USB Devices Still a Threat to Businesses, Kaspersky Finds
The use of removable storage media to deliver malware is declining, but threat actors are putting coin miners into USB devices and targeting emerging areas, a new study by Kaspersky finds.

In recent years, cloud services such as Dropbox have taken on a larger share of file storage and transfer tasks, but USB devices are still being used around the world and continue to be targeted by bad actors who see them as an avenue into a victim's systems, according to researchers with Kaspersky Lab.
Company researchers note in a blog post that data from 2017 found that about every 12 months, one in four users around the globe are impacted by what they call a "local" cyber threat detected directly on the user's compute, with the majority of attacks occurring in emerging markets such as Asia, South America and Africa. These attacks include ones caused by USB devices and other removable media.
Local threats are those that are detected directly on a user's computer, according to researchers.
(Source: Kaspersky)
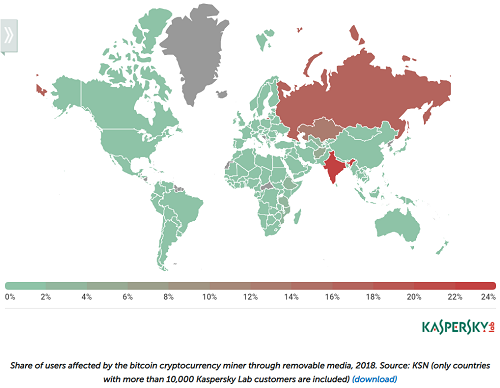
In addition, many of the infections from USB devices were aimed at spreading malware for mining cryptocurrencies such as Bitcoin and Monero, with infections going back as far as 2015. The most popular bitcoin miner, Trojan.Win64.Miner.all, targeted one in ten of all users who were hit by removable media infections in 2018, and the rate is growing. This year, the miner was found in 9.22% of infections; it was 6.7% last year and 4.2% in 2016, according to Kaspersky. (See Cryptomining Malware Continues to Surge as Cybercriminals Cash In.)
The researchers also noted the Windows LNK family of Trojans, as well as the Stuxnet exploit from 2010, CVE-2010-2568, which is still in the top ten exploits spread through USB devices. In addition, Dark Tequila, banking malware first reported in August, also has been spread primarily through USB devices. The malware targets corporate victims and consumers in Mexico and has been around since at least 2013.
For enterprises, the risks associated with USB drives are declining but still there.
The cloud services and a greater awareness of security risks associated with the devices -- any good security solution will scan removable media for malware before enabling the data to be transferred -- are helping to reduce the threat, Kaspersky researchers told Security Now. However, large numbers of USB devices are still distributed every year at places like trade shows as giveaways that are used in both businesses and homes. Organizations without the right security in place or with workers who have not yet been educated about the risk USB drives post remain vulnerable to attacks through the devices, they said.
Some companies already have taken steps to address the issue. IBM earlier this year banned all USB drives and other portable storage devices -- including SD cards and flash drives -- for its employees in an attempt to improve security. Company officials instead want employees to use IBM's cloud-based file and data-sharing service. (See IBM's USB Ban Earns Some Praise, Some Skepticism.)
The number of threats detected on USB devices has declined over the past four years, with the ratio between a user affected by such a threat and the total number of such threats detected dropping from 1:42 to an estimated 1:22 this year. By comparison, the risk by web-borne attacks is significantly higher. Last year, Kaspersky Lab detected 113.8 million likely removable media threats and almost 1.2 billion attacks launched from online resources, researchers said.
"In light of this, it can be easy to overlook the enduring risks presented by removable media, even though around four million users worldwide will be infected in this way in 2018," the researchers wrote in the blog post.
Cybercriminals like to use USB devices to attack networks not connected to the Internet, including ones that power critical national infrastructure, such as the Stuxnet campaign in 2009 and 2010 that targeted Iran's nuclear facilities. Criminal groups like HackingTeam and Equation Group have use USB devices to deliver malware.
Using USB devices to spread cryptomining malware is uncommon, but it's successful enough so that attackers will continue to use them, researchers told Security Now.
Cybercriminals using removable devices to spread their malware are particularly targeting users in emerging regions. According to Kaspersky analysts, about two thirds of users in some of these countries were victims of a local threat incident -- including drive-root malware infections from removable media -- while fewer than one in four people in developed economies have been victimized.
The countries hardest hit by the LNK exploit being delivered through such devices this year included Vietnam, Algeria and India. The US, Japan and some European countries experienced some attacks.
Threat actors continue to use removable devices to spread malware and even though their use is dropping, the rate of decline is slowing. Combined with the fact that USB devices continue to be widely shipped and used, the risk that comes with them will be around into the future, the researchers said.
Related posts:
— Jeffrey Burt is a long-time tech journalist whose work has appeared in such publications as eWEEK, The Next Platform and Channelnomics.
Read more about:
Security NowAbout the Author
You May Also Like




