Dissecting Dendroid: An In-Depth Look Inside An Android RAT Kit
Dendroid is full of surprises to assist it in subverting traditional security tactics through company-issued Android phones or BYOD.

In March, alarms went off when security researchers discovered the Android malware creation kit Dendroid was being advertised in malware forums for sale to anyone who wanted to automate the distribution process for a mere $300.
Dendroid consists of a web-based administration panel and a builder that can add “Remote Administration Toolkit” (RAT) functionality by repackaging it with existing applications. Researchers disclosed how easy it is to patch Dendroid into existing apps (which is scary enough, given how quick users are to download new apps) but what sets Dendroid apart is the myriad of malicious functionality it possesses to exploit an Android device.
One of the most frightening examples of Dendroid capabilities is that it can secretly record all of your phone calls or silently listen in on your phone’s microphone whenever it wants. The malware can also upload all of your phone’s pictures. Imagine walking into the office, going on an interview, or applying for a bank loan one day and have to face your entire digital personal history on display. Even costlier than personal embarrassment, though, is the potential risk Dendroid poses for businesses using company-issued Android devices or supporting a BYOD policy. Pictures of notes from brainstorming sessions or intellectual property are temptingly at risk of exploitation.
Diverging from the data-loss theme for a moment, Dendroid can also perform “classic” Android malware functions, such as sending SMS messages to premium-rate numbers without making its owner aware until the huge bill arrives.
Even worse is the fact that Dendroid is clever enough that it can hide in plain sight, packaging itself inside an application that appears to be a parental control tool. One area where this can really wreak havoc is with parental control apps that require several of the same privileges as the RAT, such as accessing GPS coordinates or checking installed apps. This allows Dendroid to sneak by defenses, even with manual inspection, while secretly requesting permissions to access a long list of questionable applications and actions including:
INTERNET
CAMERA
READ_SMS
WRITE_SMS
READ_CONTACTS
WAKE_LOCK
CALL_PHONE
RECORD_AUDIO
Dendroid is full of surprises to assist it in subverting traditional security tactics. In this screenshot, you can see how Dendroid authors use configurations and commands to further their efforts:
Notice the flag called “GPlayBypass,” which stands for “Google Play Bypass.” This functionality is designed to help the malware evade detection by Google Bouncer, a sandboxing tool through which almost every app has to run before it is allowed into the Google Play store. It’s just one of the many tools Dendroid wields in its quest to cause the greatest amount of harm to your Android device.
In the end, of course, it’s all about money for Dendroid. In this malware forum post from October 2013, the author advertises the sale of Dendroid source code for both the panel and the builder (including three months of support). He or she fondly notes in another section of the post that the project took “1.3 years to fully develop”:
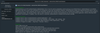
Dendroid’s large variety of available commands shows the full threat potential that an infected phone can have. The emulator detection is simple, but it is likely to work in various analysis environments. Since the kit includes components to repackage existing apps, we can expect to see more of Dendroid in the future.
All in all, this is a very interesting piece of malware, and a difficult one to detect. Users of network forensics appliances should look for indications of the traffic patterns, which you can read about in greater detail in my full blog post, Dendroid under the hood.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




