Why You Should Be Using CISA's Catalog of Exploited Vulns
It's a great starting point for organizations that want to ride the wave of risk-based vulnerability management rather than drowning beneath it.

The Cybersecurity and Infrastructure Security Agency (CISA) recently issued Binding Operations Directive 22-01 aimed at reducing risk associated with actively exploited vulnerabilities. The directive was accompanied by a catalog of known exploited vulnerabilities maintained by CISA that includes mandatory remediation deadlines. Essentially, it means "fix these fast or else" for applicable agencies and organizations.
I think it's a smart move in the right direction by CISA. I'll explain why with some stats and charts from recent Cyentia Institute research.
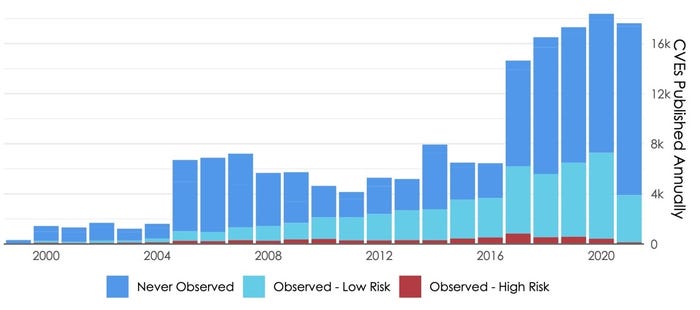
The chart from our joint "Prioritization to Prediction" research with Kenna Security demonstrates why CISA felt such a directive was needed. The number of vulnerabilities publicly reported and collected in the CVE List has risen dramatically over the years. 2021 wasn't yet done when we created this chart, so it doesn't show that last year was the first ever that topped 20,000 published vulnerabilities!
Some of this rising tide of vulnerabilities is tied to the trend popularized as software eating the world. Part stems from the struggle of writing secure code for all that software. But the primary cause of the surge of vulns circa 2017 is better reporting via an ever-growing list of CVE Numbering Authorities. Regardless of reasons, the practical outcome is security programs are overwhelmed by a constant flood of vulnerabilities to assess and remediate.
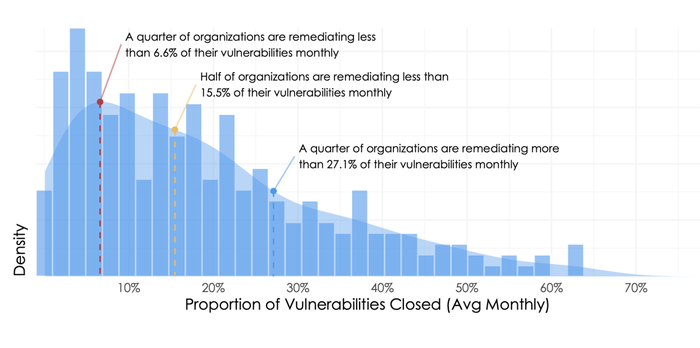
Unfortunately, many are drowning in that flood. According to the figure below, again from "Prioritization to Prediction Vol 8," most organizations remediate less than a quarter of the vulnerabilities across their environment on a monthly basis. If no new vulnerabilities emerged, they'd eventually catch up. But a glance back at Figure 1 reminds us, there's no rest for the weary in vulnerability management.
The one respite offered in the data we analyzed over the years is that organizations don't need to remediate all of their vulnerabilities. They just need to fix those that represent real risk. But how many is that?
You may have noticed the different colored segments back in Figure 1. The height of each bar corresponds to the number of vulnerabilities published. The light blue represents the proportion of published CVEs observed in production assets managed by the hundreds of organizations we studied. The red portion marks vulnerabilities with known exploit code or active exploits in the wild (aka "high risk"). Since remediation capacity is limited per Figure 2, doesn't it make sense to fix the red (exploited) ones first?
I think so too. And that's precisely why I said earlier that CISA made a smart move with BD 22-01. CISA's catalog of must-fix vulnerabilities doesn't claim (or need) to be exhaustive. It's focus is on those "that carry significant risk." As of this writing, the catalog contains 377 exploited vulnerabilities. That represents a tiny fraction (0.22%) of the ~170,000 vulnerabilities published on the CVE List. Is that too few? Too many? Spot on? Well, let's start with a simpler question: Does it represent all exploited vulnerabilities?
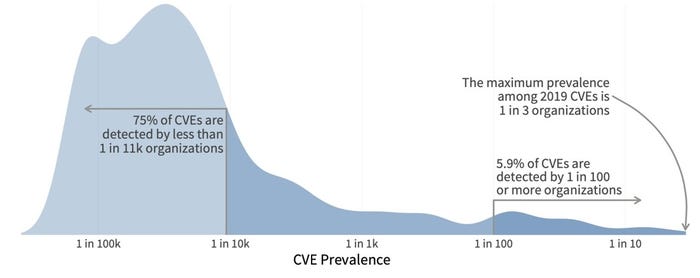
That's a hard no. The previous volume of "Prioritization to Prediction" found exploitation activity targeting 2.5% of all published CVEs. Based on that ratio, the catalog should be over 10x its current size. Before condemning the catalog, however, keep in mind that exploitation "in the wild" doesn't equate to widespread attacks targeting large numbers of organizations. One last chart should help clear that up and provide some useful statistics about the prevalence of exploitation activity.
For the sake of argument, let's say that any vulnerability registering exploit attempts against at least 1% of organizations represents a significant risk to your firm. About 6% of exploited CVEs cross that threshold, according to Figure 3.
Now some back-of-the-napkin math: If 2.5% of CVEs are exploited in the wild and 6% of those trip our risk threshold, then 0.15% (2.5% x 6%) represent significant risk to our organization. That's remarkably close to (and below) the percentage (0.22%) of CVEs in CISA's catalog. And most important — and encouraging — it's a lot less than the typical remediation capacity (~15%) of most organizations.
So it all comes back to the organization's ability to identify and prioritize the riskiest of vulnerabilities. Is CISA's catalog the end-all-be-all of avoiding exploitation? No. But it's a great starting point for organizations that want to ride the wave of risk-based vulnerability management rather than drowning beneath it.
About the Author
You May Also Like