DNS Is Still the Achilles Heel of the Internet
The Domain Name Systems is too important to do without, so we better make sure it's reliable and incorruptible
The Domain Name System (DNS) is too important to do without, but it's difficult to defend. This makes DNS services an excellent target for attack. Taking out an organization’s DNS service renders it unreachable to the rest of the world except by IP address. If "f5.com" failed to be published online, every single Internet site and service we ran would be invisible. This means Web servers, VPNs, mail services — everything.
Even worse, if hackers could change the DNS records, they could then redirect everyone to sites they controlled. Since DNS is built upon cooperation between millions of servers and clients over insecure and unreliable protocols, it is uniquely vulnerable to disruption, subversion, and hijacking. Here’s a quick rundown of the known major DNS attacks.
Denial of Service
Denial-of-service attacks are not limited to DNS, but taking out DNS decapitates an organization. Why bother flooding thousands of web sites when killing a single service does it all for you? The most famous DoS attack against DNS are the recent Dyn DDoS attacks which exceeded 40 gigabytes of noise blared at their DNS services. Dyn was running DNS services for many major organizations, so when they were drowned by a flood of illegitmate packets, so were companies like Amazon, Reddit, FiveThirtyEight, and Visa.
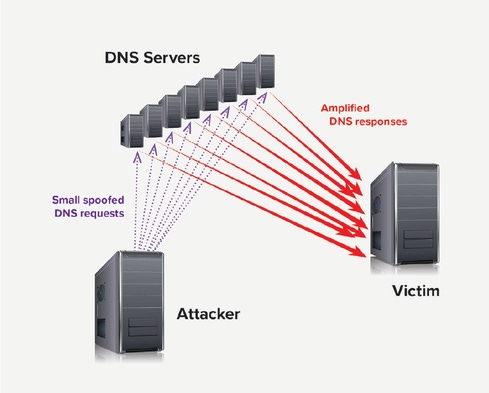
DNS can also be subverted for use as a denial-of-service weapon against other sites by way of DNS Amplification/Reflection. This works because DNS almost always returns a larger set of data than what it was queried. Since DNS runs over UDP, it’s a simple matter for attackers to craft fake packets spoofing a query source, so if they can fake thousands of queries from the victim’s IP address whose amplified responses will overwhelm the victim.
DNS Hijacking
Who owns what domain name, and what DNS servers are designated to answer queries are both managed by Domain Registrars. These are commercial services, such as GoDaddy, eNom, and Network Solutions Inc., where there are registered accounts controlling pointers to DNS servers. If attackers can hack those accounts, they can repoint a domain to a DNS server they control. This is how a Brazilian Internet banking site was completely taken over for hours.
DNS Server Vulnerabilities
Because DNS services are software, they can contain bugs that attackers can exploit. Luckily, DNS is old (so we’ve had time to find most of the bugs) and simple (so bugs are easy to spot), but problems have cropped up. In 2015, there was a rather significant hole found in BIND, an open-source DNS server running much of the Internet. Called CVE-2015-5477 (no cute name, thank you), BIND allowed an attacker to crash a DNS server with a single crafted query.
Another software vulnerability in DNS servers is the recursive DNS spoof cache poisoning technique, which means that an attacker can temporarily change DNS database entries by issuing specifically crafted queries.
Unauthorized DNS Changes
If you’ve got a server, someone must manage it. That means that you are dependent on how strongly you are authenticating the admins to that server, as well as ensuring the trustworthiness and competence of those admins. Because of the nature of DNS records, changes to DNS are cached by query clients; bad entries can sometimes take hours or days to unwind across the Internet.
DNS Data Leakage
You can’t run an unauthenticated Internet database full of important information without the occasional risk of leaking out something important. Attackers will query DNS servers looking for interesting Internet services that may not be widely known. DNS records can also aid phishing expeditions by using known server names in their phony baloney emails.
Many organizations run DNS on the inside of the network, advertising local resources for workstations. Some smaller organizations run split-horizon DNS servers that both DNS services to the world, as well as the inside network. A wrong configuration on that DNS server can lead to some devastating DNS data leakages as internal names and addresses are shared with attackers.
DNS Man-in-the-Middle
The easily spoofed protocol UDP that DNS uses is a weak link. An attacker inline between the victim and the DNS server they’re querying can intercept and monkey with DNS queries. It’s a pretty easy attack to pull off if you’re on the same wire or wireless as the victim or DNS server. An F5 researcher found a way to use it to steal Microsoft Outlook credentials. So, it’s an attack that shouldn’t be taken lightly.
Bottom line: We are stuck with DNS, so better make sure it’s reliable and incorruptible. The future of the Internet depends on it.
Get the latest application threat intelligence from F5 Labs.
About the Author(s)
You May Also Like
Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




