Passwords Use Alone Still Trumps Multi-Factor Authentication
Strong authentication use overall remains weak but is starting to gain some ground with enterprises.

Corporate America's use of passwords remains prevalent, but multi-factor authentication is showing some signs of growth in the enterprise, according to a new report.
Javelin Strategy & Research's 2017 State of Authentication Report, which surveyed 400 IT security decision makers and influencers of purchases, found that 100% of enterprises continue to use passwords, despite industry calls to ditch them all together or at least bolster security through a combination of passwords and other measures, such as biometrics and PKI.
The survey, commissioned by the FIDO Alliance, also found that half of companies used multi-factor authentication for their customers, but only 35% do so for their employees.
And when it comes to strong authentication, which is characterized by using public key cryptography as one of the forms of authentication, the percentage of companies using this form of security for both customers and employees plummets to only 5% in each case.
"I wasn't surprised by the results, but am disappointed," says Al Pascual, Javelin's senior vice president and research director.
The IT sector led the use of high-assurance strong authentication 9%, followed by the retail and hospitality services industries at 3%, the report states.
A number of small providers in the healthcare and finance industries, which likely do not have the financial resources to deploy PKI security, are stuck using security that calls for a single password, Pascual notes.
The Problem
With so many companies relying on a single factor, passwords, to secure their operations, employees and customers, it potentially sets the stage for a company's IP and financial data to get pilfered, Pascual notes.
"First and foremost, as individuals, we have bad password hygiene. We use the same passwords at home as we do for work and the bad guys know this," he says.
Indeed, the Pew Research Center earlier this year released a report that found 39% of its survey respondents used the same password, or a similar one, for a number of their online accounts.
With mass compromises of passwords occurring across a number of companies from Cupid Media's breach of 42 million passwords to Dropbox's massive compromise of 68 million passwords, it may not be surprising to find that Javelin's survey also found that a third of US companies have had customer information breached.
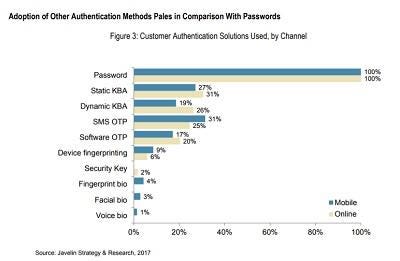
According to the Javelin report, not only are passwords a troubling issue but teaming them with knowledge-based factors for multi-factor authentication may not be much better. Static questions and SMS OTPs, which are among the weakest authentication factors, are also the most popular and pervasive, with 31% of survey respondents noting their organizations use them and 25% for SMS OTPs, the survey found.
"Passwords, static questions, and SMS one-time passwords can evaluate if the data is right or wrong but can't dynamically verify who the person behind the device really is," says Lisa Baergen, marketing director of NuData Security, a Mastercard company.
When it comes to targets, cybercriminals are focusing on financial data in 46% of the breaches reported in the survey, while in 44% of the cases, a company's intellectual property was involved, according to the report.
Companies are apparently resistant to using multi-factor authentication systems: When considering buying new employee authentication systems, 36% of respondents cite potential integration challenges as one of the main considerations, while 36% cite industry standard certifications as high on the list, according to the report.
The concern over integrating multi-factor authentication systems is real, says Pascual, who notes he has seen this with his own clients. Concerns over integrating four, five, or six disparate solutions that may operate on different platforms, is one issue they face, he says.
FIDO
Meantime, the FIDO Alliance standards are aimed at bringing strong authentication to users that have access to sensitive information and to eliminate reliance on passwords, says Michael Magrath, director of global regulations and standards for VASCO, and a FIDO Alliance board member.
"Authenticators built on FIDO standards as well as new frictionless technologies, such as behavioral biometrics and facial recognition, will help bring strong authentication to consumers," says Magrath.
The Javelin report says possession factors are a better multi-factor authentication solution than knowledge factors for multi-factor authentication. Mobile devices with fingerprint scanning, voice recognition, and other inherence-based authentication also offer a way to conduct possession-based authentication.
Pascual expects the adoption of high-assurance strong authentication will increase in the coming months and years. "I expect adoption to accelerate," he says. "It may not be in the double digits, but it will be significant growth."
Related Content:

Join Dark Reading LIVE for two days of practical cyber defense discussions. Learn from the industry’s most knowledgeable IT security experts. Check out the INsecurity agenda here.
About the Author
You May Also Like
Cybersecurity Day: How to Automate Security Analytics with AI and ML
Dec 17, 2024The Dirt on ROT Data
Dec 18, 2024




