Sale of Stolen Credentials and Initial Access Dominate Dark Web Markets
Access-as-a-service took off in underground markets with more than 775 million credentials for sale and thousands of ads for access-as-a-service.
March 2, 2023

The cybercrime economy centered around access to compromised systems, services, and networks has grown dramatically in the past year — with a sixfold increase in the number of credentials stolen via malware and offered for sale.
With cyberattackers using information-stealing malware to gather credentials, the expansion of access-as-a-service offerings has blossomed in the criminal underground with thousands of advertisements offering would-be cybercriminals access to compromised systems, according to findings in Recorded Future's newly published annual report.
In addition, the collection of data, use of stolen accounts, and phishing are among the top 10 most-discussed tactics in cybercriminals forums, according to the report.
The analysis of the most popular topics from underground forums demonstrates that stolen credentials and the sale of initial access continue to dominate cybercriminal markets, says David Carver, a senior manager at Recorded Future's Insikt research group.
"Credentials are a massive business because they continue to be successful and profitable for criminals," he says. "So as long as there continues to be fairly easy ways to monetize credentials at scale, which has been true for criminal markets for a long time, I don't see the drive for that type of theft changing."
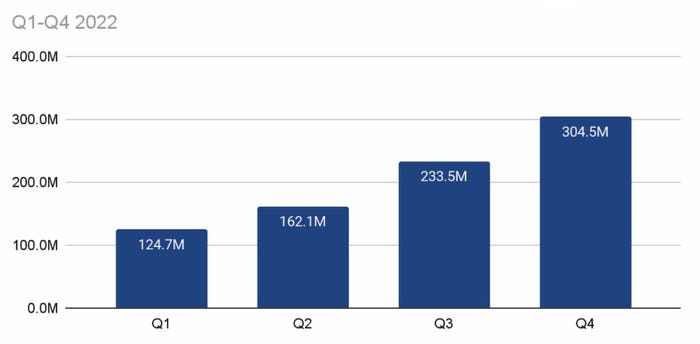
Stolen credentials logged by info-stealing malware grew significantly in 2022. Source: Recorded Future
A decade ago, cybercriminals focused on stealing valuable data or on compromising specific companies that not only could be exploited but would also pay the attacker to leave them alone. Yet with the popularity of ransomware and the ability to use cryptocurrencies as a method of payment, attackers have been able to monetize nearly any breach of an organization. Thus, selling stolen credentials and opportunistic access has become the go-to product of the underground economy.
MFA Fail
Deploying stolen credentials has become more difficult for cybercriminals thanks to multifactor authentication (MFA), but attackers have countered with bypass techniques for many types of MFA, so credential theft has continues to be a standard post-breach tactic and access-as-a-service continues to thrive, Recorded Future's Carver explains.
"Until either our concept or our fundamental methods around identity change, there's not going to be a change in the criminal market, or at least not in the way that we're seeing right now," he says.
In 2021, the attackers focused on finding valuable systems and encrypting them with ransomware, with data encrypted for impact (T1486) and system information discovery (T1082) topping the list of trending tactics, techniques, and procedures uncovered by Recorded Future. In 2022, cybercriminals shifted their focus to the collection of data from local aystems (T1005) and the use of valid accounts (T1078) for access, according to the "2022 Annual Report."
The trend shows that access has become increasingly important, as cybercriminals have more options than just ransomware to monetize compromised systems, leading to information-stealing functionality becoming popular, the firm said. Ransomware payments decreased by nearly 60% in 2022 compared with 2021, according to Recorded Future's data.
"Credential sales remain popular on dark web marketplaces, typically for use in account takeover and credential stuffing attacks," the report stated. "The tactic has grown in sophistication with the rise of information-stealing malware and the proliferation of the malware-as-a-service model."
Recorded Future would not discuss the specifics of where its credential numbers came from, but its researchers believe that they have captured evidence of at least half of total campaigns from major info stealers.
"This is as close to 'bare metal' as you can get in terms of what is being exfiltrated and exposed as part of multiple different info-stealer malware campaigns," Carver says. "So to some extent, we're getting these directly as a result of understanding what data that malware is pulling in."
Not Just Usernames and Passwords
An attacker's focus on collecting credentials following a compromise has evolved as more information about the user has become necessary to bypass some security controls. Now, attackers are likely to collect session tokens from the browser cache, geographical information, browser version information, and other data in addition to usernames and passwords, Carver says.
"When we think about credential theft, what we actually need to be thinking about is the kind of complete browser fingerprint that some of these info sealers are looking for," he says.
Companies should assume that threat actors have employees' basic credentials, and that multifactor authentication could be bypassed, Carver said. They also need to ensure they can detect anomalous account behavior.
"The absolute first thing that [companies should] look at is identity and access management, making sure that across the complete scope of identities or platforms, or users that have access to anything internal, that there is a really robust and well understood security program," he says. "To me, that's table stakes right now for a more secure program, given the rise of info stealers."
About the Author
You May Also Like
Catch the Threat Before it Catches you: Proactive Ransomware Defense
September 5, 2024How to Evaluate Hybrid-Cloud Network Policies and Enhance Security
September 18, 2024DORA and PCI DSS 4.0: Scale Your Mainframe Security Strategy Among Evolving Regulations
September 26, 2024Harnessing the Power of Automation to Boost Enterprise Cybersecurity
October 3, 2024
[Virtual Event] The Essential Guide to Cloud Management
October 17, 2024Black Hat Europe - December 9-12 - Learn More
December 10, 2024SecTor - Canada's IT Security Conference Oct 22-24 - Learn More
October 22, 2024



_Tero_Vesalainen_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
