
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
Phishers' Latest Tricks for Reeling in New Victims
Phishing works because people are, by nature, trusting -- but these evolving phishing techniques make it even tougher for security managers to stay on top.

Figure 1: 
From his days as an IT worker, to his work as a journalist covering information security, to his time now as a security researcher with Akamai, Steve Ragan has been watching phishing techniques evolve for nearly two decades.
But it wasn't until late 2007, when the Storm Worm started taking off, that Ragan's education began in earnest.
"Storm circulated via email and targeted current events as a lure to get people to open malicious attachments and URLs," Ragan recalls. "It worked well, and the botnet continued to grow. Storm was a spam campaign — at least that is how it was commonly referred to — but it was phishing at its purest. The idea was to send an email, pique the curiosity of the recipient, and deliver a malicious payload. "
Phishing is still going strong. But what has changed since Storm's earlier days?
Everything, according to Ragan.
Gone are the days when most phishing emails were easy to spot due to their grammar and spelling errors, he says. Criminals have evolved, and scripts are tighter, error-free, and more focused. Spear-phishing, which is a highly targeted type of phishing attempt that focuses on a specific individual or group, is on the rise. So are business email compromise (BEC) attacks, which are targeted phishing attacks on business emails — typically those held by high-level executives. In fact, according to the FBI, BEC attacks resulted in $12 billion in losses between October 2013 and May 2018.
"Criminals have been known to call the targeted organization or victim to confirm information, and public records are used to corroborate information, such as who works in accounting and who their direct report is," Ragan says.
Phishing continues to be a successful tactic because people are, by nature, trusting. In addition, techniques keep evolving, making it tough for security managers to stay on top. Ragan, and several other security industry experts who track phishing tactics, offer a breakdown of the latest tricks and traps phishing criminals are up to these days.
{Continued on Next Page}
Figure 2:  Image Source: Akamai
Image Source: Akamai
1. Geolocking and Geotargeted Attacks
Geolocking involves targeting victims in one geographical location for efficiency, according to Ragan.
"You'll see this with retail and financial phishing," he says, referring to one campaign his team is monitoring. "Currently a text-based phishing campaign targeting the financial sector is only allowing traffic from mobile networks and is blocking direct access via desktop browsers or crawlers."
Another newer tactic includes campaigns that abuse brands and target highly focused geographic areas, says Or Katz, principal security researcher at Akamai. The research team recently spotted a phishing attack campaign targeting people planning their summer vacation in specific regions. The criminals behind these attacks used the names of several popular amusements parks. They employed a phishing tool kit named "Three Question Quiz" and included at least 17 brands and more than 30 phishing websites, targeting amusements parks located in the US, Europe, Asia, and Australia.
Based on evidence collected from one of the UK brands impacted by the phishing attacks, Akamai noted the campaign was mainly targeting victims in the first two weeks of June – a busy time when people plan summer vacations.
2. Advanced Evasion Techniques
Phishing kits have evolved, according to Ragan, "to the point where evasion techniques are almost the central focus rather than the actual theme of the kit. Once the anti-bot and obfuscation techniques are in place, then the developer or team will select a target and develop the website as a near-perfect clone."
In addition to the aforementioned geolocking example, other evasion strategies include network-level blocking, obfuscation of text and images, keyword filtering, and self-hosted storage, where harvested credentials are stored locally instead of emailed to the criminal.
Elad Schulman, CEO of Segasec, notes his researchers have seen more advanced cloaking techniques than observed in the past.
"Hackers filter users by geolocation, user agents, and other parameters so that when a hosting provider tries to see the content of a fraudulent site, what they see instead looks completely legitimate, fooling them to believe there is nothing problematic there," he says.
3. Dynamic, Realistic Sites
As Schulman and Ragan note, phishing criminals have become extremely adept at creating sites that look nearly identical to authentic sites. In many instances, scammers are using dynamic attacks that look, feel, and behave like the original websites, Schulman says.
"For example, users can login to a website that looks like it is representing their bank account, see their account and even the right balance, and get scammed," he explains. "This type of scam is based on man-in-the-middle attacks, which completely and dynamically mirror the original site while bypassing even the multifactor authentication mechanisms."
4. Using Social Media
Most people have received a phishing attempt on social media by now. You know how it goes: A message appears in your inbox from a connection that says, "Is this you?" accompanied by a link. These kinds of attacks have ramped up, Katz says.
"Phishers have increasingly turned to social networks as a distribution channel," he says. "This tactic gives the attackers the ability to propagate rapidly and at the same time evade traditional security controls, such as email gateways."
5. Mobile Attacks
Phishing attacks that target mobile devices are also not new, but what is different is how much more common they have become, according to James Plouffe, a strategic technologist at MobileIron.
"Phones are extra susceptible to phishing attacks because of the way they are designed," he says. "For example, applications are becoming an attractive way in because they have the data and the permissions that give access to a user's microphones, cameras, and credit card information."
As the workplace continues its shift to mobile, Plouffe says his team anticipates more of these types of attacks – and criminals will be looking for details on company acquisitions, intellectual property, and revenue numbers.
{Continued on Next Page}
6. Hiding in Legitimate Apps
File-hosting and sharing websites, such as Dropbox or Google Docs, are among the newest attack vectors that Eric Brown, senior security analyst at LogRhythm, says he has seen.
"The websites as a whole are legitimate, but attackers are starting to use them as avenues for hosting specific attacks," he says. "For example, an attacker will upload a file that includes a malicious URL that is difficult for the service to identify or block. Then the targeted recipients receive emails via the service's notification system, with links to the unsafe or malicious hosted file."
This kind of attack is stealthy because it is harder for an employee to recognize than a standard phishing email, Brown says. The notification email is from a genuine service and email address, and the link to the hosted file is legitimate as well – it's being hosted on the website the employee actually uses. It's only after the employee opens the document that he's then exposed to the malicious plant.
Figure 3: 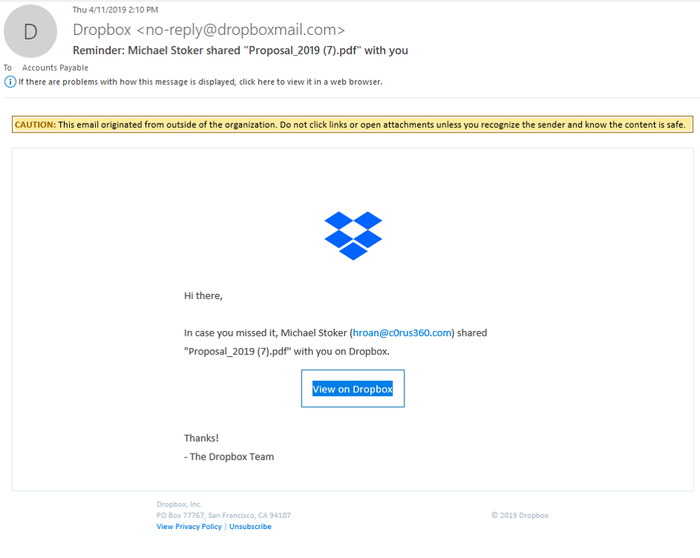
Here is a screen shot of an original email. The email sender (dropboxmail.com) is legit and from the Dropbox.com notification service. The only part that looks suspicious or out of place is the name of the person who shared this document; "Michael Stoker," itself, is OK, but it does not match or look close at all to the associated email: "[email protected]." (Image Source: LogRhythm)
7. Industry-Specific Hooks
Ranjeet Vidwans, co-founder of Clearedin, says his team is noting a risk in phishing within the real-estate industry.
"It's an industry where there's several third parties – insurers, agents, banks – that may be unfamiliar to the buyer," he says. "Sensitive information is often sent via email."
Vidwans predicts there will be more BEC-style phishing attacks, too.
"BEC attacks would mean a bad actor posing as, say, a closing agent, emailing their assistant to please shoot over some quick SSNs so that they can file this paperwork, and people will do it without thinking twice," he says.
8. New Topical Lures
Vidwans also notes that the age-old tactic of using what is hot or topical is new again, but the hook is different. For example, the possibility of a recession is now a ripe topic for phishers when looking for ways to lure victims.
"We expect to see damage from phishing activity rise significantly once the recession hits in full," he says. "There are a few reasons for that. Layoffs mean you have less staff doing the same work. So employees are moving at a fast pace and are less likely to catch suspicious spear-phishing attempts. Another reason is you have more phishers out there, looking to make money in an ailing economy. You also have more job search activity – and in a bad economy – people are much more open to opportunities than they otherwise may be."
Related Content:
About the Author
You May Also Like

