15M+ Services & Apps Remain Sitting Ducks for Known Exploits
Scans of the Internet find that millions of computers, virtual machines, and containers are vulnerable to one or more of the hundreds of cyberattacks currently used in the wild, despite being patchable.
April 4, 2023

More than 15 million instances of Internet-connected applications, services, and devices are vulnerable to software flaws that the US government has confirmed are being exploited by attackers in the wild.
More than 190,000 systems, for example, appear to still be vulnerable to the 8-year-old Heartbleed vulnerability (CVE-2014-0160), while nearly 6.5 million devices are vulnerable to a medium-severity flaw (CVE-2021-40438) that could be used to redirect traffic to another server. In all, millions of applications, services, and operating systems are exposed to more than 200 remotely detectable vulnerabilities from the Known Exploitable Vulnerabilities (KEV) Catalog, researchers from cybersecurity firm Rezilion stated in a report published on March 30.
The takeaway? There is a concerning lack of patching of systems known to be vulnerable to in-the-wild attacks, says Yotam Perkal, director of vulnerability research at Rezilion.
"While only a fraction of the vulnerabilities discovered end up being exploited, the vulnerabilities on the KEV Catalog are being exploited, continuously, by sophisticated threat actors as well as advanced persistent threat (APT) groups," he says. "Not taking action is an invitation to get hit."
He adds, "Companies should do whatever they can to prioritize patching these vulnerabilities."
To boot, those estimates of just how many things are vulnerable out there are conservative, Perkal says, as the services affected by more than one vulnerability were counted only once.
"Given this conservative calculation approach, added to the fact that there are many CISA KEV vulnerabilities that can’t be identified with a high level of certainty (if at all) using Shodan, it is safe to assume that the actual number of vulnerable instances is much higher," he says.
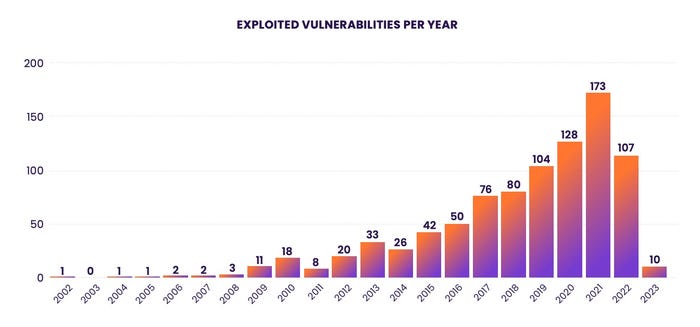
Vulnerabilities exploited by year of disclosure. Source: Rezilion
Typically, only a small fraction of vulnerabilities are exploited every year. In 2022, for example, more than 25,100 vulnerabilities were disclosed and assigned a Common Vulnerabilities and Exposures (CVE) identifier, according to the National Vulnerability Database. Yet only 107 of those issues are known to have been exploited, according to the Known Exploited Vulnerabilities Catalog, a list of more than 900 vulnerabilities maintained by the US Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA).
However, many of the KEV bugs are highly dangerous, such as the recently added vulnerability in IBM's popular Aspera Faspex file transfer stack and a bug in the ZK Java Web Framework.
The Long Tail of Exploitation
Using data gleaned from the KEV and information about the vulnerabilities contained in entries in the CVE databases, Rezilion researchers scanned the Internet using Shodan. They found 15 million services vulnerable to at least one exploit on the list.
Nearly 6.5 million instances of Apache HTTP Server were running a version still vulnerable to a critical sever-side request forgery (CVE-2021-40438) flaw. Another 2.1 million versions of the server were vulnerable to a separate flaw (CVE-2019-0211) that allows an attacker to escalate their privileges on the system. Despite its age, the Heartbleed flaw (CVE-2014-0160) ranked fifth on the list of most common vulnerabilities from the KEV Catalog, and the BlueKeep vulnerability from 2019 ranked ninth, with almost 52,000 instances discovered through the researchers' scans of the Internet. BlueKeep (CVE-2019-0708) is a critical remote code execution bug in the Remote Desktop Services Protocol in older and legacy versions of Windows.
Using data from threat intelligence service GreyNoise, the researchers discovered hundreds of scans on the part of threat actors searching for KEV vulnerabilities every day, making the threat very real, the company stated in its advisory.
"Failing to address these actively exploitable vulnerabilities poses a significant risk," the advisory stated. "While patching a vulnerability you know about, which is actively exploited in the wild and has a publicly available patch should be the easy part, the reality is that millions of systems remain exposed to these vulnerabilities — some even years after the vulnerability was discovered and a patch was made available."
More Vulnerable Under the Surface
In addition, companies are more vulnerable once an attacker gets past the perimeter. Shodan scans are limited to Internet-facing systems. Many of the flaws on the KEV list are generally only exploitable from inside a network, Perkal says.
"Some of the vulnerabilities on the CISA KEV Catalog are not vulnerabilities that exist in internet-facing applications," he says. "For example, local privilege escalation vulnerabilities are not vulnerabilities that Shodan will be able to identify."
Companies should first find which software components are affected entries on the KEV list and validate that the actual vulnerable code is part of running software. Since applications often do not use every function in an imported software library, the vulnerable code may never run. Rezilion security researcher Ofri Ouzan estimates that 85% of code with vulnerabilities is never actually run.
After that, companies can use the CISA KEV list to prioritize patching of issues. Beyond using the KEV list, other efforts are aiming to predict the likelihood of exploitation, which could help companies prioritize their effort.
About the Author
You May Also Like




