SHAKEN/STIR: Finally! A Solution to Caller ID Spoofing?
The ubiquitous Caller ID hasn't changed much over the years, but the technology to exploit it has exploded. That may be about to change.
Fraud and abuse in the form of robocalling, and more specifically illegally spoofed calling, is the No. 1 consumer complaint to the Federal Communications Commission (FCC). Robocalls make up nearly half of all phone calls, so frustrated consumers simply don't answer incoming calls and businesses can't get through to customers when they need to reach them.
At the root of the problem is the ease of spoofing caller IDs. Anyone can spoof their outbound Caller ID by using an online service like Spooftel or SpoofCard. These services are meant to protect the caller's number from being displayed and claim they aren't intended for malicious purposes, but the fact that they exist indicates the breadth of the problem.
For cybersecurity professionals, Caller ID spoofing is a particularly pernicious problem. To gain the trust of their intended victim, hackers hide behind a friend, company, or institution associated with their target's information. Typically, they will find a trusted number and spoof it.
Caller identifications are determined during the second ring of a call. In this short period, spoofers use frequency shift keying to alter the binary format of the number, a process that can be automated. Current Caller ID technology was developed without any consideration that it could be used nefariously and hasn't changed much, while the technology to exploit it has exploded.
The FCC Steps in with SHAKEN and STIR
FCC chairman Ajit Pai challenged the telecommunications industry in November 2018 to adopt a caller authentication system to combat this growing nuisance or face regulatory intervention. This has spurred the telecommunications industry to develop a framework of interconnected standards called SHAKEN (Secure Handling of Asserted information using toKENs) and STIR (Secure Telephony Identity Revisited) that defines how telephone service providers should work together to ensure calling numbers have not been spoofed.
As with many secure platforms on the Internet, digital identity certificates that leverage public key infrastructure (PKI) will make it possible to verify that the Caller ID information is accurate and can be trusted. SHAKEN/STIR shifts responsibility for identity verification from the call originator to the originating telephone company routing the call. At a high level, each telephone service provider will obtain its digital certificate from a certificate authority that is trusted by other telephone service providers. The certificate technology enables the called party to verify that the calling number is accurate, as asserted by a trusted source.
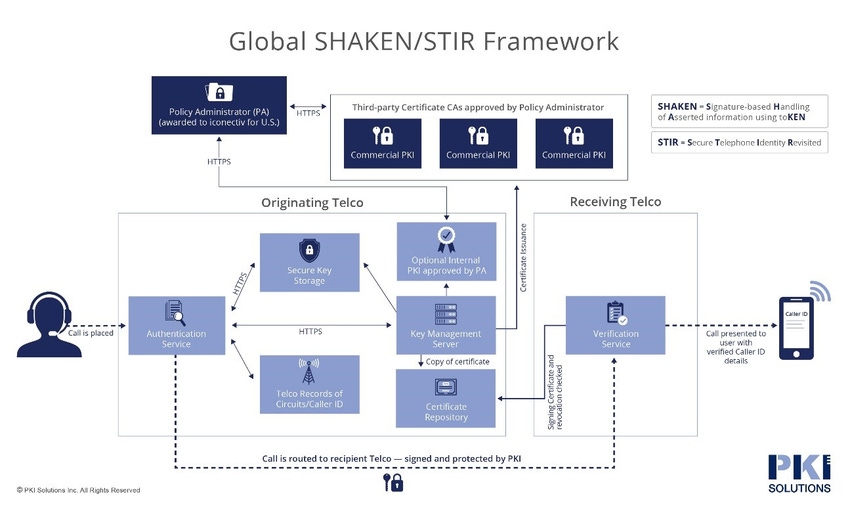
As shown in the framework diagram below, telecommunication service providers must implement a certificate management system to create and manage the public and private keys and digital certificates used to sign and verify Caller ID details. The private keys are used by the service provider to sign calls. The public key is then used by other service providers to verify that the signature was actually created by the private key associated with a trusted provider.
Also Applies to Enterprise VoIP
Although SHAKEN is a carrier-centric framework that sets out a standard way to implement STIR on the Internet Protocol-based network-to-network interface (IP-NNI), it will also affect enterprises that have their own Voice over IP (VoIP) infrastructure. In the next several years, such enterprises will be expected to set up call authentication through the SHAKEN/STIR delegation feature. Carriers can delegate authority for telephone numbers assigned to enterprises, making them a participant in the SHAKEN/STIR ecosystem.
For this ecosystem to work, the industry — technology infrastructure, telecommunications, enterprises, and government entities — needs to work together to ensure call identities are universally trusted. As this technology standard evolves and starts to be deployed, security will be required at every level of SHAKEN/STIR implementations. The players involved need to educate themselves on the many places where things can go wrong, including bad policies, lax security controls, and weak operational practices. Bad actors will absolutely try to subvert this security to initiate "validated" calls.
The telecommunications landscape is vast and diverse, with players ranging from massive corporations to virtual telcos that aggregate services and service providers serving niche clients or small geographies. For SHAKEN/STIR to accomplish its goal of re-establishing trust in the phone system, every provider will need to come up to speed on the nuances of setting up a PKI correctly.
Chances are, however, that not every provider will have the necessary expertise in-house but may decide to forge ahead on their own. When that happens, things invariably will go wrong; all it will take is one weakness in a PKI implementation for spoofers to get back in the game. As more telcos implement SHAKEN/STIR, the value on the underground of having a provider's certificate in a compromised state is significant. All of a sudden, robocallers with a validated Caller ID can start making spoofed robocalls again after everyone has started to trust Caller IDs again. There is a large financial incentive for robocallers to identify weaknesses and exploit them for financial viability.
A Long Slog Ahead
Although the FCC wants to accelerate the timeline for SHAKEN/STIR implementations across the industry, the reality is that it's going to take time. Rather than rushing ahead, a far better approach will be to invest the time and resources necessary to ensure that the system is implemented properly and highly secure. Things are moving ahead with the all-important role of Secure Telephone Identity Policy Administrator (STI-PA) being awarded to iconectiv in May 2019. In this role, iconectiv is responsible for applying and enforcing the rules defined for the SHAKEN/STIR framework.
The certificate policy will be published soon. It will lay out the rules of engagement, but without it there is significant uncertainly. Do you have to have an audit? If so, what does that audit look like? And what does it have to look at? What requirements do organizations have for security? What about availability, background screening, and training?
While these pieces are coming together, I would encourage everyone in the ecosystem to proactively line up the necessary resources and expertise to implement SHAKEN/STIR in the most secure way possible. If in-house know-how is lacking, companies should track down experts who can help get the PKI implemented correctly and address problems such as cloud vs. on-premises deployment and scalability. There's no time to waste: The integrity and trust of the telephony system depends on getting this right.
Related Content:
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "Account Fraud Harder to Detect as Criminals Move from Bots to 'Sweat Shops."
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "Account Fraud Harder to Detect as Criminals Move from Bots to 'Sweat Shops."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




