How Hackers Create Fake Personas for Social Engineering
And some ways to up your game for identifying fabricated online profiles of people who don't exist.

On April 18, 2022, a handful of US citizens scrambled to get their taxes filed. While tax season is usually a stressor, consider that these filers got some unsolicited help. Imagine that somehow, strangers that might resemble angels just appeared in their lives, offering guidance and help to work with them through this process … all through the computer screen.
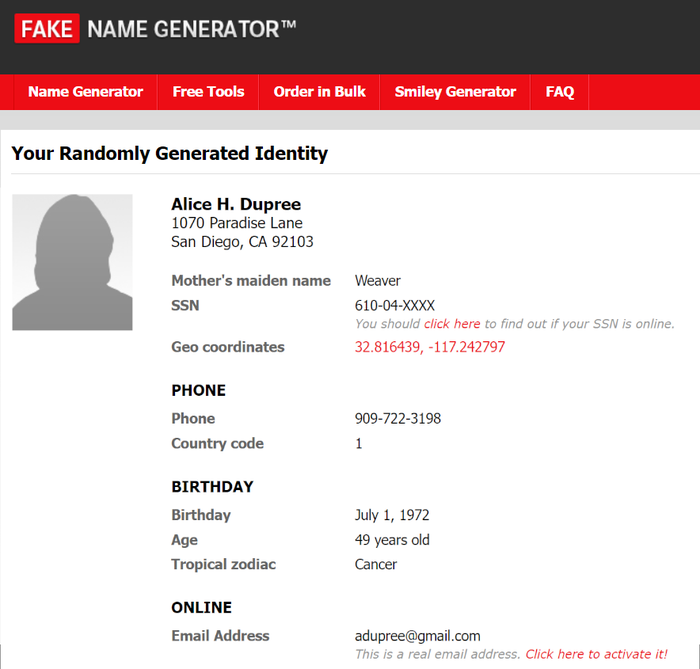
For our story, let's consider we receive a benign LinkedIn message from "Alice Dupree," stating that she is a liaison with H&R Block and is reaching out to offer any assistance in filing taxes. If we examine Alice's profile, everything mentioned lines up with her public presence. In fact, she looks like a very reputable person! She attended a prestigious university, has had a prolific career, and has an enticing professional summary.
While we could review her education and past work experience with her LinkedIn profile, there is certainly other demographic, geographic, or personal information that we wouldn’t see online. So let's talk about Alice on a more personal level.
She is 49 years old, she lives in San Diego, California, and her favorite color is black (to match the business suits she wears). On top of that, she was born on July 1, 1972, and her zodiac sign is Cancer. She drives a 2005 Lexus LS to visit her mother (maiden name "Weaver"), and in case you ever need to reach her, her cell phone number is 909-722-3198.
She has an O+ blood type and has a Mastercard that expires in February 2025. Alice owns an iPhone, but when she is on her computer, she uses the Firefox Web browser.
We never would have the need for that information, or ask any questions pertaining to it — but if we did, Alice would have all the answers. It is her life story, after all!
You might be wondering how I know so much about Alice. Well, that's because I made her up.
Alice doesn't exist, and all her background information has been randomly computer generated to make her character all the more convincing. Her entire persona was artificially created with free, publicly accessible online tools that anyone can use.
Faking People (For Real)
It is surprisingly easy to come up with a whole identity for a fake person in this day and age. In all reality, there are online tools that do all the hard work for you. Social engineering is just too easy for scammers and cybercriminals.
Perpetrators can use Fake Name Generator to rapidly create an entire persona for fake but believable characters — just like I did with Alice Dupree.
Once all this background information has been generated and supplied for a budding scammer, they simply need a believable profile picture to replace the default gray silhouette.
If it wasn't already easy enough, cybercriminals and scammers can not only generate an entire person's history, but also their appearance with another online tool like This Person Does Not Exist.
How Can You Tell What Is Real?
Maybe an observant eye might notice a few telltales that this Alice character is a randomly generated persona. The profile picture gained from This Person Does Not Exist might have the strongest indicators:
The person's gaze is directly into the camera.
They might have odd or unusual traits.
Accessories like hats or glasses or even hair strands might fade in and out.
The side edges background may have very strange figures.
You may have noticed our so-called Alice is wearing earrings, but the left looks a bit more distorted than the right.

But how can someone defend against falling for Internet scams like this? Whenever possible, if an individual can do their due diligence by reaching out to the alleged company or school this persona is/was a part of, they can determine if this is legitimate.
Examining their profile might also reveal that the account has little to no activity. Social media sites may prune or remove accounts with little to no activity, in which case scammers really need to spend time to keep up the charade and look as realistic as possible.
If there is any suspicion you received a message from a fake persona, it is worth doing some online research to determine if this person is who they say they are – or if they exist at all.
For some semblance of "training your eyes" to detect fake computer-generated profile pictures, check out Which Face Is Real. Bear in mind some of the indicators discussed: centered eyes, blurry backgrounds, fading glasses or hair strands, and mismatched earrings. When lies and cons are at your door, inbox, or direct messages, you are the front line of defense.
About the Author
You May Also Like




