Properly Framing the Cost of a Data Breach
The expenses and actions typically associated with a cyberattack are not all created equal. Here's how to explain what's important to the C-suite and board.
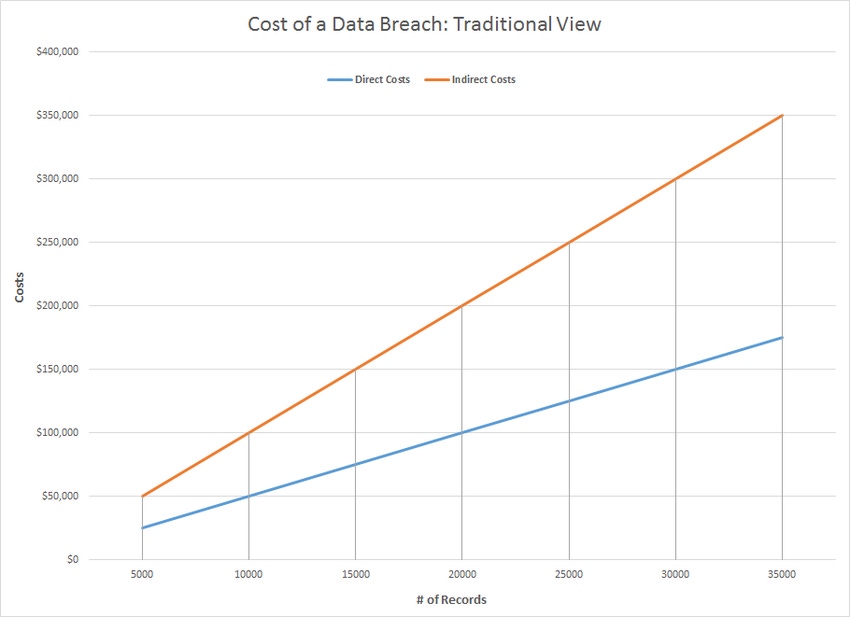
There is a lot of research, including Ponemon’s annual Cost of a Data Breach study, which does a good job of quantifying the average cost of each record lost across a large sample of records. Ponemon reasearch also provides some really interesting information related to the difference between direct and indirect costs of a breach across multiple countries. It is a must-read for me every year as soon as it is released.
However, the challenge with leveraging current cost of a data breach reports with the organizations I work with is that this type of research, when applied, yields a graph of breach cost by size that is linear in nature.
From my experience, such a graph does not reflect reality. It’s far too simple. What's missing from traditional linear charts are at least two major inflection points that represent the escalation of awareness surrounding an organization’s breach.
Who Knows What, When?
All breaches incur a minimum cost related to identification and remediation, essentially a minimum cost of entry. This entry point is followed by a flattening curve until the size of the breach hits its first inflection point – organizational awareness. In addition, there are two thresholds that may cause a second and even a third inflection point. These thresholds relate to general public awareness and press coverage.
The trigger for a second inflection point is when security nerds like me pay attention, start talking about it, start writing about it, and begin using it as examples in presentations, podcasts and blogs. A third inflection point is triggered when a breach becomes big enough news that it hits the mainstream and everyone becomes aware of it. You can use different logical tests to determine whether a breach has hit mainstream, but I like the non-technical family member test. This is when my least security-minded or technically inclined family member starts asking me about a breach. At that point, I know it is a mainstream event.
The existence of the inflection became apparent to me as I was reading an entertaining report in USA Today about the top 20 most hated companies in the United States. As I scrolled up the list from the bottom, I passed Harvey Weinstein’s company, airlines that beat and bloodied their passengers, and companies that have experienced various public relations disasters. In the number one spot I found Equifax. Another article, about Equifax, described how, as a publically traded company, it lost 31% of its marketplace capitalization, totaling over $5 billion, a measure of the value of their company, since the breach.
Breaches that Increase Data Breach Costs
Another fun research project is to look at inflection points that reflect an increase in the cost of a data breach. For example, if you review Target’s topline sales in Q3, the year of the breach, and Q3, the year after, you will see a decline in sales of more than $1 billion, or 20%. This is in an industry sector that actually grew during the same period. So, while the initial breach occurred over a set period of time, the organization continues to experience longer-term effects.
Bottom line: if an organization does not properly disclose, does not know the extent of a breach, or isn’t forthcoming with information to the public, the additional negative publicity will increase the indirect costs related to a breach.

Chart 2: Data breach cost estimates as they actually happen. (Source: Jeremy Wittkop)
If a CIO, CISO or other person responsible for maintaining data security is only providing damages associated with a cost per record to the rest of the executive team, the executive team or board may not be thinking about, or be able to visualize, how different types of incidents would monetarily affect the organization. To do so, you must account for different categories of incidents, and what the inflection points represent. A minor event (Inflection Point 1: Security incident becomes more widely known), won’t gather much attention outside the organization, and is often accidental. It typically can be minimized with commonly available security tools and may not be required to be reported externally.
The second type of event (Inflection Point 2: Security incident hits the mainstream.) occurs when organizations start to evaluate brand impact and the cost per record starts to increase. Most security professionals, for example, are familiar with the Deloitte breach, but most non-security people are not.
The final breach category (Inflection Point 3: Ongoing media coverage and remediation.) would likely make the nightly news and have a major impact on enterprise value. The majority of companies in the world do not have enough data for a breach rise to this level. However, for those that do, there are few security expenses that are not justified if they can materially impact the likelihood of such an event.
I am not proposing that companies hide breach incidents from their clients. My point is that costs associated with events are not equal and do not follow a linear path. The type of incident, its size, overall impact, and the mitigation process all affect the actual cost of a breach, which is a concept that is critical for executive teams and boards to understand. As security professionals, we must spend more time trying to build and perfect realistic investment models, and less time cheapening our mission by sowing seeds of fear, uncertainty and doubt. All of that starts with calculating the true cost of a data breach.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




