Good News! IAM Is Near-Universal With SaaS
The less-good news: IAM only works for applications your IT department knows about, so watch for "shadow IT" programs installed or written by users that leave a security gap.
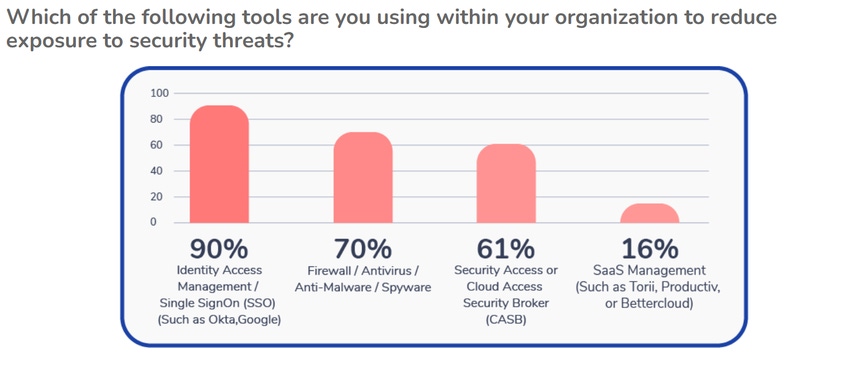
Almost every company implements identity access management (IAM) techniques such as single sign-on (SSO) to secure users who access software-as-a-service (SaaS) offerings, and most supplement that with measures like firewalls and cloud access security brokers (CASBs).
That's according to the 2022 SaaS Visibility and Impact Report from SaaS security provider Torii, which surveyed 100 technology executives to see how the pandemic has affected their IT practices and strategies. Nine of out 10 respondents (90%) say they use IAM/SSO to protect their networks, with 70% adding firewalls, antivirus software, and related safeguards. More than 6 out of 10 (61%) implement CASB or other security access guardrails related to secure access service edge, while 16% use SaaS management tools.
SaaS has become an indispensable part of business, especially during the pandemic-impelled push toward remote working. In the recent Dark Reading survey State of the Cloud: A Security Perspective, for example, half of respondents reported having 2 to 9 cloud applications in their organization. This new reality creates a need for tools that protect network resources: A recent study from Reposify showed that almost two-thirds of cybersecurity vendors had their back-office networks directly accessible from the Internet, and half had at least one exposed database.
An extra challenge springs from the decentralized work environment. Employees have started to solve their own problems by writing or installing their own software tools outside of the control of the IT department, a phenomenon known as "shadow IT." These programs, while often useful for solving immediate challenges, can create security holes when IT doesn't even know the tool exists.
Both CASBs and SaaS management tools can plug up shadow IT holes, while IAM and firewalls tend to be blind to uncatalogued software. For more, read the full report here.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




