Architecting XDR to Save Money and Your SOC's Sanity
XDR can lower platform costs and improve detection, but it requires committing to a few principles that go against the established way of thinking about SOC.
July 3, 2023

The cyber security operation center (SOC) model's focus has shifted to extended detection and response (XDR). Architected correctly, XDR puts less pressure and cost on the security information and event management (SIEM) system to correlate complex security alerts. It also does a better job as a single pane of glass for ticketing, alerting, and orchestrating automation and response.
XDR is a real opportunity to lower platform costs and improve detection, but it requires committing to a few principles that go against the established way of thinking about SOCs.
Intelligent Data Pipelines and Data Lakes Are a Necessity
Takeaway: A security data pipeline can remove log waste prior to storage and route logs to the most appropriate location.
Managing your security data pipeline intelligently can have a massive impact on controlling spending by preprocessing every log and eliminating excess waste, especially when your primary cost driver is GB per day. Consider the following example showing the before and after size of Windows Active Directory (AD) logs.
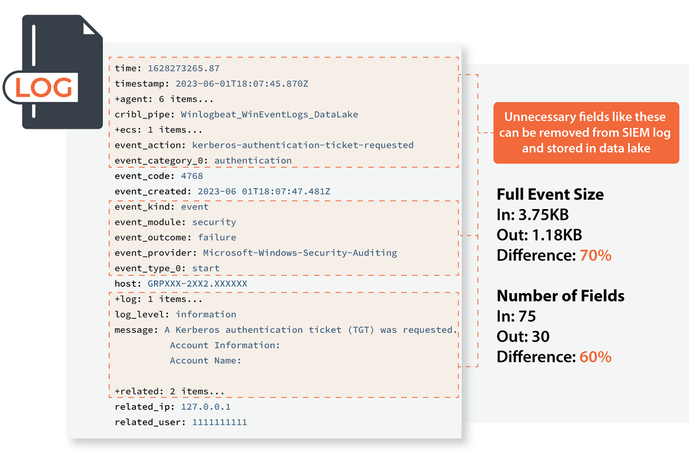
The average inbound event had 75 fields and a size of 3.75KB. After removing redundant and unnecessary fields, the log has 30 fields and a size of 1.18KB. That is a 68.48% reduction of SIEM storage cost.
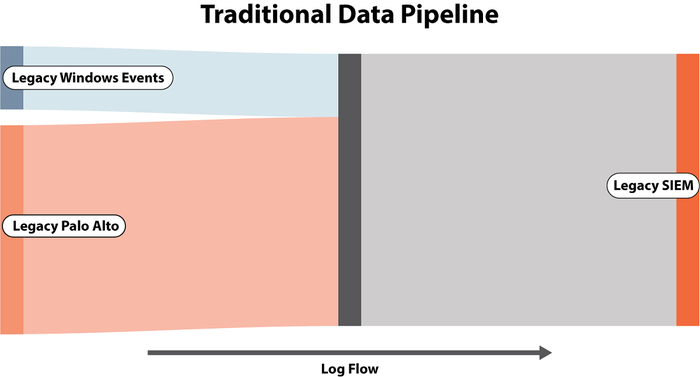
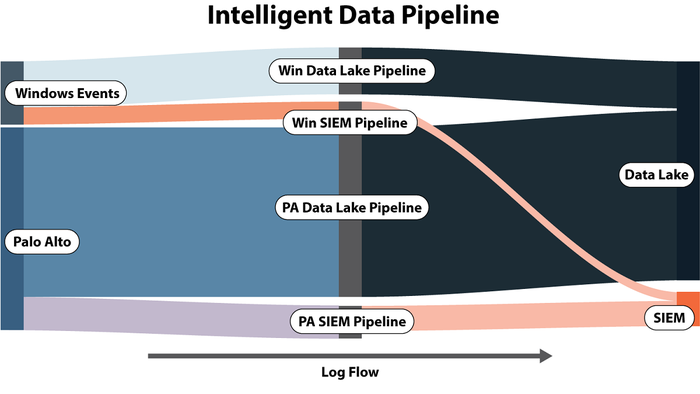
Applying similar value analysis for where you send each log is equally important. Not all logs should be sent to the SIEM! Only logs that drive a known detection should be sent to SIEM. All others used in supporting investigations, enrichment, and threat hunting should go to the security data lake. An intelligent data pipeline can make on-the-fly routing decisions for each log and further reduce your costs.
Focus Detection and Prevention Closest to the Threat
Takeaway: Product-native detections have gotten dramatically better; the SIEM should be a last line of defense.
The SIEM used to be one of the only tools that could correlate and analyze raw logs and identify alerts that need to be addressed. This was largely a reflection of other tools being single-purpose and generally bad at identifying issues by themselves. As a result, it made sense to ship everything to the SIEM and create complex correlation rules to sort the signal from the noise.
Today's landscape has changed with endpoint detection and response (EDR) tools. Modern EDR is essentially SIEM on the endpoint. It has the same capabilities to write detection rules on endpoints as the SIEM has, but now there is no need to ship every bit of telemetry data into the SIEM.
EDR vendors have gotten markedly better at building and maintaining out-of-the-box detections. We have consistently seen a sizable decrease in detections and preventions attributed to the SIEM during our purple team engagements in favor of tools like EDR and next-generation firewalls (NGFW). There are exceptions like Kerberoasting (which on-premises AD doesn't have much coverage for). As you move to pure cloud for AD, even those types of detections will be handled by "edge" tools like Microsoft Defender for Endpoint.
Play to Your SIEM Strong Suit
Takeaway: Having a deliberate process to consistently measure and improve your detection capabilities is far more valuable than having any specific SIEM tool on the market.
Purple teaming across industries and detection ecosystems has allowed us to understand the efficacy of many modern EDR, NGFW, SIEM, and other tools. We score and benchmark purple team results and trend the improvements over time. We have found over the past five years that the SIEM you buy has no measurable correlation to purple team scores. Process, tuning, and testing are what matter.
SIEM tools have architectural differences that can make one a better or worse fit for your environment, but buying a specific SIEM to significantly improve your detection capabilities will not prove out. Instead, focus your efforts on dashboards and correlations that support threat-hunt and incident-response efforts.
Align EDR, SIEM, and SOAR in Your XDR Architecture
Takeaway: Security automation and artificial intelligence (AI)-enhanced triage is the future but should be approached with caution. Not all automation needs to exclude all human involvement.
The future of XDR is coupled with tightly integrated security orchestration, automation, and response (SOAR) technologies. XDR concepts recognize that what really matters is not how fast you can detect a threat, but how fast you can neutralize a threat. "If this – then that" SOAR automation methodologies aren't effective in real-world scenarios. One of the best approaches we've seen in XDR automation is:
Conduct a purple team exercise to identify which current detection events are optimized (very low false positive rates) and can be trusted with an automated response.
Create an automated response playbook but insert human intervention steps to gain confidence before you turn it fully over to automation. We call this "semi-automation," and it's a smart first step.
XDR is a buzzword, but when viewed in a technology-agnostic fashion, it is based on good foundations. Where organizations are most likely to fail is applying legacy SIEM management philosophies to modern XDR architectures. These program design philosophies will likely improve your capabilities and reduce your costs.
About the Author

Mike Pinch joined Security Risk Advisors in 2018 after serving 6 years as the Chief Information Security Officer at the University of Rochester Medical Center. Mike is nationally recognized as a leader in the field of cybersecurity, has spoken at conferences including HITRUST, H-ISAC, and has contributed to national standards for health care and public health sector cybersecurity frameworks. Mike focuses on GCP, AWS, and Azure security, primarily in helping SOC teams improve their capabilities. Mike is an active developer and is currently enjoying weaving modern AI technologies into common cybersecurity challenges.
You May Also Like
Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


