
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
2022 Security Priorities: Staffing and Remote Work
A comprehensive security strategy balances technology, processes, and people — and hiring and retaining security personnel and securing the remote workforce are firmly people priorities.

Almost five months into 2022, acquiring and retaining security personnel and securing the remote workforce are two things top of mind for security leaders.
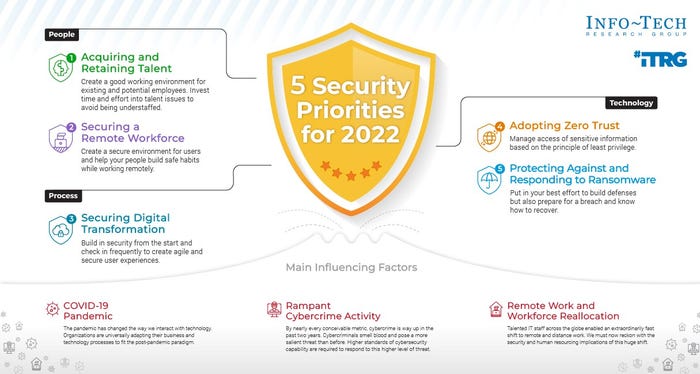
That's according to analyst firm Info-Tech Research's 2022 Security Priorities report, which lays out both the top priorities and the main obstacles for security leaders. The other three top priorities are digital transformation, zero trust, and ransomware. The priority list is strongly influenced by the COVID-19 pandemic, the increase in cybercrime, and the shift to remote work, according to Info-Tech Research.
Nearly a quarter of the respondents (23%) named securing the remote workforce as their top priority for 2022. That includes both implementing security controls to create a secure environment for users and helping employees build "safe habits," the research firm said.
Source: Info-Tech Research
Pandemic-driven changes like the shift to remote work "are largely expected to remain, regardless of the progression of the pandemic itself," Info-Tech Research said in its report. This is consistent with Dark Reading's 2022 Endpoint Security Survey, where 48% of respondents said they made changes to their endpoint security strategy to accommodate the shift to work-from-home in the early days of the pandemic — and 54% don't plan on shifting back to how things were before the pandemic.
Along with remote workforce security, the other top priority in the people category was hiring skilled cybersecurity professionals and creating a good working environment for existing employees. Retention is very important, as being understaffed means new security initiatives are placed on hold and existing security projects may be delayed. In fact, 31% of respondents cited staffing constraints as their biggest obstacle.
"The pandemic has changed how people work as well as how and where they choose work," Info-Tech Research found, noting that "Most smart, talented new hires in 2022 are demanding to work remotely most of the time."
This create a bit of a tangle for security leaders, who want to attract top talent by giving them the flexible work environment they are asking for, but the shift to remote work exposes organizations to more costly cyber incidents, according to Info-Tech Research. The cost of a data breach rose by nearly 10% over the past year, with the average cost at $4.24 million, Info-Tech Research said, citing figures from IBM's Cost of a Data Breach report. The average cost of breaches where remote work is involved is $1.07 million higher, suggesting that ubiquitous remote work will continue to result in more costly security incidents.
Part of the reason for the higher costs may be because "it takes two months longer, on average, to detect and contain a breach when more than 50% of staff are working remotely," the report said, citing IBM.
Security leaders need to reassess the enterprise security strategy to consider the work-from-home attack surface, especially endpoint visibility, and to enable strong authentication requirements, such as multifactor authentication (hardware tokens for high-risk users) and VPNs for restricted sessions.
With remote work, it is even more imperative that security leaders develop a zero trust strategy in order to minimize the blast radius in case of a breach. Zero trust, coincidentally, happens to be one of the top security priorities, which we'll cover next week.
About the Author
You May Also Like

