Senators Slam Online Advertisers As 'Malvertising' Spikes
Complex ecosystem fails to arrest rise in malicious advertising, information security experts warn Congress.

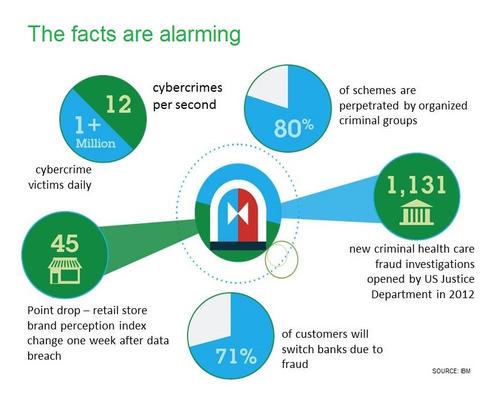
10 Ways To Fight Digital Theft & Fraud
10 Ways To Fight Digital Theft & Fraud (Click image for larger view and slideshow.)
The quantity of "malvertising" -- malware distributed via legitimate advertising networks -- has doubled in the past year, and the online advertising industry is failing to blunt its impact on consumers.
That's the assessment of a 47-page Senate report, "Online Advertising and Hidden Hazards to Consumer Security and Data Privacy," released Wednesday. The report cited statistics from the Online Trust Alliance, which saw the incidence of malvertising increase by more than 200% in 2013, resulting in an estimated 12.4 billion malicious advertising impressions.
Online advertising is big business: In 2013, related revenues hit $42.8 billion, surpassing broadcast television advertising revenues for the first time in history.
But at a Senate homeland security and governmental affairs committee hearing Thursday, Craig D. Spiezle, president and executive director of the Online Trust Alliance, said the increase in revenues has been accompanied by a rise in malvertising campaign operators successfully sneaking onto legitimate sites.
"This past January Yahoo experienced an incident resulting in over 300,000 malicious impressions in a single hour," he told the committee. "Approximately 9% or 27,000 unsuspecting users were compromised. For these consumers, the infection rate was 100%." He added that other sites that have served up malicious advertising campaigns include Expedia, Facebook, Google, Microsoft, The New York Times, and The Wall Street Journal.
[Cisco's John Chambers is critical of government overreach when it comes to surveillance. Read Cisco CEO: US Should Reform Surveillance Rules.]
Yahoo's VP of information security, Alex Stamos, failed to mention Yahoo's recent malvertising breach when he too addressed the committee Thursday, instead focusing on the bigger picture. "We successfully block the vast majority of malicious or deceptive advertisements with which bad actors attack our network, and we always strive to defeat those who would compromise our customers' security," he said.
In a phone interview, Elias Manousos, CEO of RiskIQ -- which helps sponsor the Online Trust Alliance -- said one explanation for the increase in malvertising is the advertising industry's introduction of bulk ad-buying practices, or "programmatic buying." While this makes buying and selling ads easier, it's also created a difficult-to-police supply chain in which buyers and sellers often no longer know each other.
"The ad-vetting process is really broken in this change to the ecosystem," said Manousos. "This programmatic ad buying is also very complex -- and one thing we know about security is that security and complexity don't go together."
Arguably, not every site's security has suffered as a result of these practices. "Sites like Facebook have been immune to these attacks because they don't participate in this programmatic buying -- there are direct relationships there between the advertisers and the users on the site," Manousos said.
Some online advertising organizations also have programs designed to address malvertising, although they often lack industry-wide buy-in. Earlier this month, for example, AOL, Facebook, Google, and Twitter launched Trust in Ads, which promises to bring "awareness to consumers about online ad-related scams and deceptive activities" as well as to crowdsource the detection of bad ads -- but only for those four sites.
Figure 1: 
"We kicked off this effort by identifying abusive practices in the tech support advertising space. Scam advertisers often present themselves as official representatives of companies of products for which users seek support," Google senior product manager George Salem told the committee. (As with Yahoo's representative, Salem declined to detail any of the malvertising campaigns that succeeded in infiltrating Google's advertising network.)
OTA's Spiezle told the committee that an industry focus on consumer education and relying on consumers to sound malvertising warnings was inadequate. "Unfortunately no amount of consumer education can help when users visit trusted websites that are serving malvertising," he said. "Focusing on education after the fact is like the auto industry telling accident victims whom to call after an accident from a previously known manufacturing defect, instead of building security features in the cars they sell and profit from."
While some malvertising relies on social-engineering attacks -- for example, to trick a user into thinking his PC has been infected by a virus -- an increasing quantity of malvertising uses drive-by malware attacks to automatically infect vulnerable PCs with malware. The number of drive-by malware attacks launched via online advertising also increased 41% in 2012 and 190% in 2013.
To help blunt the rise in malvertising, Spiezle recommended that Congress introduce legislation "not unlike state data breach laws, requiring mandatory notification, data sharing, and remediation to those who have been harmed." He also referenced his organization's anti-malvertising guidelines for the ad supply chain, which begin by arguing that the industry must create an accreditation/authentication process for new clients and
agencies and also report bad actors to both law enforcement agencies and industry groups.
Similarly, the Senate report recommends that the online advertising industry issue stronger security guidelines for members, as well as share more information on threats. The report also calls for more frequent spot-checks of online advertising content to better catch malvertising outbreaks, and the development of "circuit breakers" to detect malvertising before it reaches consumers.
Otherwise, the committee has promised to spell out those responsibilities in new legislation: "If sophisticated commercial entities do not take steps to further protect consumers, regulatory or legislative change may be needed so that such entities are incentivized to increase security for advertisements run through their systems," the report reads.
Last week, committee member Sen. John McCain (R-AZ) likewise warned in a statement that Congress must "make sure standards and rules exist to ensure consumers do not have to be more tech savvy than cyber criminals to stay safe online." At the hearing, meanwhile, he laid into the industry's approach to regulating itself, noting that this had failed to produce effective guidance or clear standards for online advertising security or prevent the emergence -- or timely disavowal -- of such aggressive advertising techniques as history sniffing.
Intentions aside, Congress has a poor track record of passing any legislation that relates to privacy or data security. Notably, the Do Not Track initiative has stalled -- as the Senate report notes, with advertisers and consumer groups unable to agree on even a definition of what constitutes tracking -- and after years of debate, Congress has failed to pass any cyber security legislation or even a national data breach notification law. Meanwhile, President Obama's 2012 Privacy Bill of Rights lacks the force of law and is thus voluntary. Perhaps unsurprisingly, advertisers haven't rushed to sign up.
Cue the current state of affairs: "The one party who is least capable of monitoring and regulating advertising -- the consumer -- is the party who currently bears the full brunt of the losses when the system fails," the Senate report states.
Cyber criminals wielding advanced persistent threats have plenty of innovative techniques to evade network and endpoint defenses. It's scary stuff, and ignorance is definitely not bliss. How to fight back? Think security that's distributed, stratified, and adaptive. Read our Advanced Attacks Demand New Defenses report today. (Free registration required.)
About the Author
You May Also Like




