repeated nature of the messages and the reappearance of specific examples of spelling, capitalization, and punctuation errors made it clear this was an automated system.
If the target clicked on one of the links, they were immediately redirected to a fake Find My iPhone page that attempted to harvest their AppleID and password, as shown below, taken from fake Apple servers.
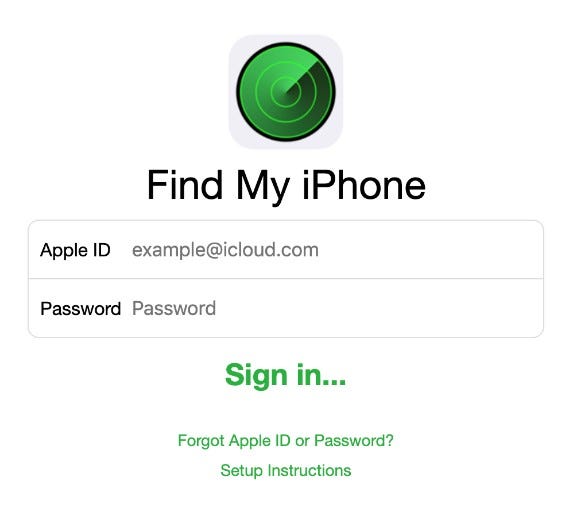
If the target entered their AppleID credentials into the site, the phone would have been quickly deleted from their account. And often, the first moment targets know this has happened is when the missing device disappears from the list of devices trackable through Find My iPhone.
Sometimes, for good measure, the thief will hijack the target's AppleID, changing email addresses and contact information to exploit the account further. As we become increasingly dependent on our online identities for tools like Apple Pay and online banking, the potential rewards from hijacking an account increase exponentially.
The Best Defense
Follow these eight simple measures to protect your privacy in the event of smartphone theft:
Make sure your device has a strong alphanumeric password in addition to using security features, including biometrics like facial or fingerprint recognition.
If your device is lost or stolen, in addition to setting it to wipe and enabling lost mode, you should also change all of your passwords and log out of any accounts that you access via that device.
Speed is important. Start by immediately remotely locking your device and then move onto locking down your accounts. Even if you aren't sure if the device was misplaced, lost, or stolen, take steps to protect yourself.
Some applications and services allow you to examine and kill sessions you don't recognize. If this feature is available, use it, but simply kill all sessions. Then you can log back in safely knowing that if a thief does gain access to your phone, they can't get into your accounts.
While stories pop up from time to time about consumers recovering stolen devices themselves, it's usually a better idea to leave crime-fighting to the police.
Take great care when handling messages with links. Never click on a link from an unknown sender and be very cautious with those from known senders. It's increasingly common for attackers to hijack legitimate email accounts in order to send malicious links to friends and family.
The more urgent a message seems, the more scrutiny you should give it. Attackers like to threaten, coerce, and demand because they know people act rashly when in a hurry.
If a message claims to come from an institution you use, instead of clicking on the link, open a new browser window and go to its website. Alternatively, pick up the telephone and call it.
Related Content:
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: A Beginner's Guide to Microsegmentation
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: A Beginner's Guide to Microsegmentation
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




