Who Is Responsible for Protecting Physical Security Systems From Cyberattacks?
It's a question that continues to engage debate, as the majority of new physical security devices being installed are now connected to a network. While this offers myriad benefits, it also raises the question: Who is responsible for their cybersecurity?
In recent years it has become more obvious that physical security systems are dependent on IT and vulnerable to cyberattacks.
In 2007, the movie Live Free or Die Hard showed how a group of criminals were able to control traffic systems and bring Washington DC and the stock market to a standstill. In the film Johnny English Strikes Again (2018), all the trains in the UK are directed to Bristol.
These movies are very much based in reality. In 2016, the BSIA warned us of the risks and recommended that "end users of IP connected CCTV systems should also ensure that they have comprehensive cyber security and information security policies in place." In 2019 a Norwegian company spent £45 million to restore its computer systems, factory machinery and building systems following a ransomware attack on its 170 sites and over 35,000 staff.
While these were operational technology systems, the 2019 BBC series The Capture demonstrated how CCTV could be hacked to convince police and security services' investigations that a lead suspect was guilty by adjusting the time frame in the system. Once again, this television 'drama' is now the unfortunate reality. The "IFSEC Global Video Surveillance Report 2020" found that 76% of respondents were concerned about the cybersecurity of surveillance systems.
For those who haven't noticed this issue, it would be wise to take stock. It is now likely that the physical security system can be attacked. As far back as 2014, the UK CPNI stated that it was possible. Cybersecurity has progressed very rapidly since then, hence a physical security lead should be engaging with the cybersecurity team to work with them — and vice versa.
Whose Responsibility Is It?
But who is responsible for protecting them from these attacks?
Is it the owner of the system? For some this is clearly the physical security lead. After all, they or their predecessor purchased or recommended it, didn't they?
But now they have a problem as they have heard the systems are not secure. Are they accountable to the business if an attacker gains access through the CCTV system to the IT corporate email and convinces the finance director to authorize an invoice costing thousands of pounds?
Or is the head of IT who authorized the CCTV system and gave responsibility for its day-to-day management to the head of physical security responsible? Or perhaps it is the head of cybersecurity who is an expert in the field and has implemented a range of controls on the network to mitigate cyberattacks? Surely this person is the one who is responsible?
Well, maybe.
A poll I conducted in November with a small group of 14 security professionals indicated 69% think physical security systems are cyber. When a ransom attack is mounted and successful, whose job is then at risk — the CEO/CIO/CISO or CSO? The board may decide that one or more people should be fired.
When you want to pay a ransom — who does it? This is a gray area, but once these systems are hacked the responsibilities will become clearer and some will lose their jobs.
Are there easy answers? Is one person responsible? Or, as some would argue, isn't everyone responsible for security?
In risk management there are RACI (Responsible, Accountable, Consulted, Informed) tables which indicate that one person is responsible for performing the work effort and management of the risk. This is usually the system or business unit owner. But that might be hard to identify for some people in large organizations.
Other business functions are meant to support that person and offer their expertise and technological services. If you occupy any of these roles, then it is important to ensure you are protecting the systems from attack, whether you are directly responsible or not. If you see a person in need of help it is vital to work with them — for their sake and the success of the business.
Whoever you believe is the most responsible for protecting physical security systems from cyberattacks, ultimately it must be a cross-functional team effort.
(Column continues on next page--see link below.)
The Debate Continues
In December 2020, I conducted a poll on LinkedIn to further understand what the views of security and IT professionals are. I was very encouraged by the interest and comments that it raised.
Over one week there were 81 votes from across all areas of security and IT. My special thanks to IFSEC Global, Mike Gips (Principal, Global Insights in Professional Security) who is a global leader in security research, and Rollo Davies, Managing editor of TPSO magazine, who reshared the poll. This enabled me to receive a range of perspectives that I simply could not have gained on my own.
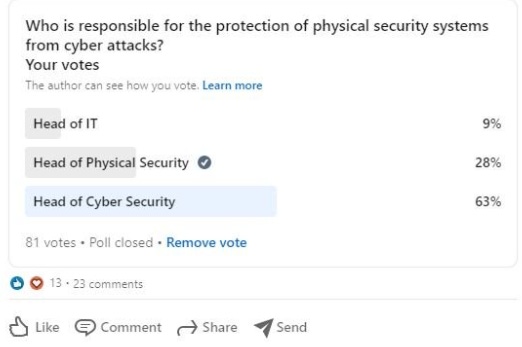
Twenty-eight percent voted for head of physical security, suggesting that the system owner is responsible (assuming this is physical security/FM etc.) and should seek support from the others. I think this is also what ISACA would advise from my studies of the CRISC materials. The head of IT allocates responsibility to individual business units and the system owner is then responsible. Similarly, the ASIS CSO Organisational Standard explains that the CSO is responsible for all security risks and can delegate "some" accountability to heads of business units who are supported by the appropriate organization's security team. Hence the physical security lead should look for support from the head of cybersecurity to provide specialized services that reduce the risk.
Brian Allen (Cyber Advisory, EY) added his comments to this: "The system owner, CSO in this case, being physical security equipment, is the system owner, with the system's state being in the cyber environment. I'd say the CSO is the system owner and whomever has responsibility in protecting assets in the digital environment, would be responsible for those protections to the limits the stakeholder (CSO) desires."
Figure 1: 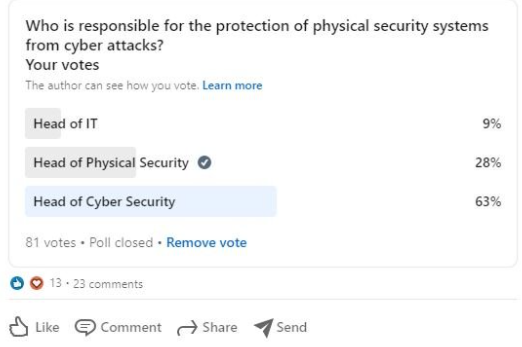
Sixty-three percent voted for head of cybersecurity, with responses including both senior physical and cyber security professionals. This is most interesting and, in some ways, expected. It reflects my earlier findings that 69% think physical systems are in fact cyber.
Over the years I have worked in the converged arena, I often meet people from both areas who are clear that physical security professionals are not experts in cybersecurity and should not try to manage this risk. Others, not surprisingly, see it as a highly complex field which they have worked in for many years and now want to help protect IoT and physical security devices. But as colleagues in IoT security are often specialists, it remains obvious that many of these systems are unprotected. I say this because if the majority believe quite reasonably that the head of cybersecurity is responsible, whereas in reality the head of physical security is, we have a problem.
Few heads of physical security in fact do know how to cyber-protect their systems and think the head of cybersecurity is doing it. This is a problem when the cyber department is in fact busy protecting the network from new risks such as the security of their own solutions (as SolarWinds evidences), of ransomware and working from home. In many instances, the last thing the cybersecurity head is worried about is CCTV and BMS.
How much time does the typical CISO/head of cybersecurity devote to this? Operational technologies are getting more attention with increasing attacks on the energy sector and the recent ransomware attack on Dusseldorf University Hospital that caused the tragic death of a patient. But if the official view is that it is the responsibility of physical security, then the industry must wake up to this and take action.
Nine percent voted for the head of IT. Clearly, some leading IT and security professionals believe that the head of IT has overall accountability and responsibility. They would then delegate the day-to-day running of the system to the business unit. This answer is of course reasonable and indicates that the business recognizes that the issue of cyber security of all systems is significant.
Peter also indicated that the IT systems should self-protect and that by 2024 the CEO would become personally responsible. We know that some of the more advanced CCTV systems self-protect, but sadly not the majority!
I didn't give the option of a CSO in the poll, partly because there are few senior roles like this and I wanted to see the answers to physical or cyber. Though it would have been interesting to see who would have voted for the CSO. The CSO, for instance, can delegate this to the head of physical or cybersecurity.
If it is evidently a challenge for the physical security lead to fully understand cybersecurity, then it makes real sense to collaborate and form cross-functional teams to address these common risks. And, as we have demonstrated at IFSEC's Converged Security Centre, it is even more important to monitor real time attacks on these systems if we are to identify the risk in time. How can the head of physical security honestly expect to see these attacks if there are no real-time cybersecurity monitoring technologies in the control room?
This is precisely why we need converged security operations centers and to move into the digital age. Without convergence technologies, the officers in a control room will not know if the camera is down from a cyber or physical attack.
Not taking anything away from Bruce Willis here, but if he could work with the hacker to save the stock market from a hostile takeover in Live Free or Die Hard, why on earth can't we?
James Willison is the founder of Unified Security Ltd, the Project Advisor to the IFSEC Converged Security Centre and Co Chair of the Smart Built Working Environment Group, IoTSF. James was also listed amongst the IFSEC Global Top Influencers in Security & Fire 2020.
This story first appeared on IFSEC Global, part of the Informa Network, and a leading provider of news, features, videos, and white papers for the security and fire industry. IFSEC Global covers developments in long-established physical technologies — like video surveillance, access control, intruder/fire alarms, and guarding — and emerging innovations in cybersecurity, drones, smart buildings, home automation, the Internet of Things, and more.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




