
News, news analysis, and commentary on the latest trends in cybersecurity technology.
What Security Controls Do I Need for My Kubernetes Cluster?
This Tech Tip offers some security controls to embed in your organization's CI/CD pipeline to protect Kubernetes clusters and corporate networks.

Question: What are some security controls I need for my Kubernetes cluster?
Ratan Tipirmeni, president and CEO, Tigera: Security controls for your Kubernetes clusters should help you prevent, detect and mitigate breaches. Kubernetes clusters are automatically refreshed as new builds are available, so it’s important that security controls are embedded in your continuous integration/continuous deployment (CI/CD) pipeline as soon as the application artifacts are built.
You should have the following build and deploy time controls to secure your Kubernetes clusters:
Scanning registries, both public and private, on a continuous basis. These registries make up your software supply chain.
An admission controller that actively enforces security policies to control the deployment of images.
Once you have secured your software supply chain, the next step is to make sure that your Kubernetes infrastructure and control plane are deployed with a hardened configuration.
You should include the following deploy time controls:
Assess your configuration security (images, containers, Docker runtime, worker nodes and Kubernetes API server) against industry benchmarks such as CIS
Kubernetes Security Posture Management (KSPM) to assess the configuration of your Kubernetes cluster
Embed your compliance controls as security policies as part of your deployment pipeline
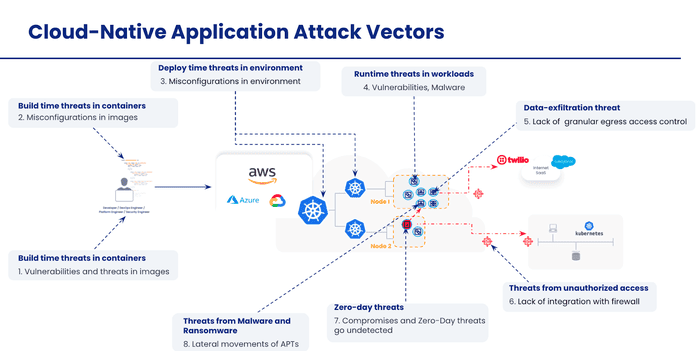
To protect your Kubernetes clusters at runtime, you should implement zero-trust security controls to reduce the attack surface. This gives your application teams more time to mitigate vulnerabilities.
In Kubernetes clusters, by default all workloads can communicate with each other, and they can also communicate anywhere outside the cluster. A zero-trust security architecture explicitly allows all legitimate traffic and denies everything else.
Source: Tigera
Zero-trust security for Kubernetes clusters should include zero-trust workload access controls to establish which services can communicate externally (and which external resources can access services in the cluster), limiting the blast radius of potential attacks with microsegmentation, and enabling firewall protection at granular workload levels to prevent unauthorized access.
And finally, you need runtime threat defense capabilities that can detect both network and container-based threats. For known threats, you should ingest threat feeds of known vulnerabilities and threats. In addition, you should use machine learning to identify anomalies in your workload behavior to identify indicators of compromise or attacks.
About the Author
You May Also Like

