5G Network Security Needs a Comprehensive Approach in 2019
As the first 5G rollouts are anticipated to start in 2019, service providers need to take a more holistic and comprehensive approach to securing these new networks and the businesses and customers using them.

As rollouts of 5G networks get underway in 2019, the technology will affect three very diverse areas: enhanced mobile broadband for consumers; massive machine-type communications for billions of Internet of Things devices and systems; and ultra-reliable, low latency communications for mission-critical applications.
Within these three areas, the range and effect of possible security threats is wide: from a breakdown of communications and massive service outages, to unauthorized access of sensitive and private data.
All of these can lead businesses to losses and worse -- putting people's lives and property at risk.
Major standards organizations, including 3GPP and ITU, view 5G security in a holistic manner, with frameworks encompassing all aspects. One vital element of the 5G security architecture is the transport network domain. With more infrastructure owners and increased complexity of trust relationships, this network needs more comprehensive security.
Network slicing will effectively multiply these concerns across many individual slices.

(Source: iStock)
A proper 5G transport domain security approach must protect the network infrastructure and ensure confidentiality, integrity and availability of communications flows across all network planes: user, control, data and management planes.
These approaches must also support diverse mobile generations that will continue to coexist and many distributed, hybrid -- virtualized and physical -- domains that need to be dynamically interconnected.
For service providers who lease their transport from wholesale providers, protecting traffic between the radio access network (RAN), the core network and their multi-cloud environment becomes even more vital.
Security gateways to the rescueHistorically, security of transport in mobile environments has been effectively addressed by deploying high-end routers at centralized locations as security gateways (SeGWs).
This approach ensures:
Authentication: Affirmation that communication elements are truly who they claim they are
Integrity and confidentiality of communications: By encrypting communications flows in an end-to-end (or in a more precise, point-to-point) manner using the highest cryptographic standards available
Internet Protocol Security (IPsec) has been used extensively to protect all communications between the RAN and core.
In the RAN, encrypted sessions start at RAN base stations or nearby cell/aggregation routers. At the centralized location, these encrypted sessions are terminated by a large-scale IP router: a dedicated SeGW, which also provides all required interconnectivity.
In this chart, the solution based on SeGWs can also work in 5G to address all types of RAN base stations: macrocells, small cells, and fixed-wireless access. Non-3GPP access -- carrier WiFi -- can be integrated to the 5G core in a similar manner through Non-3GPP Interworking Function (N3IWF).
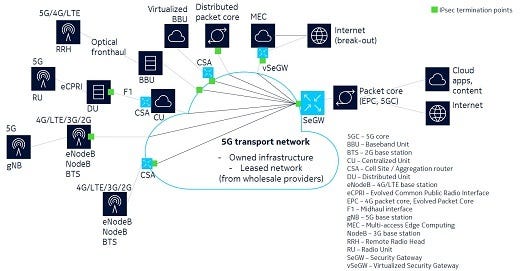
\r\n(Source: Nokia)\r\n\r\n
The deployment of SeGWs is done in conjunction with Public Key Infrastructure Certification Authority (PKI CA) -- a software-based system that ensures the authentication of access elements, provides for authorized and secure exchange of encryption keys, and manages the whole solution from a security viewpoint.
5G specification also brings a new authentication scheme and opens the scope of research to monitor developments in quantum cryptography. (See How Quantum Physics Will Protect Against Quantum-Busting Encryption.)
It's important to add that security has also become a consideration at the optical transport level, resulting in Layer 1 encryption techniques as part of an overall defense-in-depth strategy.
New generation of transportReal-time encryption of communications flows add a "processing tax" in the form of reduced throughput (lower than line rate) and increased end-to-end latency. This may not pose a great challenge for broadband services, where high speed is generally much more important than low latency -- such as video streaming. However, to "qualify" for the 5G era, SeGWs need to ensure low latency for services where it's critical (such as uRLLC) or an essential part of a user experience, for example, gaming. They also need to support distributed architectures and hybrid deployment.
The progress made with the latest generation of routers -- from the underlying processors with extreme processing power and intelligence, to new product architectures and high-density, high-speed interface cards -- allows SeGWs to:
Handle large number of IPsec sessions (hundreds of thousands per system)
Achieve high-aggregate throughput rates (up to hundreds of Gbps per system)
Add very little latency
In addition, great progress has been made with virtualized implementations (vSeGW), running in x86 environments.
However, not all vendor implementations are the same, and interoperability test results -- where they exist -- are not shared publicly.
Where does this leave you?Service providers transitioning to 5G should include 5G transport domain security in their overall 5G tests and trials.
Security of the transport network, like overall 5G security, should be a forethought, not an afterthought. The stakes are much higher in 5G, and only a 5G transport network that can address all 5G requirements -- including security -- will safely take you into the 5G era.
Related posts:
— Alex Pavlovic is a senior product marketing manager for IP and Optical Networks at Nokia, where he focuses on Nokia Anyhaul -- the mobile transport portfolio for the 5G era (and Nokia IP Anyhaul in particular).
Read more about:
Security NowAbout the Author
You May Also Like




