Network Data Shows Spikes, Vulnerability of Work-at-Home Shift
Traffic on the public Internet has grown by half this year, and videoconferencing bandwidth has grown by a factor of five, all driven by remote-work edicts.
April 13, 2020
As social-distancing mandates forced employees to work from home, bandwidth consumption and potential security weaknesses have risen, according to data from network providers and network-intelligence firms.
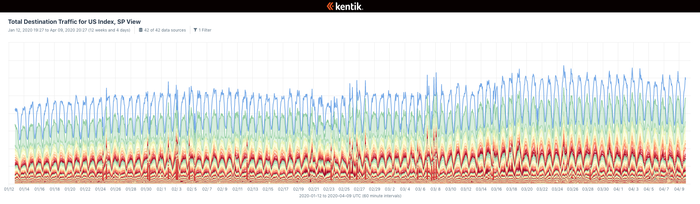
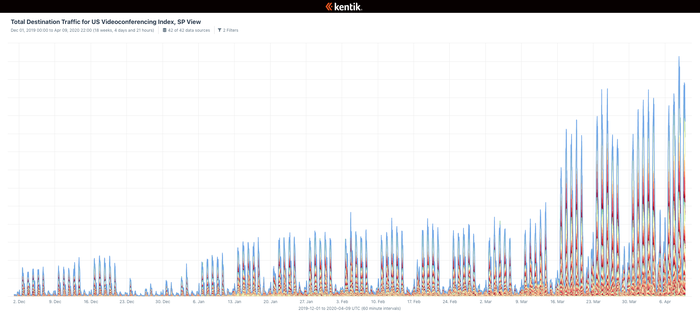
Traffic on the public Internet jumped by half since the beginning of the year, as employees moved to remote work, with videoconferencing seeing the greatest increase — 500% — according to Kentik, a provider of machine-learning-based network operations. Overall, the week-to-week growth in bandwidth consumption matched the month-to-month growth seen last year, says Avi Freedman, co-founder and CEO of Kentik.
Total Destination Traffic for US Index (click to enlarge)
Total Destination Traffic for US Videoconferencing Index (click to enlarge)
Network providers, in general, have handled the spikes in bandwidth consumption well, he says.
"Across broadband and transit networks, the first surges in growth this year were generally handled by existing overprovisioned capacity," Freedman says. "It has put a lot of networks into accelerated growth mode, which has also meant the usual kind of 'micro outages' but accelerated into a compressed time frame. However, it hasn't caused [many] large-scale or sustained outages."
Yet there are signs that the move to remote work caught many companies by surprise, leaving them with weaknesses in their infrastructure.
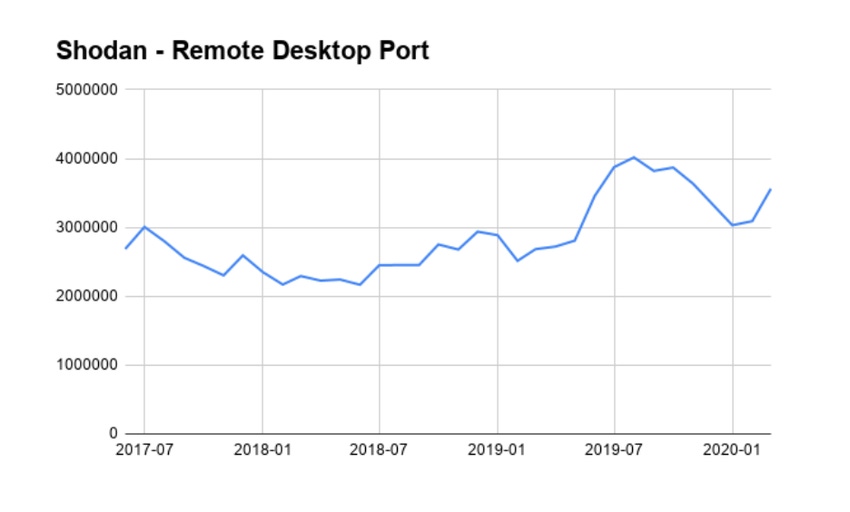
Data from the end of March collected by port-scanning service Shodan suggested that the number of systems exposing the remote desktop protocol (RDP) had increased in the past month and continued a general two-year trend of increased exposure.
At the same time, the number of Internet source scanning for the most common RDP port, 3389, jumped by 40% in March, according to the SANS Institute.
Overall, companies are finding that they are living their disaster plans, says Kentik's Freedman. If they had a good disaster plan, they are doing well. If not, they are having problems transitioning.
Companies "are focusing on helping and holding their organizations together, but across 30-plus customers I’ve talked to recently, almost all of them already had substantial remote [work provisions]," he says. "So even though they've had to go from 'situation usual,' some systems were already in place — or at least described — and able to assist in reacting quickly to new work habits."
Peak Movement
Comcast, the operator of the largest residential Internet network in the United States, has seen peak Internet traffic increase by 32% — 60% in some markets — along with a 24% increase in mobile data usage, according to the company. In addition, while 9 p.m. local time was the peak download time across residential markets, now 7:30 p.m. is the peak time, perhaps reflecting a lack of commute time before workers sit down to relax. More interestingly, the peak upload time has shifted from 9 p.m. to during work hours, although the exact time differs.
Comcast also saw virtual private network (VPN) traffic jump 40% and videoconferencing traffic rise 212% since March 1.
"We are seeing an unprecedented shift in network usage, but it's within the capability of our network," the company states on a page dedicated to its response to the shift, adding that "while the COVID-19 experience is new and unprecedented, the internet ecosystem is flexible and performing the way it was designed."
Remote Work Causes Initial Rise in Exposed Desktops
To keep business going and employees working, many companies exposed desktops to the Internet for direct connection. A common, but often insecure, protocol for accomplishing this is RDP.
Scanning service Shodan saw an increase in exposed RDP ports — both the standard 3389 and an alternate 3388 — from January to February.
More attackers focused on the protocol as well, according to data from the SANS Institute. The group saw an approximate 40% increase in the number of RDP sources.
"This is attackers expecting to find more vulnerable RDP servers, so they are scanning more," says Johannes Ullrich, dean of researcher at the SANS Technology Institute. "There is not a huge shift, but that increase is there."
Uneven Impact
The work-at-home mandate has also exposed the inequities in broadband access for rural and urban communities. Nearly a quarter of households do not have a broadband connection, which includes more than 4 million schoolchildren, according to consumer-focused publication Consumer Report.
Overall, providers see few major hurdles for network stability in the future, but the uneven distribution of high-speed Internet is apparent in the network data as well, Kentik's Freedman says.
"We're starting to see unequal effects of the COVID-19 situation on health and outcomes, but while things are going OK for the 'already connected,' there is some concern about what might happen if remote education is the default for the fall," he says. "There are already communities where organizations are opening Wi-Fi because there is insufficient quality of reach of broadband — for rural areas as well as more urban neighborhoods."
Related Content:

A listing of free products and services compiled for Dark Reading by Omdia analysts to help meet the challenges of COVID-19.
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's featured story: "When All Behavior is Abnormal, How Do We Detect Anomalies?"
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's featured story: "When All Behavior is Abnormal, How Do We Detect Anomalies?"
About the Author(s)
You May Also Like
Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024Finding Your Way on the Path to Zero Trust
May 22, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024