CISA, MITRE Look to Take ATT&CK Framework Out of the Weeds
The Decider tool is designed to make the ATT&CK framework more accessible and usable for security analysts of every level, with an intuitive interface and simplified language.
March 2, 2023

The US Cybersecurity and Infrastructure Security Agency (CISA) has launched Decider, a free tool to help the cybersecurity community more easily map threat actor behavior to the MITRE ATT&CK framework.
Created in partnership with the US Homeland Security Systems Engineering and Development Institute (HSSEDI) and MITRE, Decider is a Web application that organizations can download and host within their own infrastructure, thus making it available to a range of users via the cloud. It's meant to simplify the often onerous process of using the framework accurately and effectively, as well as open up its use to analysts at every level in a given cybersecurity organization.
ATT&CK: A Complex Framework
ATT&CK is designed to help security analysts determine what attackers are trying to achieve and how far along they are in the process (i.e., are they establishing initial access? Moving laterally? Exfiltrating data?) It does this via a set of known cyberattack techniques and sub-techniques determined and refreshed periodically by MITRE, that analysts can map on top of what they might be seeing in their own environments.
The goal is to anticipate the bad guys' next moves and shut down attacks as quickly as possible. The framework can also be incorporated into a variety of security tools, and it provides a standard language for communicating with peers and stakeholders during incident response and forensic investigations.
That's all well and good, but the problem is that the framework is notoriously complex, often requiring a high level of training and expertise to select the correct mappings, for instance. It also continually expands, including beyond enterprise attacks to incorporate threats to industrial control systems (ICS) and the mobile landscape, adding to the complexity. In all, it's a sprawling data set to navigate — and cyber defenders often end up in the weeds when trying to use it.
"There are a lot of techniques and sub-techniques that are available and that can get very involved and very technical, and oftentimes analysts are overwhelmed, or it slows them down quite a bit, because they don't necessarily know if the sub-technique they're picking is the right one," James Stanley, section chief at CISA, says, noting that complaints about mis-mappings using the tool are common.
"When you go to the website, there's a lot of information in front of you and it gets daunting quickly. The Decider tool really just brings it into more plain language for an analyst to use, regardless of their level of expertise," he says. "We wanted to give our stakeholders more guidance on how to use the framework, and make it available to, say, junior analysts who could benefit from using it in real time during middle-of-the-night incident response, for instance."
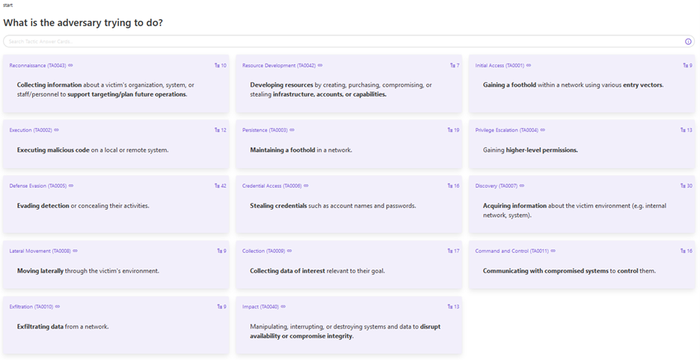
Decider uses a series of questions to guide analysts through the framework. Source: MITRE Corp.
On a broader level, proselytizers at CISA and MITRE believe that a wider use of ATT&CK — as encouraged by Decider — will lead to better, more actionable threat intelligence — and better cyber-defense outcomes.
"At CISA, we really want to put the emphasis on using threat intelligence to be proactive in your defense and not reactive," Stanley says. "For a very long time, the industry's go-to for that has been to share indicators of compromise (IOCs), which have very broad, very limited context."
In contrast, ATT&CK tips the playing field to the defense's advantage, he says, because it's granular and gives organizations a way to understand the specific threat actor playbooks that are relevant to their specific environments.
"Threat actors should know that their playbooks are essentially useless once we highlight what they do and how they do it and incorporate it into the framework," he explains. "Organizations that can use it have a much stronger security posture as opposed to just kind of blindly blocking IP addresses or hashes, like the industry is so used to doing. Decider gets us closer to that."
Simplifying ATT&CK for Analyst Accessibility
Decider makes ATT&CK mapping more accessible by walking users through a series of guided questions about adversary activity, with the goal of identifying the correct tactics, techniques, or sub-techniques in the framework to fit the incident in an intuitive way. From there, those results can "inform a range of important activities such as sharing the findings, discovering mitigations, and detecting further techniques," according to CISA's March 1 announcement of the new tool.
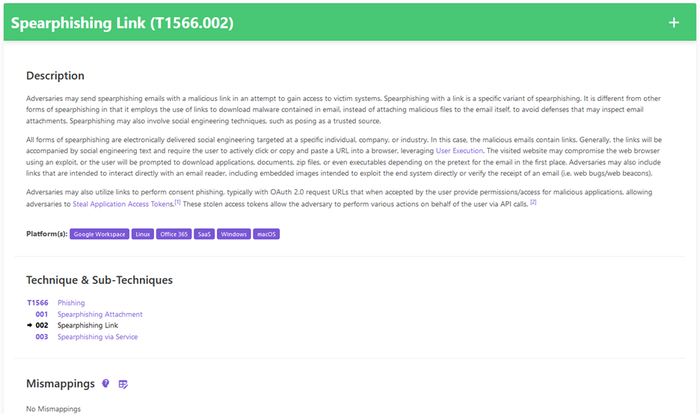
Decider uses simplified language and definitions for techniques and sub-techniques. Source: MITRE Corp.
In addition to the prepopulated guiding questions, Decider uses simplified language that would be accessible to any security analyst, an intuitive search and filter function for uncovering relevant techniques, and a "shopping cart" functionality that lets users export results to commonly used formats. Additionally, organizations can tailor and tune it to their own individual environments, including flagging common mis-mappings.
The hope is for ATT&CK to eventually become a foundational, background tool for cybersecurity organizations, according to John Wunder, department manager, CTI, and Adversary Emulation at MITRE, rather than the unwieldy, if useful, instrument that it has been.
"One thing that I would really love to see as ATT&CK moves more into the background is just a part of the day-to-day operations of cybersecurity and individual analysts just having to pay less attention to it," he says. "It's just something that should form the foundation of what we do and thinking about understanding adversary behaviors, and not something that you have to spend a lot of time thinking through each time you're doing an incident response. Decider is a big step forward to that."
The tool also helps ATT&CK's syntax to become the de facto common nomenclature across tools and security platforms, and for sharing threat intelligence.
"Once you see ATT&CK used across more and more of the ecosystem, and everyone using a common language, then the users of ATT&CK start to see more and more benefit from aligning things to the framework and using it to more effectively correlate tools and so on," Wunder says. "Hopefully through things like Decider that make it easier to use, we'll start to see more and more of that."
About the Author
You May Also Like
Catch the Threat Before it Catches you: Proactive Ransomware Defense
September 5, 2024How to Evaluate Hybrid-Cloud Network Policies and Enhance Security
September 18, 2024DORA and PCI DSS 4.0: Scale Your Mainframe Security Strategy Among Evolving Regulations
September 26, 2024Harnessing the Power of Automation to Boost Enterprise Cybersecurity
October 3, 2024
[Virtual Event] The Essential Guide to Cloud Management
October 17, 2024Black Hat Europe - December 9-12 - Learn More
December 10, 2024SecTor - Canada's IT Security Conference Oct 22-24 - Learn More
October 22, 2024



_Tero_Vesalainen_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
