10 Web Threats That Could Harm Your Business
Easily overlooked vulnerabilities can put your data and business at risk
March 7, 2013

Download Dark Reading's March special issue on Web threats
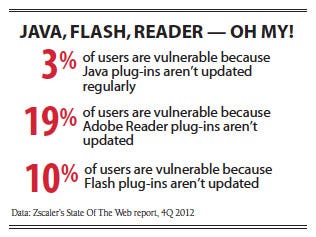
SQL injections accounted for about 7% of Web attacks in 2011 and looked to be petering out, according to security services vendor Trustwave. Then last year those exploits jumped to 26% of Web attacks, hitting companies that could have easily protected themselves.
The Trustwave data proves what hackers have known for years: Even though application vulnerabilities are well known and can be fixed or blocked, many companies don't implement secure coding practices and regularly test their applications to find them. Companies that overlook such basic Web security practices have no chance against more advanced attacks, says Chris Pogue, Trustwave's director of incident response and forensics.
Input validation, where user input -- such as a search query -- is limited to simple strings, is an easy way to protect against SQL injection, but developers frequently fail to do that, Pogue says. "It's one of the things that's taught in college, and if it has made it into the university system, then it's not bleeding-edge technology," he says.
The Web presents a variety of security threats for unwary businesses, from well-known SQL injection and cross-site scripting attacks to more esoteric threats posed by Web scraping and HTML5's many features. What follows are 10 Web threats we think are particularly worrisome, either because they're becoming more popular with attackers or because security pros and developers tend to overlook them.
1. Bigger, Subtler DDoS Attacks
When IT specialists think about distributed denial-of-service attacks, they envision the most basic kind: floods of packets overwhelming a victim's network so that valid requests can't get through. But improvements in defenses have forced attackers to change the way they attack.
Packet floods have become larger, maxing out at 100 Gbps. In a six-month campaign against U.S. banks, for which a group of alleged Muslim hacktivists claimed credit, the volume of attack traffic has regularly surpassed 30 Gbps -- throughput rarely seen five years ago.
Attackers also have targeted other parts of the infrastructure. Corporate domain name service servers are a favorite target, according to domain registrar VeriSign. When attackers take DNS servers down, customers can no longer access a company's service. "It doesn't matter how much data center capacity a company has, the requests will never reach their data centers," says Sean Leach, VP of technology for VeriSign's network intelligence and availability group.
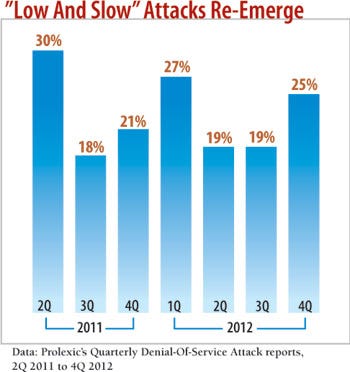
Massive DDoS attacks often mask "low-and-slow" attacks, which use specially crafted requests to cause Web applications or appliances handling specific services, such as Secure Sockets Layer communications, to quickly consume processing and memory resources. These application-layer attacks now account for about a quarter of all attacks.
"If the mega-DDoS attacks are the cavemen getting bigger clubs, [low-and-slow] attacks are like the caveman evolving, getting smarter," says Matthew Prince, CEO of Internet security company CloudFlare.
Attackers look for URLs on a target site and then make calls to the back-end database that powers the site. Frequent calls to those Web pages quickly consume a modest site's resources, says John Summers, VP of security products at Akamai Technologies. "The targeting is much better this year than in 2011," Summers says. Attackers "are doing their homework, doing reconnaissance."
It's no longer enough for companies to use an appliance to block bad traffic as it enters their networks because the router will still be overwhelmed in a low-and-slow attack. These attacks can also get through a cloud DDoS mitigation service. Instead, companies should go with a hybrid approach, using Web application firewalls, network security appliances and content distribution networks to create a layered defense that screens out unwanted traffic at the earliest possible point.
2. Old Browsers, Vulnerable Plug-Ins
Cyber attacks that account for millions of dollars a year in bank account fraud are fueled by browser vulnerabilities and, more frequently, the browser plug-ins that handle Oracle's Java and Adobe's Flash and Reader. Exploit kits bring together a dozen or so attacks on various vulnerable components and can quickly compromise a company's systems if the patches aren't up to date.
A recent version of the popular Blackhole exploit kit, for example, contained attacks for 16 vulnerabilities, including seven targeting the Java browser plug-in, five targeting the Adobe PDF Reader plug-in and two targeting Flash, according to anti-malware firm Sophos. The Sweet Orange exploit kit contains Java, PDF, Internet Explorer and Firefox exploits, according to the creator's statements that security firm Webroot discovered. "These exploit kits are really good at identifying which vulnerabilities are unpatched in the browsers that people are running," says Grayson Milbourne, Webroot's senior threat researcher.
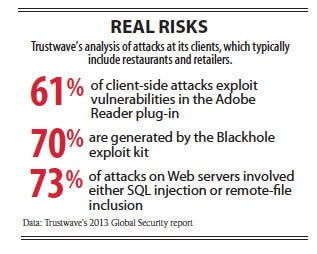
Companies should pay attention to Oracle's Java plug-in in particular. Cybercriminals are focusing on Java because it's widely deployed but poorly patched, says Michael Sutton, VP of research at Zscaler, a security-as-a-service provider.
Only 4% of systems at companies using Zscaler's security service have the Java plug-in installed, but almost 80% of those Java plug-ins are out of date, according to the provider's data for the last quarter of 2012. Adobe's Flash and Reader plug-ins are more ubiquitous but better patched, Sutton says. "Companies haven't grasped the problem of how Java plug-ins have been abused," he says.
Patching is the most obvious way to protect against this vulnerability. A number of patch management products, such as Qualys for large companies and Secunia for small and midsize businesses, are available. Companies that want to protect against zero-day attacks (for which a patch hasn't been released) should use anti-malware software such as ValidEdge (recently acquired by McAfee) and Invincea, which runs downloaded files in a sandbox.
Trustwave Global Security report - Real Risk
3. Good Sites Hosting Bad Content
Attackers are targeting well-known, legitimate websites to take advantage of users' trust in those sites. For example, in the VOHO watering hole attack last year, attackers infected legitimate financial and tech industry websites in Massachusetts and Washington, D.C., commonly accessed by their intended victims, says security vendor RSA.
Such tactics are difficult to explain to employees, and technical defenses aren't always enough, says Dan Ingevaldson, CTO at Easy Solutions, a fraud protection company. "You can't stop it by asking users to browse well-known websites, because the fact that the site is legitimate doesn't matter," he says.
A more insidious attack, malvertising, is the insertion of malicious content into an ad network. The malicious ad may crop up only occasionally in the network's rotation, making the attack difficult to detect.
It's a serious issue, says Robert Hoblit, senior director of product management for Symantec. "When you're serving malvertising to your end users, you're going to get blacklisted and you'll lose revenue," he says.
Again, a layered defense will help stop both watering hole and malvertising attacks. Security proxies that clean Web traffic and attempt to catch malicious executables work well, but they should be paired with anti-malware protection on employees' computers to catch the execution of known threats.
4. Mobile Apps And The Unsecured Web
The bring-your-own-device movement has led to a surge in consumer-owned devices inside corporate firewalls. But mobile apps are notoriously poorly programmed, putting business data at risk, says Zscaler's Sutton. There's been a lot of talk about the increasing amount of mobile malware published online, but few security experts are issuing warnings about how programming mistakes turn legitimate mobile apps into dangerous threats.
Nearly 60% of mobile apps Zscaler has studied are grabbing unique hardware information from devices and passing it over Web interfaces, Sutton says. Worse, about 10% of the applications aren't transmitting users' credentials securely, he says.
Part of the problem is that Google's and Apple's app stores aren't as secure as they should be. Mobile app security should be better than in the PC world because these app stores act as gatekeepers, "but they're clearly not catching these issues," Sutton says.
Furthermore, the Web services that power many mobile apps are poorly programmed. Because users don't like to type passwords to use services from their mobile devices, mobile apps often use session tokens that don't expire. Attackers can sniff traffic at Wi-Fi hotspots and pick out these tokens, letting them access their victims' accounts.
"The guy who sniffed that traffic … can be you for a year," says Dan Kuykendall, CTO at NT Objectives, a Web application security provider. Sound security programming is the best way to defeat these sorts of man-in-the-middle attacks, but it's not being applied to mobile apps, Kuykendall says. "We're seeing a lot of Web security 1999 problems -- wide open stuff," he says. A new generation of developers isn't putting the necessary defenses in place to stop malicious hacking, and "we know that's a very bad assumption to make," he says.
Companies do find it difficult to limit the applications loaded onto an employee-owned phone. But they can limit the data that workers put on their devices or in the cloud and limit the devices to a corporate DMZ.
5. Failing To Clean Up Bad Input
Since 2010, SQL injection has held the top spot on the Open Web Application Security Project's list of top 10 security vulnerabilities. Dynamic websites that pass search queries or other application inputs to a back-end database server are vulnerable to SQL injection. But the simple fix, as mentioned earlier, is to check all user-provided input to make sure it's valid.
Companies often focus on their main website when fixing SQL flaws and forget to lock down other connected sites, such as remote collaboration systems and contractor time-tracking systems. Attackers can use those other sites to infect employees' systems and gain access to the internal network without the need to circumvent security measures on the victim company's main site, says Jeremiah Grossman, CTO at Web application security firm WhiteHat.
To minimize SQL injection flaws, pick a software development framework and commit to it, Grossman says. As long as the developers stick to programming in that framework and keep its patches up to date, they'll create secure code, Grossman says.
Zscaler State of the Web: Java Flash Reader
6. The Hazards Of Certificates
Two years ago, a series of hacks against certificate authorities -- the companies that determine who's trusted online -- gave attackers the tools they needed to issue fraudulent SSL certificates that could disguise a malicious website as a legitimate, well-known company's site. The attacks, against Comodo, DigiNotar and other certificate authorities, underscored the danger of relying too much on a single security technology.
These attacks also highlighted the blind trust that companies were putting in certificates. In addition to letting attackers create authentic-looking malicious sites and services, fraudulent and stolen certificates also let them sign malicious code to make that code appear legitimate. Browser makers generally decide which certificates to trust, but businesses do have control over their own encryption keys and certificates.
Poor certificate management can lead to expensive incidents. The average large company is expected to lose $35 million in the next two years from certificate-related incidents, according to a Ponemon Institute study funded by Venafi, a certificate management provider. Venafi often finds companies storing certificates in the open on developer systems. Instead, they should create a centralized and well-secured repository where they can track certificate use and revoke certs when they're found to be compromised.
7. The Cross-Site Scripting Problem
Attacks exploiting cross-site scripting flaws let the attacker run scripts as if they came from a vulnerable website. They don't give the attacker access to the vulnerable website but instead target the users that go to that site. An attacker going after a banking site with a cross-site scripting vulnerability could run a script for a login box on the bank's page and steal users' credentials. "XSS exploits the trust that a browser has for a website," WhiteHat's Grossman says.
More than 70% of the applications checked by code-security firm Veracode contain cross-site scripting flaws. The vulnerability is the top issue affecting commercial open source and internally developed software, Veracode says.
Automated code-checking tools, such as those from Hewlett-Packard's Fortify, Veracode and WhiteHat, can detect cross-site scripting issues. Companies should modify their development processes to check code for defects before it's put into production. This approach will catch common coding mistakes and trains developers to avoid them in the future.
8. The Insecure 'Internet Of Things'
Routers and printers, videoconferencing systems, door locks and other devices are now networked via Internet protocols and even have embedded Web servers. In many cases, the software on these devices is an older version of an open source library that's difficult, if not impossible, to update. Welcome to the Internet of things.
An Internet-enabled device is "a great stealth back door into an enterprise for an attacker," says Zscaler's Sutton. "It has everything you need to get in."
Most companies don't bother securing their Internet-accessible printers and videoconferencing systems, for instance, so attackers find those vulnerable systems and take them over. Once a device is owned by the attacker, it serves as a bridge into the company's network.
A recent Internet scan by vulnerability management firm Rapid7 found 40 million to 50 million accessible devices using one of three libraries for the Universal Plug and Play protocol, which are known to contain vulnerabilities.
End users, businesses and ISPs should identify and disable any Internet-exposed UPnP endpoints in their environments, says HD Moore, Rapid7's chief security officer. "UPnP is pervasive. It's enabled by default on many home gateways, nearly all network printers and devices ranging from IP cameras to network storage servers," he says.
Hunting down vulnerable network devices needs to be easier, Zscaler's Sutton says. General-purpose tools designed to scan PCs and servers usually don't give reliable information about embedded devices, but there are tools that will identify vulnerable devices, such as Rapid7's ScanNow and open source tools such as Nmap.
Low and Slow attacks emerge
9. Getting In The Front Door
Not all attacks are aimed at breaching a company's defenses. Automated Web bots scrape from Web pages information that can give a competitor better intelligence on your business. For example, if you have an online store, a competitor could collect data on your pricing from publicly available information on your site, says Marc Gaffan, co-founder of Web security firm Incapsula. "Are they breaching your site? No, but they are harming your business," he says. More than 30% of Web traffic to the average site is this sort of unwanted, potentially business-sapping traffic, Gaffan says.
Web application firewall services such as Incapsula and CloudFlare let businesses identify which traffic is connected to good search-indexing bots and which are bad market intelligence services or even fake Google bots. Such services block the requests, preventing information from going to competitors.
10. New Technology, Same Problems
Stanford graduate student and computer security researcher Feross Aboukhadijeh recently showed how an HTML5 feature could let an attacker pull off a convincing phishing attack. Using HTML5's ability to trigger full-screen mode, Aboukhadijeh created a large database of simulated pages that could fool users into thinking they had gone to a bank's website when, in fact, they were on an attacker's site.
Using Firefox on Mac OS X to click on a link that appears to go to Bank of America's consumer banking site? No problem. With Aboukhadijeh's attack that link is on an attacker-controlled page, and your click is intercepted. Since some browsers don't notify users that they're entering full-screen mode, attackers can throw up a full-screen disguise for any site and then use the fake site to obtain victims' login credentials.
In this case, rather than sending you to bankofamerica.com, the attacker throws up a full-screen page that makes it appear you're on the real Bank of America site. A careful inspection could tip off users to the fact that parts of the screen, such as the menu bar, don't match their normal desktop, but most people won't look that closely.
"Links are the bread and butter of the Web," Aboukhadijeh wrote on his site. "People click links all day long -- people are pretty trained to think that clicking a link on the Web is safe. Savvy users may check the link's destination in the status bar before clicking. However, in this case, it won't do them any good." That's because the attacker can make the fake site appear to go to the real site, say, bofa.com.
The automated security tools that could eliminate HTML5 security issues aren't available yet, says NT Objectives' Kuykendall. "People are outpacing their security tools, which is going to leave them exposed," he says.
Training developers in secure practices, especially with new platforms such as HTML5, is a critical first step to preventing security problems. In addition, having developers check one another's code can cut down on vulnerabilities.
As with any collection of threats, businesses will find themselves with different exposures. An online business may have SQL injection and HTML5 issues, while a firm with a lot of telecommuters may have mobile issues, including exposed devices with embedded vulnerabilities. Rather than attempt to minimize the dangers from every threat, companies should focus on the subset of vulnerabilities where they're most exposed.
About the Author
You May Also Like




