1 In 5 Companies Cutting IT Security Spending, Our Survey Finds
Budget woes, increased regulation, and new challenges for sensitive data are on the menu for risk managers.

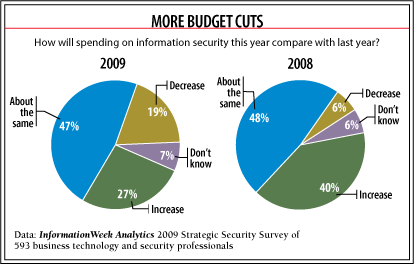
Cutting IT security spending, unthinkable a couple of years ago, is officially on the table. Just a year ago, even with a recession taking hold, only 6% of companies planned to trim security. This year, 19% are cutting, our Strategic Security Survey finds, while only 27% are increasing spending on IT security, down from 40% who were a year ago. (Download the full report).
At the same time, CEOs desperate to make their quarterly numbers may enter new businesses or find ways to trim expenses with less concern for the impact on data security. If you thought you had a handle on your organization's appetite for risk, chances are the economy has changed the dinner portions.

While it's no surprise that regulatory compliance and budget pressure show up in our annual survey as high-stress items, we were somewhat surprised by the number of respondents struggling to figure out how to assess the risks inherent in the various forms of cloud computing. Because the potential for saving money through the use of cloud services is real, security pros are being pressured to figure out just how risky those services are. Ironically, one of the hardest things to assess about cloud services is their effect on regulatory compliance.
Our survey shows that compliance is the main goal of risk management initiatives, and compliance tied with internal audits as the No. 1 measurement of success. "Compliance is making people do things to stay out of jail, changing security from a 'should' to a 'must,'" says Ira Winkler, CEO of consulting firm ISAG. Winkler laments that highly secure organizations have to spend on compliance testing to prove they're secure. But, he says, "organizations lacking in security are much better off today because of compliance since they have had to establish better practices and processes."
Companies that do security well have the same staffing and funding obstacles as any company, but they focus on managing risk and protecting data. They know their appetite for risk and they manage to it, rather than think of security as a checklist of requirements. They can't secure everything, so they identify their most important assets and the likelihood of loss, and put programs and controls around them for protection.
For example, Payment Card Industry (PCI) Data Security Standards require that antivirus software be installed on all systems that are "commonly affected by malicious software." So does that mean Apple's Mac OS X is exempt because it's not commonly affected by malicious software? Antivirus software is supposed to detect all known malware, but known malware isn't the problem, now is it?
DIG DEEPER
Get Strategic
Our annual Strategic Security Survey is available for free for a limited time
See all InformationWeek Analytics Reports
Simply put, compliance best practices aren't necessarily security best practices. What if a company used a combination of host hardening, remote user access with no clipboard or file sharing between the host and the remote desktop, and segregated networks to put a moat between users and applications in such a way that malware couldn't get to sensitive data? And what if that company could show that its systems were thus well protected against malware? Would that be satisfactory? No, because PCI requirement No. 5 calls for antivirus protection.
Using antivirus software is considered an industry best practice, but "best practices were created by the legal community to defend litigation in court so the organization can say they were following best practices," says John Pironti, president of management consulting firm IP Architects. Both sides bring in expert witnesses, and the most convincing expert wins.
Best practices aren't worthless, but they're not one size fits all, and are too often applied without regard to context. The types of attacks against Heartland Payment Systems, Hannaford Brothers, and TJX took planning and expertise. They weren't conducted by kids downloading pre-compiled tools--the types of attacks that would be stopped by companies that implement the bare minimum "best practices." And that is fundamentally the difference between check-box security and risk management.
Head In The Clouds
If you think you have risk management in hand, chances are cloud computing will shake that confidence. Assurances about data segregation, privacy, and security, while nothing new, take on added dimensions in cloud services because you don't know where your data is most of the time. Don't think cloud computing will affect your organization? It will. Surveys conducted by Deloitte's Security & Privacy Services show that many companies already have moved to some outsourced computing "because you can't argue with the dollars," says Deloitte partner Rena Mears. "Stop asking if cloud computing is going to happen. It's already happening."
Knowing data's location is fundamental to securing it, and the location of data may have significant legal implications. It's a problem that Chiquita Brands tackles head on when considering external service providers. "The first step for Chiquita," says CIO Manjit Singh, "is to understand the regulatory requirements for every country we operate in. We then know the requirements we need to meet to protect our sensitive data internally. Then we have to ask ourselves and local authorities what an external provider needs to show to demonstrate they can protect our data as well as Chiquita."
To do that, cloud and software-as-a-service providers have to agree to periodic security assessments by external auditors chosen by Singh's team, and Chiquita must thoroughly understand the policy and procedures of the service provider, including who has access to the company's data and equipment. For example, Singh points out that many providers have one policy governing their contractors and another for their own employees. In other cases, the provider may outsource part of its operations to yet another a service provider. "You need to be aware of what's going on in the facility and not just what relates directly to yourselves, which is a step a lot of companies miss," he says.
The economics of cloud computing are so compelling that SaaS vendors are starting to host their applications in a cloud service. Two examples are point-of-sale software vendor PayGo and healthcare information manager MedCommons, both of which use Amazon.com's Elastic Compute Cloud as an option to host their SaaS offerings. For providers like them, data may go through a chain of hands, all of which need to be known and evaluated.
Assessing The Cloud Threat
As the Chiquita example points out, assessing cloud security is difficult and ongoing. Providers are inclined to ask you to trust that they're handling your data securely, without providing a mechanism to verify if that trust is warranted.
One instrument often suggested for verification is SAS-70 assessments. SAS-70 is a standard that dictates how audits of service providers should be done, but the assessments cover only the operations that the provider wants covered, and often the only document you get to see is the auditor's statement of opinion, which provides an overview of the scope of the assessment and whether the organization does what it says it does. What you don't see, and what consultant Pironti recommends that providers not reveal, is the detailed auditor's report, which lays out what the assessor found, including the tests performed.
Deloitte's Mears is of the opinion that generally accepted practices will be developed for cloud computing providers to communicate clearly what they're doing to comply with requirements to secure and manage sensitive data. "Providers can't let everyone do their own assessment," she says. "It's not sustainable for them."
One group that's generating some buzz is the Cloud Security Alliance, a group comprising industry and customer organizations. The group's initial Security Guidelines document includes a set of questions to ask providers, and another set to ask about your own organization's readiness to adapt to cloud services. Jim Reavis, co-founder of the alliance, expects version 2.0 to be ready by October, providing more specific guidance, exploring the threats to cloud services in more detail, and providing more precise definitions.
Reavis believes it eventually will be mandatory for cloud providers to pass a security certification. The challenge for CSA is to create certification requirements that don't suffer from PCI's snapshot-in-time problem and that are directly applicable to cloud environments. In addition to working with the Information Systems Audit and Control Association, CSA will likely work with the American Institute of Certified Public Accountants, the International Organization for Standardization, auditing and security groups, as well as enterprise IT, service providers, and other stakeholders to come up with meaningful assessment and certifications, Reavis says. CSA is gaining support with backing from big-name companies like Dell and eBay, as well as cloud providers.
Chiquita's Singh says certifications are a starting point, but "we and other Fortune 500 companies wouldn't be satisfied with a certification. We'd still require the right to have our own auditors perform an assessment. SMBs might be satisfied with them, but global companies view certifications as a starting point, from which we exercise the extra diligence of our own assessment to our requirements."
Money Makes The World Go Round
Despite economic pressures, compliance programs are getting funding because companies have no choice. Adam Ely, a former senior information security manager at Disney turned consultant, sees companies saying, "Let's do what we have to do to get through the next audit." That mind-set increases spending for and awareness of compliance, consultant Pironti notes, but it subverts the discussion about ongoing risk management.
Not everyone sees an increase in spending on compliance. Mike Healey, president of integrator Yeoman Technology Group and an InformationWeek contributing editor, notes that as tech funding and staffs are kept flat or reduced, even compliance audits are back-burnered "because audits aren't front-line defense." Two years ago, Healey says, "organizations had audit schedules or did it themselves. Today, they're prioritizing efforts elsewhere."
Beyond regulations, federal, state, and local laws also affect security spending. Breach notification laws didn't tell companies how to protect data; they just require that companies tell their customers when they've lost their custom- ers' data. But because no company wants to end up in a data-breach headline, those laws have been among the biggest drivers of information security spending. Similarly, laws in Massachusetts, Nevada, and other states for protecting personal information on devices containing sensitive data will certainly drive up spending for any company doing business in those states.
Security vendors are creating products to meet the new laws and regulations, but watch out for snake oil. "The side effect of compliance is that a lot of vendors are just repurposing old products as compliance solutions," says consultant Ely. "The repurposed products are claimed to solve items on the PCI checklist or standard governance, risk, and compliance initiatives." Even the governance, risk, and compliance software market, where products help you score, assess, and manage risk, is seeing an explosion of new products--not all of which are particularly useful.
One practice that Ely sees as increasingly popular and useful is data masking, a process that replaces sensitive data with legitimately formatted fake data. Here's how the practice works. Organizations have to test new applications and application patches on test systems before applying them to live systems, and they have to protect private data. Developers and testers--particularly those outside a company holding sensitive data--shouldn't be allowed to view private data, but they have to work with valid data to test their applications and patches. Data masking, for which there are many techniques and products available, generates valid but obfuscated functional data. It's a relatively straightforward process that should be employed for outsourced development tasks.
Ely also sees enterprise rights management as an increasingly useful technology because ultimately you need to manage access to data wherever it resides. Rights management controls who can do what to data. Policies define the controls required to read, write, or modify a document. Often the data is secured via encryption, so if it's sent outside the realm of the digital rights management system, it can't be viewed.
The major difficulty with rights management is a lack of standard formats and interfaces among products and operating systems to uniformly manage rights. For example, if you and a partner want to exchange documents protected by rights management, you'd have to use the same system. It's good for relatively small communities of interest but doesn't scale well to a global environment. Standardized formats and protocols must be developed and implemented in products.
Work To Do
Robert Richardson, director of the Computing Security Institute, thinks there's still work to be done in the more mundane parts of security, like log management and how it relates to security and compliance. "In many cases where there is a breach, there were flags indicating a breach but they were never noticed," Richardson says. "It's like trying to find a needle in a stack of needles because most events look pretty much the same. Practitioners tell me they have a hard time getting the funding for log management because it sounds dull, but it's a necessary tool." Log analysis tackles a number of challenges, from simply getting all the logs in one location, to normalizing them, to understanding what the logs are saying and then correlating individual entries to a particular event.
Southwest Washington Medical Center makes extensive use of its health application logging facilities, says Christopher Paidhrin, the hospital's IT security and compliance officer. "Actions like accessing or modifying records are recorded so that in the event of an incident, we can trace an employee's steps," he says. "Most improper record accesses are accidents, and we can see that from the short duration of the access and the lack of a pattern of unauthorized access attempts when a mistake is made."
Paidhrin admits that much of the hospital's log monitoring is reactive, but like all security programs, it's evolving. Simply managing the volume of events and making sense of the relevant ones requires going beyond log management software to correlate discrete events into security alerts.
That's the job of security event management systems. These big SEM systems can cost a quarter of a million dollars and then take lots of care and feeding, putting them out of reach of many organizations. Seeing a vacuum, log management vendors have been adding SEM-like capabilities such as smart searching, reporting, trending, and graphing to their product lines, but those features are a long way from correlation. Both PCI and HIPAA have language requiring regular log management and review as a best practice.
As we concluded after last year's Strategic Security Survey, don't focus on tactical missions like regulatory compliance and cloud computing; focus on the strategic mission of information security via risk management. Whether your sensitive data is in your own data center, in a cloud service, or replicated between the two, the same privacy requirements apply. Prioritize your risk requirements, determine which steps must be taken to protect your information, and then figure out what technology, product, or processes you need to mitigate your risk.
About the Author(s)
You May Also Like
Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




