We as an industry must demand greater protection of our medical data.
October 27, 2016

My Twitter timeline informed me of yet another company suffering from a data breach -- this one only 43 million records. The reaction was limited to a collective shrug, just like we saw when news of the massive Yahoo breach came to light. While the security community analyzes and deliberates over the details behind each breach, the reality is that affected consumers and society in general care more about the major deaths in season 7 of the “Walking Dead.”
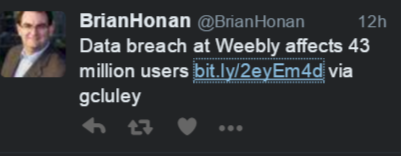
Sometimes, consumers do care. When a breach impacts day-to-day activities, they care. After the Target breach, for example, it was reported that credit card companies implemented additional fraud activity checks that resulted in false positives. Subsequently, holiday shoppers found that in some cases legitimate transactions were blocked, all of which were “pretty annoying.” Although we see headlines associated with breaches concerning payment cards and a tepid response from affected users, identity thieves have pulled off heists at 10 times the scale of credit card fraud by going after medical and tax records. Such data sets are becoming increasingly valuable, and there is little awareness.
Our threat research report The Hidden Data Economy highlights the value criminals place on data about us. However, what’s missing in this report is research on stolen medical data. That prompted questions about whether underground marketplaces exist for medical data, and if they do, what is the value of that data. We researched these questions and presented our findings in the just published report Health Warning: Cyberattacks Are Targeting the Healthcare Industry. We were able to confirm that the healthcare sector is being targeted and that the stolen data indeed has value.
We did not have to look very hard to find a robust market for stolen healthcare data. Almost immediately, we were offered huge data sets from the healthcare sector.
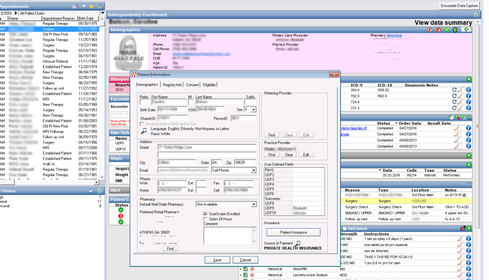
As we delved deeper, we even saw details of the ecosystem that resulted in such breaches. One particular individual detailed how they had purchased an exploit that gave them access to a database within the healthcare sector.
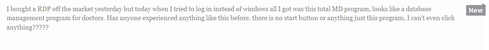
What followed the preceding dialog was a discussion about pricing and a congratulatory message to the cybercriminal that they were in the money. Such interactions demonstrate the vulnerabilities of the healthcare sector, but moreover the value that criminals place in stolen medical data.
Attacks are not limited to healthcare organizations. A recent Federal Times article highlighted that the US Food and Drug Administration was also targeted. The Federal Times article “Why Hack the FDA” stated that “the FDA reported 1,036 security incidents between January 2013 and June 2015.”
These reports demonstrate that bubbling under the sea of stories of megabreaches is the fact that medical data is both targeted and valued by criminals looking to make money from our misfortune. Medical data is not perishable, so unlike payment cards, thieves do not need to worry about validity rates.
We have no desire to spread fear about the state of the “Second Economy,” but the level of apathy is allowing almost free rein to criminals who compromise organizations for their own greed. We must demand greater protection for our medical data.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




