Phishing for Your Information: How Phishers Bait Their Hooks
A treasure trove of PII from social networks and the public Internet is there for the taking.
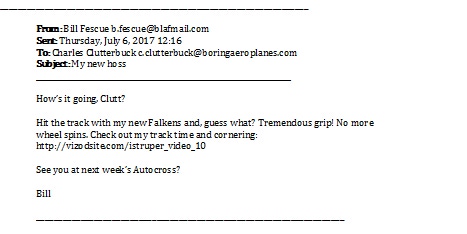
Seven minutes until his next meeting, Charles Clutterbuck, the CFO of Boring Aeroplanes, had just enough time to answer a few emails. A dozen emails glowed unread at the top of his inbox stack. He skimmed down the list of names and subjects when one caught his eye. It was from an old friend. With a nod, he clicked it up. "How’s it going, Clutt?" the email began. He smiled at the old nickname from the dorm days when he first met Bill. Funny that Bill was emailing him at his work address, but that question was quickly forgotten as he skimmed the message.
As you might have guessed, this is a spear phishing email. In spear phishing, the attacker leverages gathered information to create a specific request to trick someone into running something or giving up personal information. It’s an extremely successful technique and attackers know this. In fact, the Anti-Phishing Working Group (APWG) reports that phishing has gone up 5,753% over the past 12 years.Phishers work by impersonating someone trusted by the target, which requires crafting a message that is credible and easily acceptable. To do this, the phisher needs information about the target to construct their disguise and bait the hook. They get this information by research and reconnaissance.
In the example above, an executive at a military plane parts supplier received an email apparently from a friend. His interest in car racing—as well as his friend’s name and style of speaking—was plucked off social media. The attacker spent a few minutes of web research on car racing to get the vernacular right, and then created an email account in the friend’s name. The link is to a site with a video server that sends an exploit geared to the target’s laptop operating system (gleaned from research on the company infrastructure). It loads specialized malware built to exfiltrate aerospace intellectual property. Easy, peasy.
So, we know that attackers are gathering information from social networks and various Internet sources, but just how much information is available? It’s worth exploring what's typically discovered in an attacker’s passive electronic reconnaissance. And, that’s not counting active recon like calling the company’s main phone number and trying to extract information via pretexting or going onsite for dumpster diving. This is all low-risk stuff that can happen in secret from afar.
Scouting an organization
Since spear phishers go after a specific organization, they need to know who works there before they can begin their targeting. A lot of people tag themselves on various social media sites as an employee of a particular company. LinkedIn is a site that provides lots of details on where people work. Quora is another site where tech people congregate:
Through these sites, it’s not hard for phishers to gather up a list of names of employees at a specific organization.
Social Media and Personal Information
Social media companies expend tremendous effort to encourage people to join and post information about themselves. Some valuable bits of information that attackers can use are:
Work history
Education information (college and high school attended)
Family and relationship information
Comments on links
Dates of important life events
Places visited
Favorite sites, movies, TV shows, books, quotes, etc.
Photographs
Profiling
All these pieces of information provide powerful leverage points for attackers, but they also provide a lot of valuable indirect information. Attackers can observe the writing style of the people they want to impersonate. They can also create detailed psychological profiles of victims. There are many tools and techniques available to do things like:
Analyze sentiment to determine people’s opinions and political leanings.
Analyze posting times to determine when people are awake (and asleep) and their home time zones.
Determine an individual’s personality type, which can inform manipulation techniques.
Analyze relationships and friendship ties.
With sites like Facebook that host nearly 2 billion users, it’s very easy to craft a Google search for someone with [name] [location] site:facebook.com” to find their page.
Many social media users are part of interest groups, which can provide useful leverage points for a phisher. Even when someone sets their social media profile to “private,” it’s still not too difficult for an attacker to break in and get what they want. There are many hacking services advertised on Darknets for just that purpose:
People Search Engines
In addition to social media sites, there are numerous "people search" sites like Pipl, Spokeo, and ZabaSearch. Many of these sites pull together profiles based on dozens of resources. Sometimes they’re not very helpful, like this example for me, because I’m a paranoid security guy:
Image Source: F5
However, different sites can dig up some interesting data, like this example:

Note how this site provides Facebook information, email address, annual income, education, phone number, age range, and even racial profiling. Here’s some typical information you can get from these kinds of sites:
Home address
Mobile phone number
Home (landline) phone number
Age
Salary range
Spouse and family
Email address, which leads to possible usernames
Middle name
Maiden name
Most employees don’t think about things like this—because most employees don’t think like bad guys. It doesn’t occur to them how much personal and work-related information they are freely volunteering on various websites — or how easy they make it for phishers to pull information together into some pretty comprehensive professional dossiers. The lesson here is think before you volunteer information about yourself and your work, and limit the number of websites where you do this.
Get the latest application threat intelligence from F5 Labs.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




