Empower Your Security Operations Team to Combat Emerging Threats
When examining the modern threat landscape, empowering your security operations and overcoming the limitations inherent with other malware prevention solutions is imperative.
July 7, 2022

The implementation of defense-in-depth architectures and operating system hardening technologies have altered the threat landscape. Historically, zero-click, singular vulnerabilities were commonly discovered and exploited. The modern-day defensive posture requires attackers to successfully chain together multiple exploit techniques to gain control of a target system. The increased utilization of dynamic analysis systems has driven attackers to evade detection by requiring input or action from the user. Sometimes, the victim must perform several manual steps before the underlying payload is activated. Otherwise, it remains dormant and undetectable through behavioral analysis.
It is well known that client-side attacks are the predominant access vector for most initial access. Web browser and email-based malware campaigns target users through phishing, social engineering, and exploitation. Productivity and business tools from vendors like Adobe and Microsoft are widespread and provide attackers with many options. Combining the lack of security awareness training and well-developed social engineering tactics frequently results in users permitting the execution of malicious embedded logic like weaponized macros or other scripts. Analysis of these common malware carriers is time-consuming and tedious, and it requires expert skills. To adequately prevent, detect, and respond to these threats, an organization must throw everything at the problem and augment this previously human-intensive process.
Deep File Inspection (DFI) is one approach to ease the burden associated with continuous security monitoring. DFI is a static-analysis engine that inspects beyond Layer 7 of the OSI model, essentially automating the work of your typical SOC analyst or security researcher. Regardless of the complexity of evasive techniques a threat actor utilizes, DFI dissects malicious carriers to expose embedded logic, semantic context, and metadata. Coercive graphical lures are extracted and processed through a machine vision layer, adding to the semantic context of the original file. Commonly used obfuscation methods and encoding mechanisms are automatically discovered and deciphered.
A public concern that SOC analysts, IR teams, and security researchers encounter is the limited availability of context for detection analytics. In the case of intrusion prevention systems, resources are limited to microseconds of time and kilobytes of analyzable data. Intrusion detection systems can typically dig deeper, taking additional milliseconds to expose further data.
Regarding the time-analysis trade-off, the next step up is behavioral monitoring or sandboxed execution. This class of solutions detonates samples in a virtualized environment and annotates the system's behavior for threat detection; this process is both compute- and time-intensive, taking minutes to analyze each file. There is a middle ground where a few additional seconds can provide previously unseen detection opportunities.
Use Case: Qbot Malware Delivered via Follina and Malspam
An example of an evasive threat is the recent TA570 campaigns that delivered Qbot malware with thread-hijacked emails. This wave of malspam utilized two different methods to provide the payload. The first method used a shortcut LNK to run a DLL with the hidden attribute. The second method is a Word document using the Follina (CVE-2022-30190) exploit.
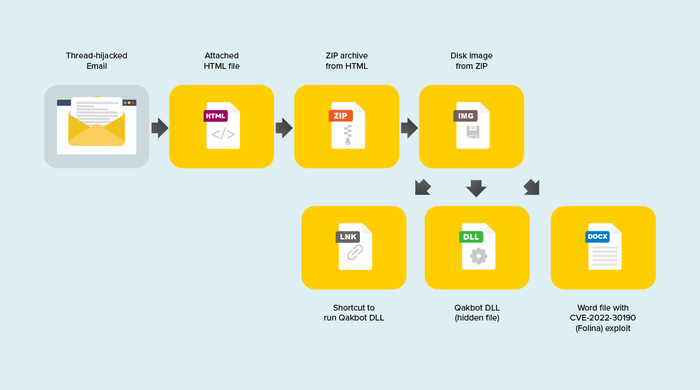
Figure 2. Recent Qbot threat sequence. Source: InQuest
The attached HTML file contains an antiquated JS function to convert the embedded base64 string into a zip archive and prompt the victim to download. When extracted, the zip file contains a disk image that will be mounted showing either a shortcut or the shortcut and word document. The shortcut will execute the Qbot DLL within the directory with the hidden attribute set. At the same time, the Word file will attempt to exploit the MSDT vulnerability and download the payload from a remote server.
It is challenging for many solutions to carve the zip archive from the encoded HTML, extract the IMG file, and identify the weaponized contents. In this example, multiple threat signatures are seen from ambiguities within the SMTP headers, down to the hidden DLL or Follina document.
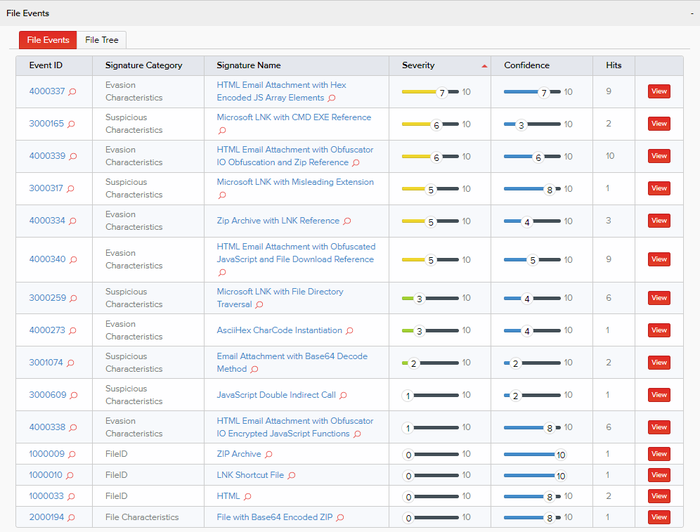
Figure 3. Variety of signatures alerts. Source: InQuest
Another interesting approach for detection is the concept of retrospective analysis or RetroHunting. While DFI creates a new dimension of data, RetroHunting provides a new dimension of time for analyzing historical events. The appearance of Follina and other zero-day vulnerabilities illustrates the usefulness of this capability by facilitating the detection of previously unseen alerts with emerging threat intelligence and detection logic.
In addition to a library of predeveloped signatures, analysts can develop user-defined YARA rules to combine strings, bytes patterns, and regular expressions via flexible conditional logic.
When confronted with novel attack techniques being encountered in the wild, security leaders must provide an opportunity to empower your detection operations and overcome the limitations inherent with other malware prevention solutions. A free resource to test the efficacy of a mail provider's security controls is the Email Security Assessment.
About the Author

Josiah Smith has almost a decade of experience in the realm of security. Before becoming a threat engineer, Josiah worked as a cyber operator, overseeing signature management and host-based detection programs. He spent several years in a room without windows, focusing on network detection, threat hunting, and IR investigations. He began his career as a member of the US Air Force, and most of his experience is with the DoD.
You May Also Like


