Korean-Speaking Cyberspies Targeting Corporate Execs Via Hotel Networks
Researchers unmask the inner workings of "Darkhotel," a unique seven-year-old cyber espionage campaign against C-level executives from various nations as they travel in the Asia-Pacific region.
November 10, 2014
Corporate executives from around the world are being individually tracked and targeted on the road in an intriguing cyber espionage attack campaign where the attackers know the hotels their targets are staying and stage attacks from the establishments' networks.
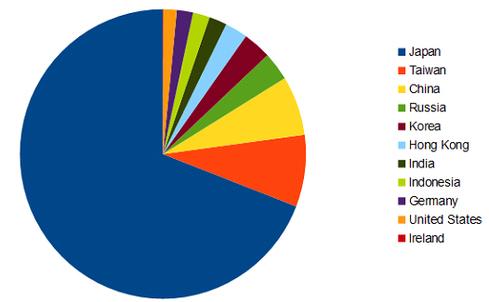
More than a couple of dozen hotels' physical and WiFi networks in the Asia-Pacific region have been infiltrated by the so-called Darkhotel or Tapaoux hacker group, which appears to be Korean-speaking, according to findings shared today by Kaspersky Lab. More than 90% of the victim organizations have been from Japan, Taiwan, China, Russia, and Hong Kong, though the researchers also have found some German, American, Indonesian, Indian, and Irish execs who have been affected. Japan has the heaviest volume of victims, and just under two dozen executives so far have been confirmed as victims, according to Kaspersky researchers.
The attackers employ a mix of highly targeted and botnet-type techniques, infecting hotel networks and then waging their attacks from those locations when specific execs -- some CEOs, senior vice presidents, sales and marketing directors, and R&D execs from major companies -- check into their hotels. The botnets are for surveillance, DDoS, or downloading more sophisticated information-stealing malware on to their victims' machines. The attacks via hotel networks have been under way for at least four years and are still ongoing, according to Kaspersky, but the group has been waging other forms of attack for at least seven years.
"Multiple hotels in multiple countries in the APAC as of right now" are being hit by Darkhotel, says Kurt Baumgartner, principal security researcher at Kaspersky Lab, who would not name the victims or hotels involved. "But our investigation is ongoing, and we have a strong belief that it is [occurring] elsewhere" outside the Asia-Pacific region, as well.
Baumgartner says a keylogger used in the attacks appears to be written by a Korean-speaking developer, and the data discovered on the command and control servers used in the attacks have Korean language in the data strings. "You've got a number of individuals involved here who are Korean-speaking and the attacks are happening in the APAC region." He stopped short of confirming the attackers were a Korean nation-state.
And when they infect a Korean-speaking target, the attackers delete the malware -- an indication that they are avoiding friendly fire.
Hotel networks and WiFi -- like any public WiFi -- is notoriously risky. Tom Kellermann, chief cyber security officer at Trend Micro, says hotel wireless networks have been under siege by criminals and spies for a long time. "Travelers should be tremendously dubious of hotel, train, and airport WiFi. These locations have become the ideal hunting grounds for opportunists and nation-states alike. This campaign represents nothing new."
CrowdStrike issued a related warning today about hotel networks and other WiFi to participants in the upcoming G20 Global Leaders Summit, which will be held Nov. 15 and 16 in Brisbane, Australia. With hotels in Brisbane at capacity, many attendees will be lodging outside the city and be shuttled to and from the meetings, leaving them at risk during their travel back and forth, says CrowdStrike's Adam Meyers. In its advisory, CrowdStrike says that the likelihood of attacks via "social engineering, shoulder surfing, or certain Wi-Fi and mobile attacks (exploiting hotel networks, for example)" increases due to the travel.
The Darkhotel gang pushes infected Adobe Flash, Google Toolbar, or Windows Messenger updates to a targeted exec when he or she logs into the hotel's physical or WiFi network. If the exec downloads the update, a backdoor gets planted on the machine. The Adobe Flash update, for example, is actually digitally signed so that it will appear legitimate.
"They used some heavy math which was pretty impressive at the time to sign their malware with their weak [512-bit key] certificates. Now they are outright stealing legitimate 2,048-bit certificates from legitimate organizations... to sign their malware," Baumgartner says.
The attackers also download the Karba Trojan with an information-stealing module and other malware to conduct reconnaissance on the executive's machine, looking for AV software, cached browser and email passwords, and any other sensitive information. The attackers infect each victim only once, and they delete any trace of their activity after they've pilfered what they want from the victim. Kaspersky recently discovered attacks against US and Asian execs traveling on business in the APAC region for investment or other purposes. So far, Darkhotel appears to be targeting execs in government, defense, and non-governmental organizations.
"These guys are professional, well-organized, and methodical," Baumgartner says. "They know what they're after. They don't need to go after a victim again" once they've accessed what they need.
The cyber espionage gang also previously used spearphishing attacks and poisoning of peer-to-peer networks to hit their targets.
In another unusual strategy, one of the downloaders delays command and control communications by the infected machine for 180 days. "If a special file exists on the system, the module will not start calling back to the C&C server until the special file is 180 days old," Kaspersky says in its detailed report on Darkhotel.
"We've seen delays of five days, maybe a week. But we don't see 180 days," Baumgartner says. "That may be so that when an executive returns to his [office] and his laptop gets inspected, they don't want any outbound traffic. They've already gotten what they wanted and don't need to look for anything."
Kaspersky recommends using a VPN on WiFi or other networks on the road, and to be suspicious of any application updates that pop up.
But Ian Pratt, co-founder and executive vice president of products at Bromium, says a VPN can't necessarily prevent a WiFi-borne attack.
"Most WiFi networks require you to successfully sign in to a captive portal page before they will allow you external access. In many cases it is the sign-in page itself that is malicious, and by the time the user has entered their surname and room number they will have been delivered an exploit tailored to their machine and compromised," Pratt says. "Bringing a VPN up at this point plays directly into the attackers' hands, bringing the infection onto the enterprise network."
About the Author(s)
You May Also Like
Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024Finding Your Way on the Path to Zero Trust
May 22, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


