
News, news analysis, and commentary on the latest trends in cybersecurity technology.
NIST Commits to Plan to Resume NVD Work
The agency aims to burn down the backlog of vulnerabilities waiting to be added to the National Vulnerabilities Database via additional funding, third-party contract, and a partnership with CISA.
June 4, 2024

More than 100 days after the National Vulnerability Database all but ceased validating the severity of vulnerability reports, the US National Institute of Standards and Technology (NIST) has come up with a plan to get back on track.
On May 29, NIST announced that the agency had awarded a contract to support the future processing of vulnerabilities to "allow us to return to the processing rates we maintained ... within the next few months." It also partnered with the Cybersecurity and Infrastructure Security Agency (CISA) to reduce the backlog by Sept. 30, the end of the US government's fiscal year, and is working on updating technology and modifying its process to handle the greater number of vulnerabilities disclosed every year, the agency said in a status update.
The key to taming the backlog will be to take a multipronged approach and work with both public- and private-sector participants to satisfy future needs, says Matt Scholl, chief of the Computer Security Division at NIST's Information Technology Lab.
"Once we have restored our capacity, NIST will continue working with the CVE board, the CNAs [CVE numbering authorities], FIRST [Forum for Incident Response and Security Teams], and the vulnerability management community to update any needed data specifications, coordinate transitions to new specs, and identify areas for improvement," he says. "We plan to identify processes that will result in a 'better NVD' to include the use of automation, tooling, participation, and updated standards and data specifications."
The origin of the problem that led to the bottleneck, however, remains largely a mystery. In mid-February, NIST, which maintains the National Vulnerability Database, all but stopped processing new vulnerabilities, citing a "perfect storm" of challenges. The agency typically enriches new vulnerabilities reported in the Common Vulnerabilities and Exposures (CVE) process with additional information or by verifying existing information, such as the product affected, assigning a Common Weakness Enumeration (CWE) identifier, and calculating impact and exploitability metrics.
Fast-Growing Flaws Meet Slow-Changing Government
NIST faces an exponentially growing problem. Following the removal of bottlenecks in the process of assigning CVE identifiers in 2017, the number of vulnerabilities disclosed each year with an associated identifier has taken off. In 2016, fewer than 6,500 vulnerabilities were disclosed. The following year, the number jumped to more than 14,600 and has grown every year after that. This year, the tide of vulnerabilities is on track to surpass 36,000.
The quickly increasing flood of issues has become an issue not just for defenders who want to apply necessary software patches, but also for threat-information providers that want to make sense of the deluge, says Josh Bressers, vice president of security at Anchore.
"The way vulnerabilities used to work isn't how they work anymore," he says. "The sheer volume of CVEs, the amount of automated tooling, and the number of organizations paying attention is larger than anyone could have imagined 20 years ago."
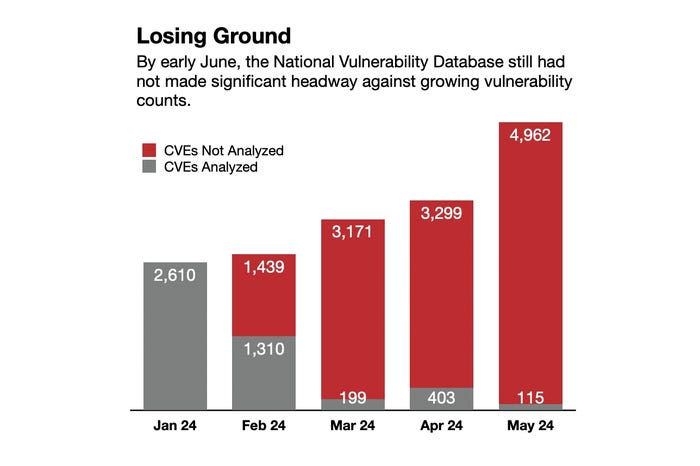
As the monthly vulnerability counts climb, the NVD remains behind. Source: Robert Lemos, data from the NVD dashboard
NIST had been keeping up — until suddenly it wasn't. The agency has processed only 26% of the vulnerabilities disclosed so far this year, according to data from its dashboard. No one factor — neither the quickly growing workload nor a lack of people — led to the stop of vulnerability reviews, says NIST's Scholl.
"It is not one or the other but a combination of many pressures," he says. "Reductions in resources, coupled with the steady increase in vulnerabilities, were certainly the main causes for this interruption."
Are Community Solutions Viable?
NIST plans to work with the community to improve the process and explicitly mentioned working with CISA. Two months ago, CISA launched a project, dubbed CISA Vulnrichment, to add metadata to vulnerability information. The project aims to enrich vulnerability information with data from the Stakeholder-Specific Vulnerability Categorization (SSVC) analysis process.
Between the two efforts, the government agencies could come up with a workable solution, says Kaylin Trychon, vice president of marketing at Chainguard, a supply chain security firm. CISA has already triaged about 1,300 vulnerabilities (although nearly 18,000 vulnerabilities have been disclosed) and assigned CVEs since the beginning of 2024.
"When NIST is up and running, the hope is this data can make the process for triaging and scoring CVEs faster to burn through the backlog," Trychon says. "Again, this is another temporary solution, but it is encouraging to see the nation's cybersecurity arm jumping in with resources to help chip away at the larger problem."
Trychon and other cybersecurity industry professionals sent a letter to Congress in mid-April warning of a crisis in cybersecurity and urging them to restore the NVD to full operation. Whether that pressure helped NIST free up the resources is unclear.
Yet Trychon wonders whether the current effort will be enough. The government needs to raise the priority of the NVD and treat it as an essential service and critical infrastructure, she says. Current discussions have suggested that a nonprofit foundation could be established through a public-private partnership.
"In theory, this funding source would ensure that critical programs, such as the NVD, remain resourced appropriately, while giving a clear path for the private sector to contribute to the continuity of operations," Trychon says.
Anchore's Bressers remains concerned that short-term efforts may not be enough and that long-term efforts will falter.
"Everyone says how important and critical vulnerability information is, but I think the amount of interest and investment tells a different story," he says. "It is very difficult and thankless work."
About the Author
You May Also Like

