New Ransomware Data Is In: What's Happening and How to Fight Back
Be proactive about data defense. Start with the right data, leverage domain expertise, and create models that help you target the most critical vulnerabilities.

Ransomware is still on the rise. What can we do about it? There are three things you need to consider right now.
First, some context: The pandemic is slowing down, so why aren't the attacks slowing down? The pandemic fueled a stratospheric rise in both the sophistication and volume of attacks as threat actors capitalized on the often-hasty shift to remote work. Suddenly, millions of devices and users were outside perimeters and in survival mode. Easy targets.
But that was then. The world has adapted to the Everywhere Workplace. Most companies have begun to get their proverbial feet under them. Digital transformation is accelerating, and companies are starting to adopt cybersecurity protocols that are more appropriate for the current landscape.
Surely, that's enough to stem the flow of ransomware attacks. Right? Well, apparently not.
The Latest on Ransomware Threats
In a just-released "Ransomware Report for Q2/Q3," Ivanti reports yet another increase in vulnerabilities. The highlights (or perhaps I should say lowlights):
As of the third quarter of 2022, there are a total of 170 documented ransomware families actively seeking to exploit vulnerabilities.
10 new ransomware families emerged over the past two quarters.
18 ransomware vulnerabilities are missing from popular scanners.
Two new vulnerabilities are being effectively exploited by AvosLocker and Cerber ransomware.
706 vulnerabilities have become weaponized in the last two years alone.
A new weakness category (CWE) is contributing to ransomware vulnerabilities.
Despite the documented rise in ransomware vulnerabilities, there are still 124 vulnerabilities that haven't even been added to the CISA KEV catalog yet.
Healthcare, energy, and critical manufacturing are the worst-hit sectors, at a time when all three sectors are still reeling from the pandemic.
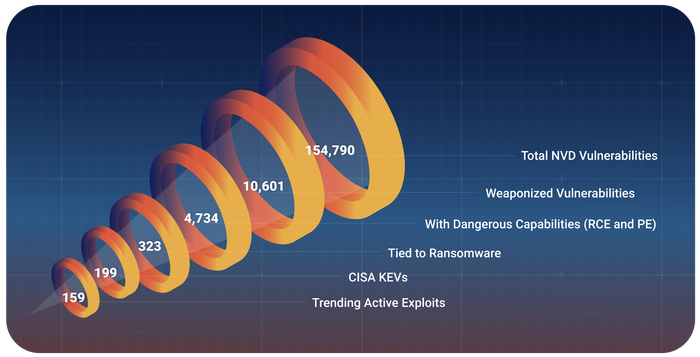
To date, there are 323 vulnerabilities tied to ransomware. However, CISA's KEV catalog is missing 124 of those. Organizations that continue to rely on traditional vulnerability management practices, such as solely leveraging public databases to prioritize and patch vulnerabilities, will remain at high risk of cyberattack. Source: Ivanti
You'd be forgiven if your eyes glazed over reading that list or looking at the graphic. It's a lot to take in. And it's even more to combat.
How to Combat Ransomware Right Now
I promised three things to consider right now when it comes to combatting this overwhelming threat. To make them easier to remember, I call this list "The Three Ds."
#1: Data
#2: Domain expertise
#3: Data modeling
You can't patch everything. And you also can't patch what you don't know about. That's why everything starts with data.
Right now, defense tends to be static. Too often, it's a "set it and forget it" approach that is completely antithetical to the way threat actors operate. Threat actors are not static, and neither should your defense be.
A clean and comprehensive data set, used the right way, lets you establish risk and security context.
How to do it? Don't wait for a vulnerability to be exploited. Every morning, look at your key risk indicators (KRIs) to get a sense of known vulnerabilities and known exploits (known/known). These are vulnerabilities that we can confirm are being used by threat actors. These early indicators are essential to get ahead of the game.
Fix known/knowns first. Once you've done that, then you can look for vulnerabilities that have the potential and likelihood to be weaponized. How likely are they?
This timely information is critical. Risk context and security information make patch data sets (that often feel overwhelming) more approachable. Instead of scrambling to produce as many patches as possible, you can fix what matters.
Domain expertise turns raw data into something actionable. Anyone can look at a data set, and no matter how clean and comprehensive it is, if you don't have domain expertise, you'll still be making wild guesses. Domain expertise lets you be smart about risks and prioritization. Without understanding a threat actor's intent — an understanding that can only come with domain expertise — you're wasting your time.
Finally, while domain expertise is fundamental to putting effort in the right place, truly effective risk-based patch management is impossible without automation. No one, no matter how much expertise and data they have, can effectively manage all this manually.
Data modeling is the final key. It can dissect the data based on any number of factors, such as sector, geography, threat profile, etc. Instead of looking at the data one way, you can look at it 10 different ways without expending additional human cycles.
Interdependent Protection Levels
Here's the tricky part: each of these factors (data, domain expertise, data modeling) flow into each other. You can't pick and choose. They're interdependent. Effective data modeling and automation are not a replacement for domain expertise; they're enabled by domain expertise. Lack of domain expertise means faulty models and faulty outputs. And again, without a clean and comprehensive data set, no amount of domain expertise will produce the right outcomes.
Start with the right data. Leverage domain expertise. And create models that help you target the most critical vulnerabilities.
Done well, this is a proactive and pain-free way to stay ahead of threat actors. Patch management and cybersecurity is too often reactive, but playing from behind is the biggest risk of all.
Threat actors are looking at their problem statement in a dynamic way, and they're reassessing constantly. Shouldn't you?
About the Author
You May Also Like
Catch the Threat Before it Catches you: Proactive Ransomware Defense
September 5, 2024How to Evaluate Hybrid-Cloud Network Policies and Enhance Security
September 18, 2024DORA and PCI DSS 4.0: Scale Your Mainframe Security Strategy Among Evolving Regulations
September 26, 2024Harnessing the Power of Automation to Boost Enterprise Cybersecurity
October 3, 2024
[Virtual Event] The Essential Guide to Cloud Management
October 17, 2024Black Hat Europe - December 9-12 - Learn More
December 10, 2024SecTor - Canada's IT Security Conference Oct 22-24 - Learn More
October 22, 2024



_Tero_Vesalainen_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
