Zero-Day Exploit Use Exploded in 2021
Ransomware and other financially motivated threat actors joined nation-state-backed groups in leveraging unpatched flaws in attack campaigns, new data shows.
April 21, 2022

Threat actors exploited more zero-day vulnerabilities in 2021 than any prior year and mostly in software from Microsoft, Google, and Apple.
State-backed advanced persistent threat actors remained the most prolific users of these exploits as has always been the case to date. However, they were not the only ones: financially motivated groups — particularly ransomware operators — sharply ramped up their use of zero-days and accounted for one in three of attackers exploiting these vulnerabilities.
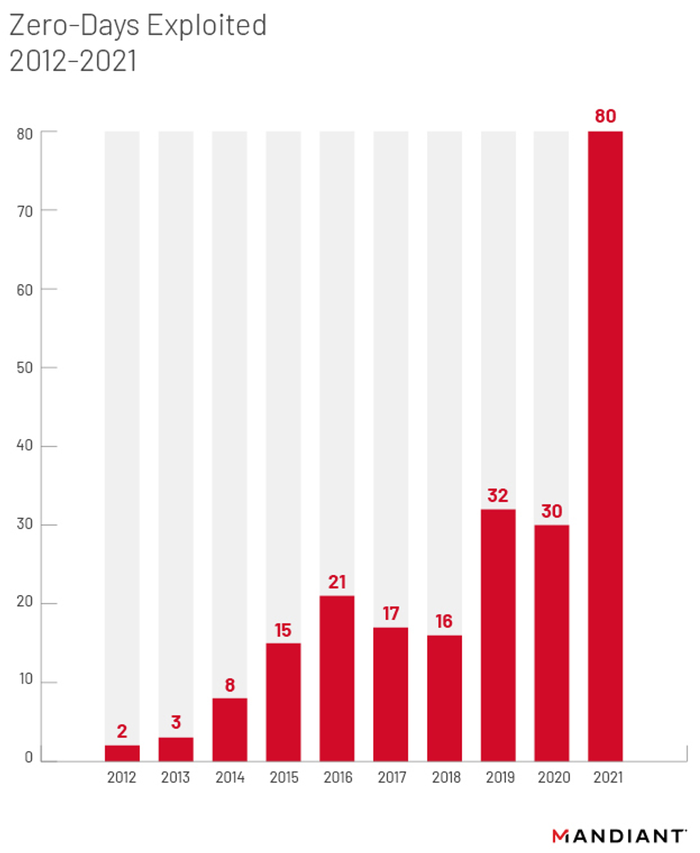
Two separate advisories this week — one from Mandiant and the other from Google's Project Zero security team — identified a big jump last year in software flaws that threat actors exploited before a patch became available. Mandiant counted a total of 80 such flaws in 2021, while Google identified 58 zero-days that were exploited in the wild before being patched.
By Mandiant's count, the 80 zero-day exploits in 2021 represented a 167% increase over the 30 it logged in 2020, and it more than doubled the previous highest number of 32 in 2019. The 58 zero-day exploits that Google counted represented more than double the 25 that company observed in 2020. It was also more than double Google's highest-ever total of 28 zero-days back in 2015.
Vulnerabilities in Microsoft, Google, and Apple accounted for 75% of the zero-days that threat actors exploited last year — a number likely tied to the broad use and popularity of technologies from these three vendors, Mandiant said. A spreadsheet of zero-day flaws that Google has maintained since 2014 shows that 16 of the 58 zero-day exploits the company observed last year were in its own technologies; 21 involved Microsoft products; and 13 were in Apple products. The remaining vulnerabilities involved products from a total of nine other vendors including Qualcomm, Trend Micro, Sonic Wall, Accellion (now Kiteworks), and Pulse Secure, Mandiant said.
Source: Mandiant
The data underscores how organizations cannot ignore the potential for threat actors to hunt for and exploit zero-days in less widely used technologies, says James Sadowski, principal analyst at Mandiant.
"While popular vendors remain popular targets for zero-day exploitation, we've gradually seen expansion of both technologies and vendors targeted by zero-day exploitation outside of main vendors," he says.
"Like we observed in the exploitation of Accellion FTA, threat actors can exploit vulnerabilities in these systems and cause significant damage," Sadowski says, referring to a zero-day flaw in a near obsolete Accellion product that led to breaches at multiple large companies.
Many Reasons Why
Mandiant identified multiple potential reasons for the explosion in threat actor use of zero-day exploits last year. The company perceived the increased enterprise adoption of cloud, mobile, and IoT technologies as increasing the volume of software that organizations are using and therefore resulting in the discovery of more bugs. The increase in the number of so-called exploit brokers trading in zero-day vulnerabilities has also been a factor, as have increased investments in research and development by zero-day exploits threat groups. Google, meanwhile, attributed the surge to improved detection and disclosure of zero-day bugs — a factor that Mandiant too said was likely at play.
The security vendor's analysis showed that state-sponsored groups — especially those from China — continue to dominate zero-day exploit use. But there was a noticeable increase in the number of ransomware and other financially motivated threat groups leveraging zero-days in their attacks.
Sadowski says these threat actors are likely acquiring zero-day exploits via underground exploit brokers and criminal service providers. Or they could be recruiting the requisite talent in-house to research vulnerabilities and develop zero-day exploits, as appeared to be the case with the Conti ransomware group — leaked Conti chat files showed the threat actors discussing recently disclosed vulnerabilities and assigning members to build a scanner to identify potentially vulnerable systems.
"As ransomware groups collect increasingly large sums from their operations, we have observed them more frequently employ zero-day exploits in their operations," Sadowski says. Generally, though, it is extremely difficult to identify where a threat actor might have acquired a zero-day exploit, he says.
Bud Broomhead, CEO at Viakoo, says the increased use of zero-day exploits shows that threat actors are shifting their attack vectors away from vulnerabilities that traditional threat assessment and detection solutions would uncover. "That's why not just zero-day threats, but also exploiting IoT vulnerabilities and leveraging open source software, are rapidly growing enterprise threats," he says. The challenge for organizations is figuring out how to limit damage from a successful zero-day breach and figuring out how to protect against exploits targeting new attack vectors.
The growing use of zero-days highlights the need for organizations to have rapid, out-of-band patching capabilities, says John Bambenek, principal threat hunter at Netenrich.
"Organizations need to remain flexible and agile getting these into production," he says. "Remove as many barriers as possible to patching, including streamlining testing and change management."
About the Author
You May Also Like




