
News, news analysis, and commentary on the latest trends in cybersecurity technology.
Organizations are also looking at threat intelligence, risk assessment, cyber insurance, and third-party risk management.
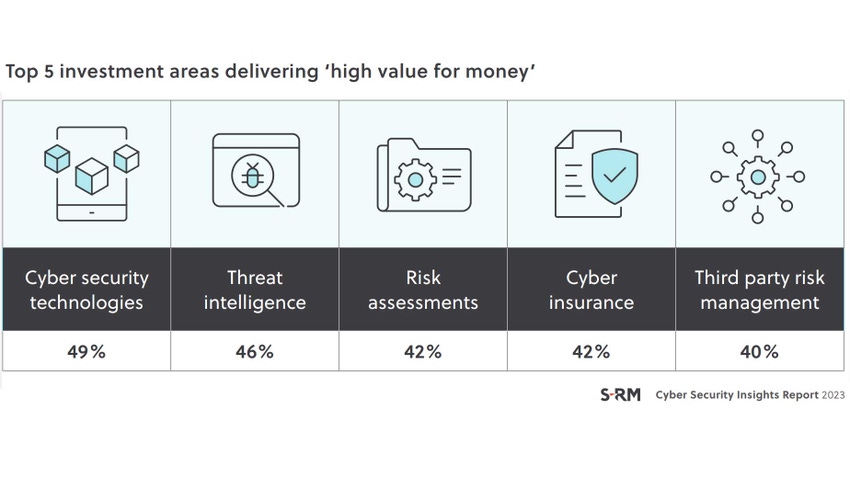
Organizations are looking for a "high value for money" when deciding how to allocate their cybersecurity budgets, and there is a "greater focus on getting value from existing resources," according to S-RM's "Cyber Security Insights Report 2023." The report, which reflects responses from 600 C-suite business leaders and senior IT professionals within large organizations, found that the top five investment areas were cybersecurity technologies (49%), threat intelligence (46%), risk assessment (42%), cyber insurance (42%), and third-party risk management (40%). Fewer organizations highlighted technology as good value for money in 2023 (49%) than in 2022 (58%). suggesting an awareness that technology investments go hand-in-hand with investing in governance and personnel to effectively enable and manage the technology.
That awareness may be more prevalent among IT professionals than C-suite business leaders because the IT professionals are more immersed in the day-to-day minutiae of security operations. Consider that 43% of IT professionals cited technology as a "high value" investment area, compared with 56% of C-suite executives.
The difference was even more stark for cyber insurance, with C-suite business leaders seeing greater value for their money (48%) than IT professionals (36%) in having a cyber-insurance policy. The report speculated the difference could be because the C-suite is focusing on potential business interruption and regulatory and reputational impact as a result of a security incident and not just the damage to the IT infrastructure. C-suite business leaders are also more likely to rely on insurance to mitigate more than just the costs associated with remediation of technical infrastructure, according to the report.
Nearly a third of respondents said lack of budget (31%) is a key security challenge, a clear indicator that the budget they want is not the budget they are getting. Cybersecurity accounted for about a quarter of the organization's overall IT budget in 2023, according to the report. This was the case for the following sectors: financial services (25%); extractives, which includes mining, oil and gas drilling, and forestry (25%); legal (24%); and insurance (24%). There were a handful of sectors with budgets slightly more than a quarter of the IT budget: retail (28%), telecommunications (27%), pharmaceuticals (27%), and private equity (26%). Energy and utilities segment stood out for its underinvestment (18%).
The gap between expectation and reality has been fairly consistent over the years, according to the report. The average cybersecurity budget for a large organization rose by 3% year-on-year, which is less than the 5% increase the respondents had predicted they would see in 2023. Respondents had anticipated an 8% increase in their cybersecurity budgets in 2022 but saw an actual increase of just 5.1%. As such, it is likely that organizations will see a smaller, more modest, budget increase in 2024 than the hoped-for 8%.
Organizations also recognize that investing in technology also means getting the right people and governance in place. Respondents said they anticipate an increase in their security budgets in order to invest in people. Nearly an equal number of respondents said the budget increase is tied to upskilling the existing security team (42%) and to hiring more skilled personnel (41%).
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

