Security Via Consensus: Developing the CIS Benchmarks™
Understand the CIS Benchmarks'™ community-consensus development process that helps ensure they provide comprehensive guidance on Internet security.
February 5, 2024

By Mia LaVada, product manager, Center for Internet Security
The Center for Internet Security® (CIS®) released the first CIS Benchmark™ 24 years ago, in 2000. Fast forward to today, and you can now use more than 100 CIS Benchmarks to protect your systems across more than 25 product vendor families.
None of this would have been possible without the participation of our global community of experts and volunteers. The CIS Benchmarks Communities beat as the heart of an ongoing effort to provide security-hardening recommendations across industries and technologies.
What Are the CIS Benchmarks?
The CIS Benchmarks consist of vendor-neutral security recommendations for specific operating systems (OSes), servers, mobile devices, and other technologies. They are available as PDFs, which are freely available to download from the CIS website, and in additional file formats (including XCCDF, Word, and Excel) for CIS SecureSuite® Members.
The CIS Benchmarks don't just lay out what you need to do to configure a system. They also provide context on each security recommendation, including why you want to implement a recommendation (the rationale), what the security benefits of implementation are (the impact), and how each recommendation maps to the CIS Critical Security Controls® (CIS Controls®). The CIS Controls offer prioritized and prescriptive security best practices that simplify the process of strengthening your cybersecurity posture against common cyber threats.
Several industry standards and regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Federal Information Security Management Act (FISMA), reference the Benchmarks. This helps streamline compliance efforts to avoid duplicative work.
Many Benchmarks support different configuration profiles so that you can harden your technologies to a level that works for your organization. Level 1 consists of base recommendations that you can use to securely configure your technologies without significantly affecting their performance. Level 2 consists of defense-in-depth recommendations intended for environments or use cases where security is paramount. This configuration profile could affect the performance of your systems. Finally, the STIG profile provides recommendations that are specific to the Security Technical Implementation Guides (STIGs) developed by the Defense Information Systems Agency (DISA). The STIG profile identifies areas of overlap with the Level 1 and Level 2 configuration profiles and references the DISA STIG information.
Inside the CIS Benchmarks Development Process
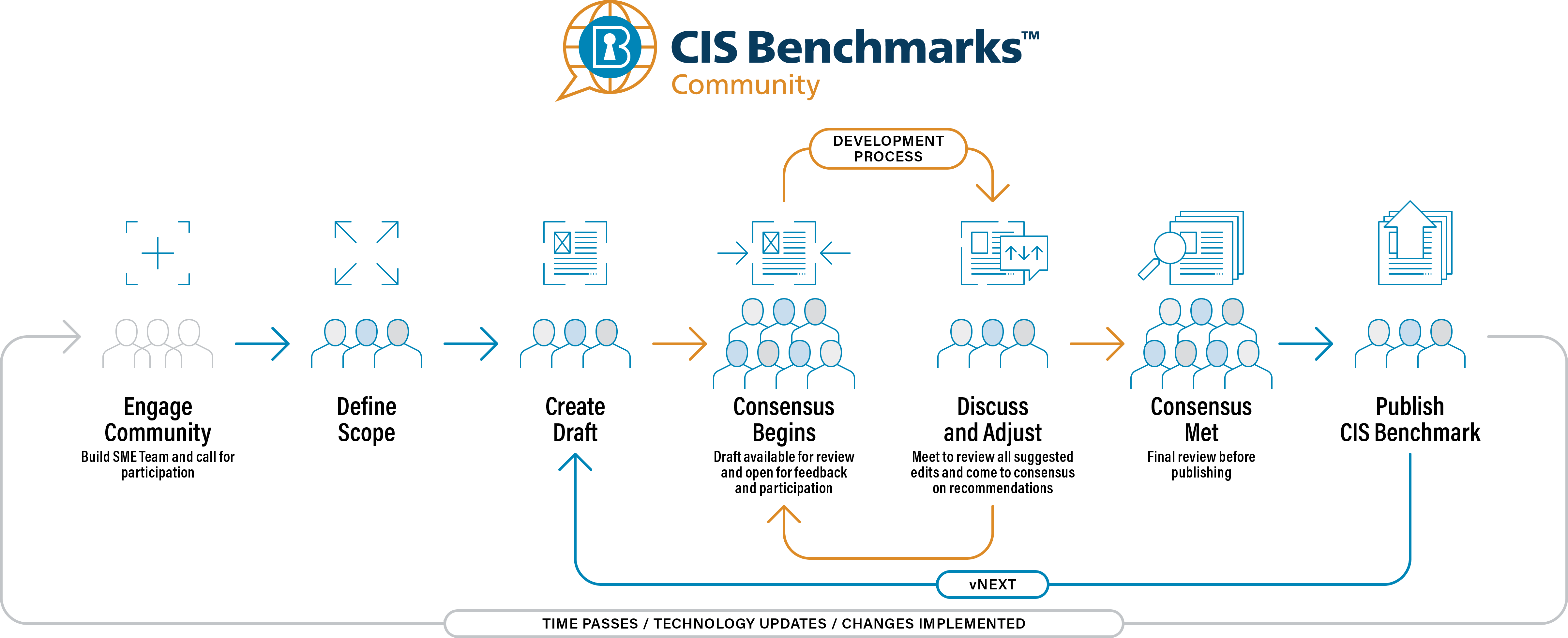
A unique community-consensus process drives development of the CIS Benchmarks on CIS WorkBench, a centralized development platform that's home to the CIS Benchmarks Communities along with CIS SecureSuite Membership resources, tools, and more. Anyone who wants to help develop the Benchmarks can join the CIS Benchmarks Communities and work with like-minded subject-matter experts (SMEs), vendors, technical writers, and SecureSuite Members around the world. Together with leads from CIS, these individuals use their real-world experience and expertise to develop the CIS Benchmarks on an ongoing basis.
The typical development process uses tickets and discussion threads to facilitate dialogue among the Benchmarks Communities until participants reach a consensus on proposed recommendations and working drafts. Here's what the typical development process looks like:
The initial stage defines the scope of a Benchmark. With that scope in mind, SMEs and the CIS lead launch a discussion in a Benchmarks Community and lead the creation and testing of working drafts to produce an initial draft.
CIS announces the availability of the initial draft in the Benchmarks Community. This initiates the main part of the consensus process by inviting folks to review, test, and provide feedback.
After receiving and reviewing the feedback, the CIS lead for the Benchmarks Community and SMEs discuss and adjust the Benchmark as necessary.
CIS makes a final call for participation on the draft in the Benchmarks Community, a period that lasts about two weeks.
After the CIS lead and SMEs address final feedback, CIS publishes the final CIS Benchmark and makes it publicly available online in PDF format for non-commercial use.
Source: CIS
Join a Benchmarks Community Today!
Each CIS Benchmark reflects the expertise and input of volunteers all over the world. Their efforts ensure that the security recommendations represent comprehensive guidance.
Want to play your part in the Benchmarks development process? Learn how to get started.
About the Author

Mia LaVada is a product manager for the CIS Benchmarks and Cloud products at the Center for Internet Security (CIS). She has been with CIS since June 2019. As a strong believer in the power of community, LaVada regularly works with CIS Members to help ensure CIS addresses the needs of the global cybersecurity community. She’s also particularly passionate about finding solutions to further secure the ever-changing cloud ecosystem.
Read more about:
Sponsor Resource CenterYou May Also Like
.png?width=300&auto=webp&quality=80&disable=upscale)


