Lone Android vulnerability among the top 10 software flaws most abused by cybercriminals.
March 19, 2019
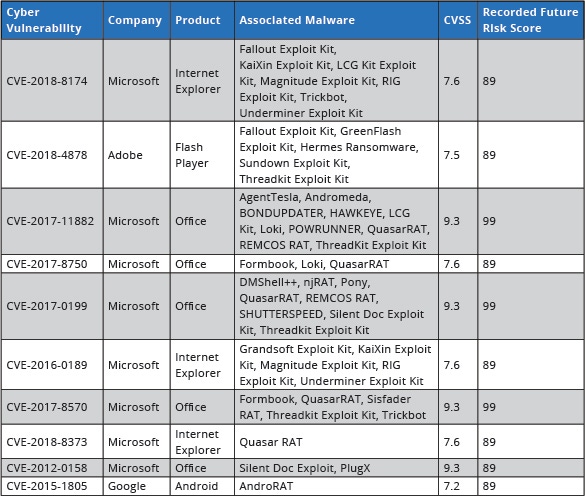
It should come as no surprise that cybercriminals favored Microsoft Office vulnerabilities in their cyberattacks last year, given the rise in phishing attacks that included rigged Word and Excel Office file attachments.
Eight of the top 10 most exploited vulnerabilities in 2018 were Office bugs, according to a new study by Recorded Future. An Adobe Flash bug (No. 2) and an Android flaw (No. 10) also made the list, which led with a Windows remote code execution exploit that was found in several exploit kits, including Fallout, KaiXin, LCG Kit, Magnitude, RIG, Trickbot, and Underminer.
It's a natural progression given the shift from cybercriminals employing Web exploit kits to waging more phishing campaigns in 2018, notes Alan Liska, threat intelligence analyst at Recorded Future.
The shift away from browser exploits is due to developers better securing and enforcing updates to their browser software, he says. Just three of the top 10 vulns on the list were browser-related, involving older versions of Internet Explorer. "That means there are a whole lot of older systems still running unpatched [browsers]," he says.
Meanwhile, just five new exploit kits arrived in 2018, down from 10 new ones in 2017 and 62 in 2016, according to the study, which analyzed code repositories, Dark Web forum postings and sites, as well as other metadata. And just two new exploit kits - Fallout and LCG Kit - made the Top 10 most exploited vulns list for 2018.
While Recorded Future excluded nation-state groups from the list, the study also comes amid a throwback to old-school hacking by both cybercriminals and nation-states: using stolen user credentials, including Remote Desktop Protocol (RDP) and VPN logins or credential-stuffing attacks to hit a targeted organization, rather than throwing malware at the victim.
"I think the trend line of fewer exploit kits" supports this, Liska says. "There are other points of entry taking away from where we see vulns being deployed. If you focus on brute-force attacks and using tools to enable that, you're not necessarily going to need to use an exploit kit or these vulns if you can walk in with credentials."
"We spend a lot on threat-sharing," notes John Bambenek, director of cybersecurity research at ThreatStop. "But if there are no indicators to share except people sharing credentials, there's no real defense except not to have [weak] passwords."
And exploit tools, including zero-day vulnerabilities, increasingly are only being used by nation-states, not cybercriminals. "Zero-days are immensely valuable resources. Why throw them into an exploit kit when you can sell them to an intel agency for seven figures?" he explains. "Criminals are getting their payday, anyway ... just having email lists and mail servers," for example, he says.
Android Cracks the Top 10
The only mobile device flaw on the Recorded Future top 10 list was a critical 2015 local elevation of privilege vulnerability in the kernel of some Android devices. It made the list for the first time and for the same basic reason Microsoft Office did, according to Liska: It's a popular platform with a wide attack surface. And some Android devices are more secure than others, he notes of the open-source mobile platform.
"The most exploitation we saw with the Android vuln occurs in various Android stories - through bad apps or rigged apps," Liska says.
Mobile remains a small portion of the attack surface to date, though. A recent study by Sophos found that 10% of cybercriminal attacks are discovered on mobile devices, while 37% are detected at the server and 37% at the network. "We don't see a lot of compromises [via] mobile. We don't see a lot of big incidents starting with the phone," says Chester Wisniewski, principal research scientist for Sophos.
Meanwhile, "Double Kill," the Microsoft IE flaw that holds the No. 1 slot for the most exploited, operates over multiple versions of IE and Windows, which made it especially popular, according to Liska. "The way its kit works is that it sends a probe - usually a JavaScript [one] - and queries information on the browser to find out as much as it can about the operating system, browser version, and patches installed" on the victim's machine, he says. "Then it chooses the exploit to throw at it. It's so easy to use."
The No. 2 vuln exploited last year was CVE-2018-4878, an Adobe Flash Player use-after-free flaw that was packaged in several exploit kits, including Fallout and the former Nuclear kit. Fallout spreads the prolific GandCrab ransomware, which increasingly is being deployed in targeted attacks against large organizations to get a better bang for the buck for the attackers.
Adobe plans to kill off the historically flawed and targeted Flash Player in 2020. Meanwhile, though, Flash holds the dubious record for the fastest exploitation of flaws: Once Adobe reveals and issues a patch for one of Flash's bugs, on average it gets exploited within two days, according to Liska.
A remote-access Trojan also made Recorded Future's most exploited list: CVE-2017-8570, an Office remote execution flaw, comes with the Sisfader RAT.
Same Old, Same Old
While the top 10 most exploited vulnerabilities list is intended to help organizations prioritize their patching rollouts, Recorded Future's recommendations for preventing attacks from these exploits are the usual security hygiene checklist: Steer clear of Flash on websites, use browser ad blockers to protect from malvertising, execute frequent backups, and train users on phishing awareness and other scams via email. The company also advises running Google Chrome browser, which is considered one of the most secure.
Related Content:

Join Dark Reading LIVE for two cybersecurity summits at Interop 2019. Learn from the industry's most knowledgeable IT security experts. Check out the Interop agenda here.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


