Connect the Dots with Genetic Algorithms on CNAPP
Cloud-native application protection platforms can apply machine-learning algorithms on cloud data to identify accounts with abnormal permissions and uncover potential threats.

Over the past decade, we've seen a dramatic uptick in cloud migrations. On-premises solutions are becoming a thing of the past, and the cloud is becoming the default in the present. But why cloud, and why now?
Many organizations are currently undergoing a digital transformation. Much of this is expedited, due to the COVID-19 pandemic. Moving to the cloud offers numerous benefits—scalability, agility, and cost reduction being some of the most significant. Legacy solutions require setting up more physical servers, which increases complexity and operational effort, leading to higher costs. Meanwhile, cloud lets us do everything—and more—with just a few clicks.
The move to the cloud poses new challenges. One of the simplest ways attackers can get to an organization's crown jewels in the cloud is by clearing attack paths through a combination of network access and permissions. In what's quickly becoming a go-to method, many attackers use cloud-native privilege escalation techniques like PassRole to gain privileged access. The smallest drift in an environment can open up these attack paths in seconds, creating utter madness for a business. With the right privileges, data exfiltration takes mere moments and is almost impossible to detect.
To expose these types of attack paths, DevOps and security teams can use machine-learning capabilities embedded in a cloud-native application protection platform (CNAPP) solution to detect abnormal permissions, correlate all the signals, and search for privileges that collide with public exposures and vulnerabilities.
One of the problems we've seen most frequently, and one that's difficult to track and catch, is extra permissions being granted to many users within a tenant. In these cases, most permissions are unused, and attackers can take advantage. A CNAPP solution can detect abnormal permissions of identities within a tenant using specific machine learning methodologies.
Our definition for "abnormal" is simple: actionable + most risky = abnormal. For instance, when users in a given group each have more or less the same set of permissions in an environment, but one user has extra permissions in another environment, we consider the extra permissions abnormal.
In case of outliers over data that consists of a large number of features, the native machine learning models would usually be PCA, DBSCAN, LOF, or Isolation Forest. However, we discovered that the perfect model is a genetic algorithm. Genetic algorithms aim to detect mutations within a series of genes.
How exactly do we do that? Let’s have a look at a specific example.
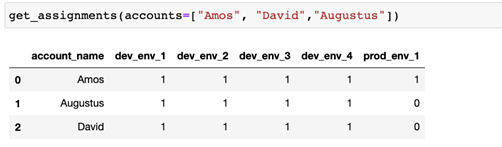
In the table above, we can see that Amos has some extra permission in the production environment, which we consider abnormal. Let's now convert that graph to a DNA vector (DNA assignment).
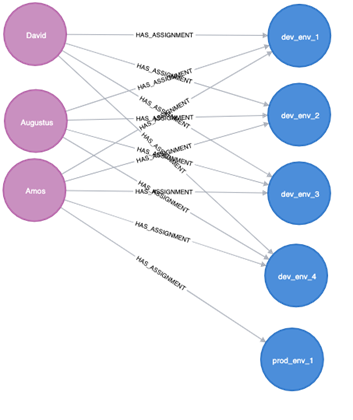
We see here that Amos has mutations. The goal is to search for close communities that have extra important permissions—only then may it be considered an anomaly. Also, if the communities are far from each other, it's not necessarily anomalous.
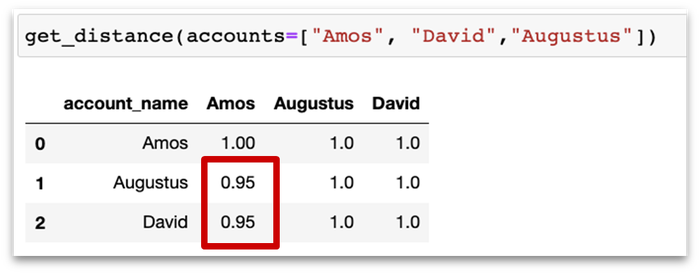
After more in-depth ML calculations to eliminate false positives, you'll end up with a genetic algorithm that can help detect outliers with abnormal permissions. It's fast, simple, and effective. Trying to perform this kind of analysis with a legacy approach would require a massive manual effort to first understand the business impact of each permission, and then detect the excessive permissions. On the other hand, an ML-based approach suggests a self-learning method without the need to understand each and every permission, helping to expedite the process.
With cloud threats constantly evolving, machine/deep-learning detection-based methods are going to become a necessity when evaluating CNAPP solutions. Don't wait for that next drift to activate a chain of catastrophic events—get ahead of the curve of detecting your next breach with the power of machine learning.
Read more Partner Perspectives from Zscaler.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




