3 Common Initial Attack Vectors Account for Most Ransomware Campaigns
The data shows how most cyberattacks start, so basic steps can help organizations avoid becoming the latest statistic.
May 19, 2023

Most ransomware attackers use one of three main vectors to compromise networks and gain access to organizations' critical systems and data.
The most significant vector in successful ransomware attacks in 2022, for example, involved the exploitation of public-facing applications, which accounted for 43% of all breaches, followed by the use of compromised accounts (24%) and malicious email (12%), according to Kaspersky's recently released report, "The Nature of Cyber Incidents."
Both exploitation of applications and malicious emails declined as a share of all attacks compared with the previous year, while the use of compromised accounts increased from 18% in 2021.
Bottom line: Doubling down on the most common attack vectors can go a long way to preventing a ransomware attack. "A lot of companies are not the initial targets for attackers but have weak IT security and [allowing them to] be hacked easily, so cybercriminals take the opportunity," says Konstantin Sapronov, head of the global emergency response team at Kaspersky. "If we look at top three initial vectors, which together account for almost 80% of all cases, we can implement some defensive measures to mitigate them, and go a very long way to decreasing the likelihood of becoming a victim."
The top initial vectors cited by Kaspersky match an earlier report by incident-response firm Google Mandiant, which found that the same common vectors made up the top three techniques — exploitation of vulnerabilities (32%), phishing (22%), and stolen credentials (14%) — but that ransomware actors tended to focus on exploitation and stolen credentials, which together accounted for nearly half (48%) of all ransomware cases.
Ransomware took off in 2020 and 2021, but leveled off last year — even dropping slightly. But this year, ransomware and a related attack — data leaks with a goal of collecting a ransom — appear to be increasing, with the number of organizations posted to data leak sites increasing in the first part of 2023, says Jeremy Kennelly, lead analyst for financial crime analysis at Mandiant.
"This may be an early warning that the respite we saw in 2022 will be short-lived," he says, adding that the ability to continue to use the same initial access vectors has helped attacks.
"Actors engaging in ransomware operations haven’t needed to evolve their tactics, techniques, and procedures (TTPs) significantly in recent years, as well understood strategies have continued to prove effective," Kennelly says.
Unsurprising Trio: Exploits, Credentials, Phishing
In December 2022, the Cybersecurity and Infrastructure Security Agency (CISA) warned that attackers were commonly using five initial access vectors, including the three identified by both Kaspersky and Mandiant, as well as external remote services — such as VPNs and remote administration software — and third-party supply chain attacks, also known as trusted relationships.
Most compromises are either quick or slow: Quick attacks compromise systems and encrypt data in days, while slow ones are where threat actors typically infiltrate deeper into the network over months, possibly conducting cyber espionage and then deploying ransomware or sending a ransom note, according to Kaspersky's report.
Exploitation of public-facing applications and the use of legitimate credentials also tend to be harder to detect without some sort of application or behavioral monitoring, leading to longer dwell times for attackers, says Kaspersky's Sapronov.
"[N]ot enough attention is paid to application monitoring," he says. "Also, when attackers use [exploitation], they need to take more steps to reach their goals."
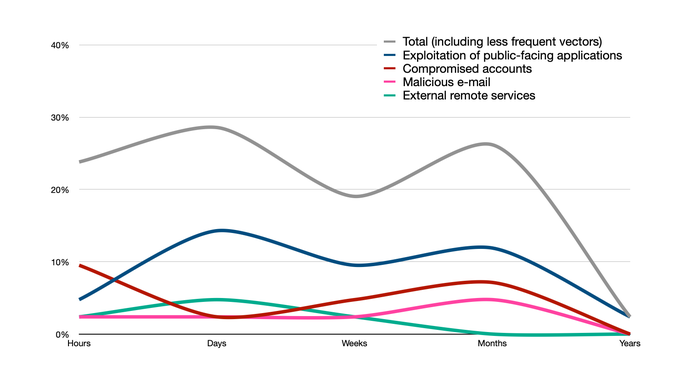
Exploitation is the top initial access vector and tends to lead to a quick ransomware attack or longer espionage. Source: Kaspersky
Tip: Track Exploitation Trends
Knowing the most common approaches attackers likely will take can help inform defenders. Companies should continue to prioritize vulnerabilities that have exploits in the wild, for example. By paying attention to the shifts in the threat ecosystem, companies can make sure that they are prepared for likely attacks, Mandiant's Kennelly says.
"Due to the velocity at which threat actors can weaponize exploit code to support intrusion operations, understanding which vulnerabilities are being actively exploited, whether exploit code is publicly available, and if a particular patch or remediation strategy is effective can easily save organizations from dealing with one or more active intrusions," he says.
But avoid putting too much emphasis on protecting against specific initial access vectors, as attackers continually adapt to defenses, Kennelly adds.
"The specific infection vectors that are most common at a given time should not broadly change an organization's defensive posture, as threat actors continually shift their operations to focus on whichever vectors prove most successful," he says. "[A] decrease in the prevalence of any given vector does not mean it poses a significantly lower threat — for example, there has been a slow decline in the proportion of intrusions where access was obtained via phishing, but email is still used by many high-impact threat groups."
About the Author
You May Also Like




