
Enterprise cybersecurity technology research that connects the dots.
Best Practices for Enterprise Private 5G Security
Omdia's latest research with Trend Micro and CTOne sheds light on 5G security challenges and ways to effectively extend enterprise-grade security to 5G networks

Private 5G is becoming a key asset for enterprises as it addresses common challenges across industry verticals. Omdia's latest research, in partnership with Trend Micro and CTOne, involved a survey of 150 organizations and 150 service providers around 5G networks and their strategies for securing them. In our survey, the top reasons that organizations give for deploying 5G are to obtain faster operations, handle a greater number of connected devices, and lower operational costs.
Compared with previous iterations of mobile protocols, 5G has an increased security focus — and organizations are keen to benefit from this. That said, there still remains some awareness and education to distinguish the limitations of 5G's "security by design" approach, and where organizations need to be implementing additional security for their 5G networks. Omdia's "Beyond Secure by Default" whitepaper, sponsored by Trend Micro and CTOne, details what companies need to know about enterprise private 5G security, including the following best practices.
Understanding the Limitations of 5G Network Security
One of the key aspects to consider when deploying a private 5G network is that organizations may be expecting a secure network by default, but there is still much to be done by the organization. In terms of the network itself, there have been numerous enhancements compared with what previous cellular networks could offer — predominantly authentication, access control, and encryption. Still, this isn't to say that therefore a 5G network is "just secure." There needs to be additional consideration across people, processes, and technology for an extension of enterprise-grade security — notably, when factoring in new endpoints such as IoT devices and mission-critical requirements. Omdia's survey shows that many organizations are aware of these additional requirements. Organization's leaders most commonly selected security visibility, risk control management, and streamlined alerting as their top requirements.
Determining Responsibility
It's clear there is a shared responsibility in 5G networks, and this isn't going to be the same for every organization. 5G networks are likely to be deployed in different ways, as depicted in the figure below. No matter the deployment model, the enterprise will likely be working with service providers and system integrators at some point throughout their journey, whether that be planning, deployment, or operation.
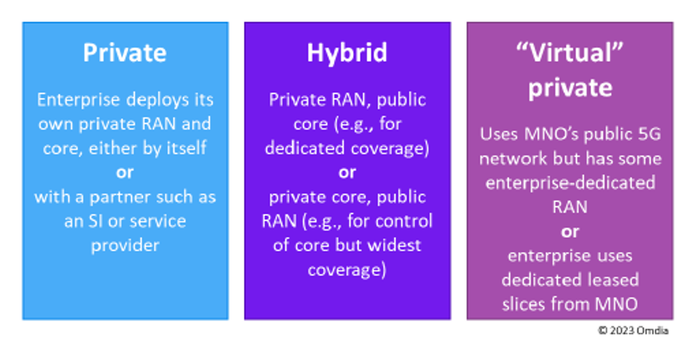
Source: Omdia
Therefore, it's vital that each organization understands and sets clear responsibility throughout these stages. Our research suggests most enterprises expect to manage the planning, deploying, and operating of the 5G private network core, IoT devices, and the data network — and will turn to a service provider and supplier for management of radio access network (RAN) and multi-access edge compute (MEC) elements. Although this will vary on a case-by-case basis, this shows that a security solution will have to factor in this shared responsibility. While the enterprise may not be directly responsible for securing the RAN and MEC, as in this example, they will still need to ensure that their partner is providing them with a secure product and service.
Looking to New, Integrated, Security Measures
When asked how enterprise 5G network security is to be integrated with existing security measures, most organizations (60%) believe that it will require new measures, and that it will need to be fully integrated with existing tools and services. Integration is key here because the complexity of 5G already poses a large challenge for organizations from a management and skills point of view — leaving room for misconfiguration and underutilized technology, which can act as a hindrance to cybersecurity.
Other respondents to the survey expect to run new 5G security measures separately (15%) or handle 5G security with existing tools and services (25%). Existing tools and services can apply to 5G networks in some instances, such as Web application firewalls, workload protection, and endpoint detection and response. Many principles of IT security cross into the communication technology side, and existing services providers may be able to support organizations across these technologies. However, there are nuances with 5G that will need special attention, whether that be a need for more granular visibility into all aspects of a cellular network, the volume of devices connected and their security management, threats related to the subscriber identity module (SIM), air interface vulnerabilities, or even physical tampering with RAN equipment.
Considering the Entire Landscape
Organizations must be prepared to have an accurate picture of their 5G network alongside other technologies — especially OT and IoT, which are likely to intersect. This means extending visibility and monitoring across IT, communications technology (CT), devices, infrastructure, and networks, and then applying proactive protection, detection, and response.
The Internet of Things is a good example here; there is likely to be a much higher volume of these devices connected to the network, with 61% of organizations telling us they are deploying 5G due to a greater number of connected IoT devices. These devices usually are not hardened, and they often have security vulnerabilities. It is not just the device itself that an organization will need to be concerned with, but communication, data, applications, and so on. Organizations will need visibility into these devices and their actions, with the ability to apply granular policies to mobile devices. Devices will be authenticated to the network, but organizations will need to consider who is using the device, the processes on these devices, and how data is flowing. Given that many organizations are going to be deploying 5G across multiple sites, according to our survey, this again highlights complexity and importance of tooling and technology that can visualize this environment and its connected devices.
About the Author
You May Also Like

