How to Spot a ChatGPT Phishing Website
Scammers are leveraging the popularity of ChatGPT in phishing attacks. Here's a look at research on these newly registered domains and tactics.
May 4, 2023

Hackers will always take advantage of the hot thing: COVID-19, crypto, tax season, or what have you. And with the rise of ChatGPT, they've not missed a beat.
Through the first four months of 2023, researchers from Check Point tracked 13,296 newly registered domains relating to Open AI and ChatGPT. According to new research from the company, one in 25 of those domains were malicious.
The fake sites tend to unsubtly project their relation to ChatGPT, with examples like:
chat-gpt-pc.online
chat-gpt-online-pc.com
chatgpt4beta.com
chatgptdetectors.com
chat-gpt-ai-pc.info
chat-gpt-for-windows.com
Some of the fake sites take the obvious route, copying OpenAI's actual landing page as closely as possible:
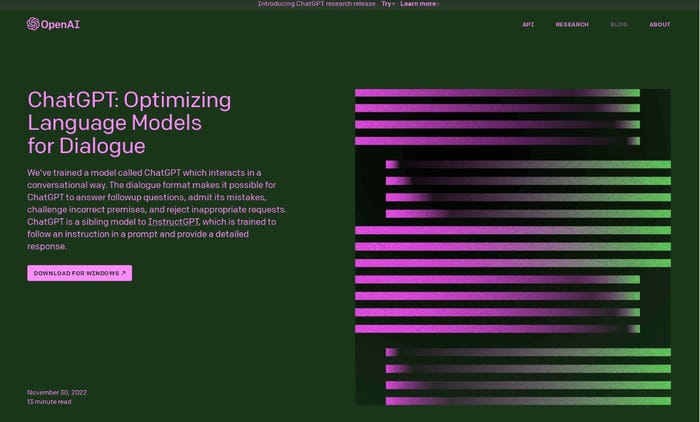
Source: Check Point Research
Other lures take a different approach. Rather than impersonating OpenAI, they pretend to offer related services.
For example, the following landing page purports to offer software for detecting ChatGPT prose, something educators in particular have been calling out for in recent months:
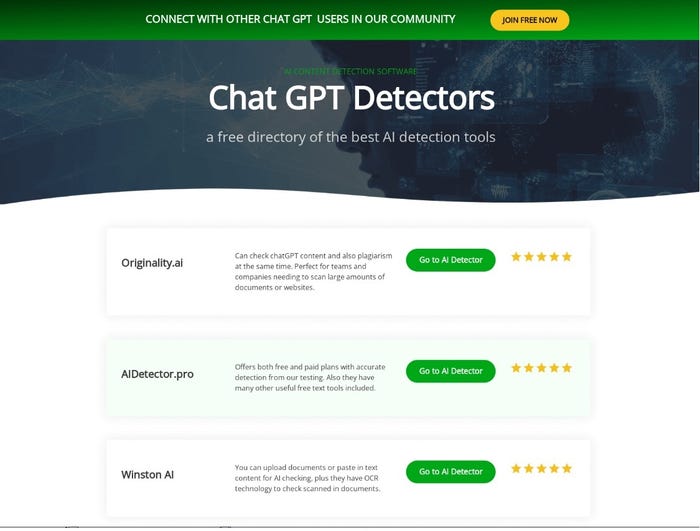
Source: Check Point Research
Beyond the threat to individuals, "there are two main potential problems here for enterprises," notes Omer Dembinsky, data group manager at Check Point Software, and the lead researcher behind the report.
"One issue is that employees can download malicious files and applications from those websites, and thus provide cybercriminals with an initial foothold on their corporate network," he says. "The second issue is that the websites mimic ChatGPT so well that employees can potentially fall for their disguise and can submit queries with sensitive corporate information to those fake websites."
What to Do
To avoid falling for one of these traps, the researchers recommended attentiveness and basic cyber hygiene around phishing emails. Specifically:
Don't reply, click on links, nor open attachments in unverified emails
Report suspicious emails to your IT or security team
Delete suspicious emails
Be on the lookout for lookalike and fake domains
However, the researchers caution that "while awareness of common phishing tactics and knowledge of anti-phishing best practices is important, modern phishing attacks are sophisticated enough that some will always slip through."
And so, Dembinsky says, enterprises need to both educate their workforce and implement effective anti-phishing mitigations.
About the Author
You May Also Like
.jpg?width=100&auto=webp&quality=80&disable=upscale)
.jpg?width=400&auto=webp&quality=80&disable=upscale)


